Mechanism for securing a digital lock from unauthorized use
A digital lock and lock body technology, applied in the field of digital locks, to achieve the effects of easy implementation, reliable energy consumption, and small size
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
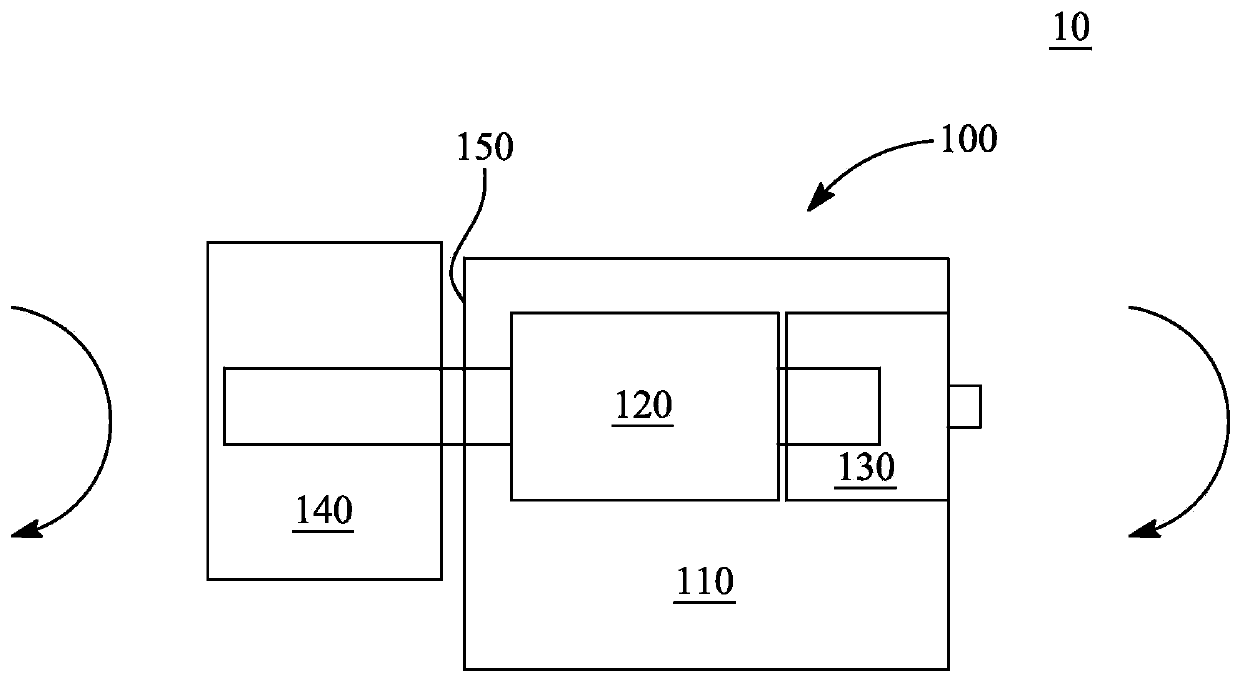
Embodiment approach 10
[0082] Any feature of embodiment 10 can be readily combined with other embodiments 20, 30, 40, 50, 51, 60, 70, 80, 90, 91, 92, 93, 94, 95, 96, 97, 98 according to the invention , 99, 101, 102, 103, 104, 105, 106, 107, 108, 109, 116, 111, 112, 113, 114, 115, 117, 118, 119, 121, 122, 123, 124 and / or 125 Any combination or permutation of them.
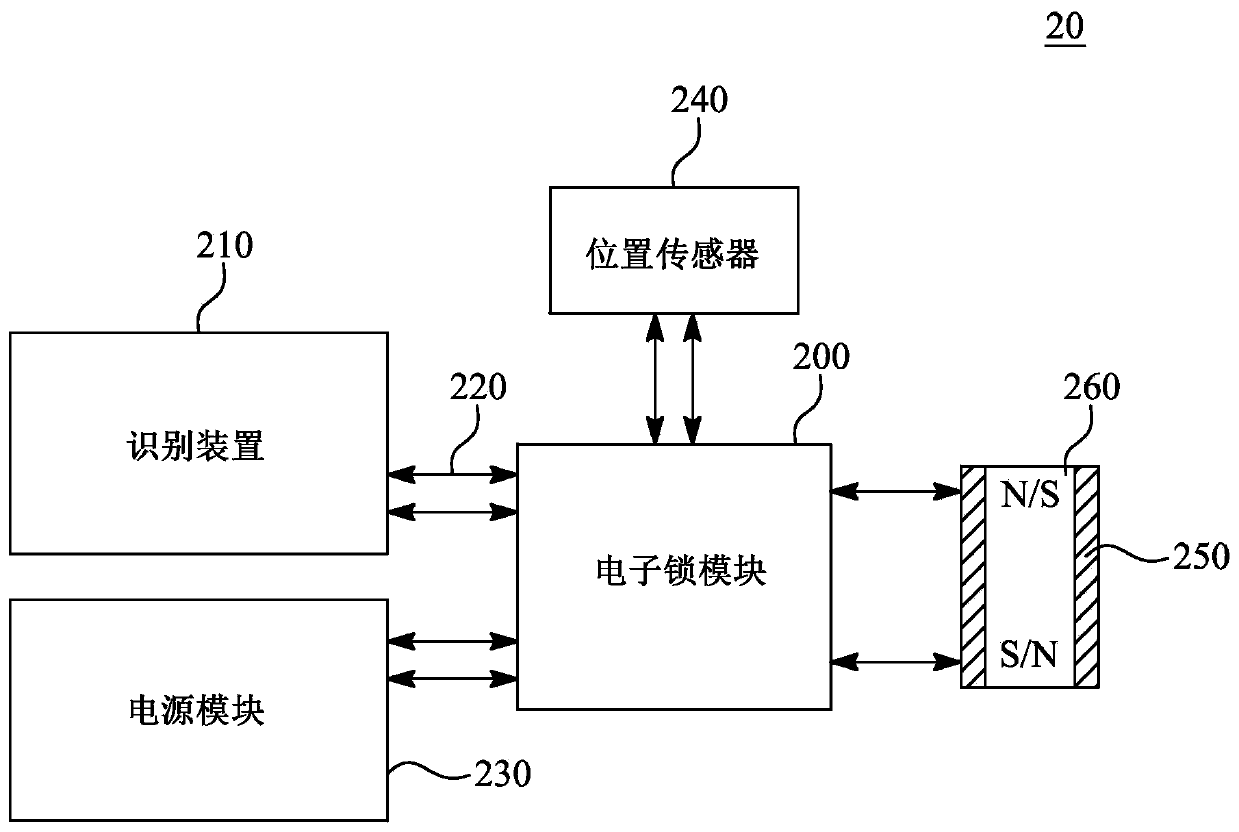
[0083] figure 2 Embodiment 20 of a digital lock 100 according to the invention is shown in a block diagram. The digital lock 100 also includes an electronic lock module 200 connected to the identification device 210 via the communication bus 220 . The communication bus 220 is configured to transmit data between the identification device 210 and the electronic lock module 200 .
[0084] The identification device 210 is configured to identify the user via any of the following: a key tag, a fingerprint, a magnetic strip and / or a near field communication (NFC) device. The identification means 210 can identify the user and allow access to...
Embodiment approach 20
[0089] Any feature of embodiment 20 may be readily combined with other embodiments 10, 30, 40, 50, 51, 60, 70, 80, 90, 91, 92, 93, 94, 95, 96, 97, 98 according to the invention , 99, 101, 102, 103, 104, 105, 106, 107, 108, 109, 116, 111, 112, 113, 114, 115, 117, 118, 119, 121, 122, 123, 124 and / or 125 Any combination or permutation of them.
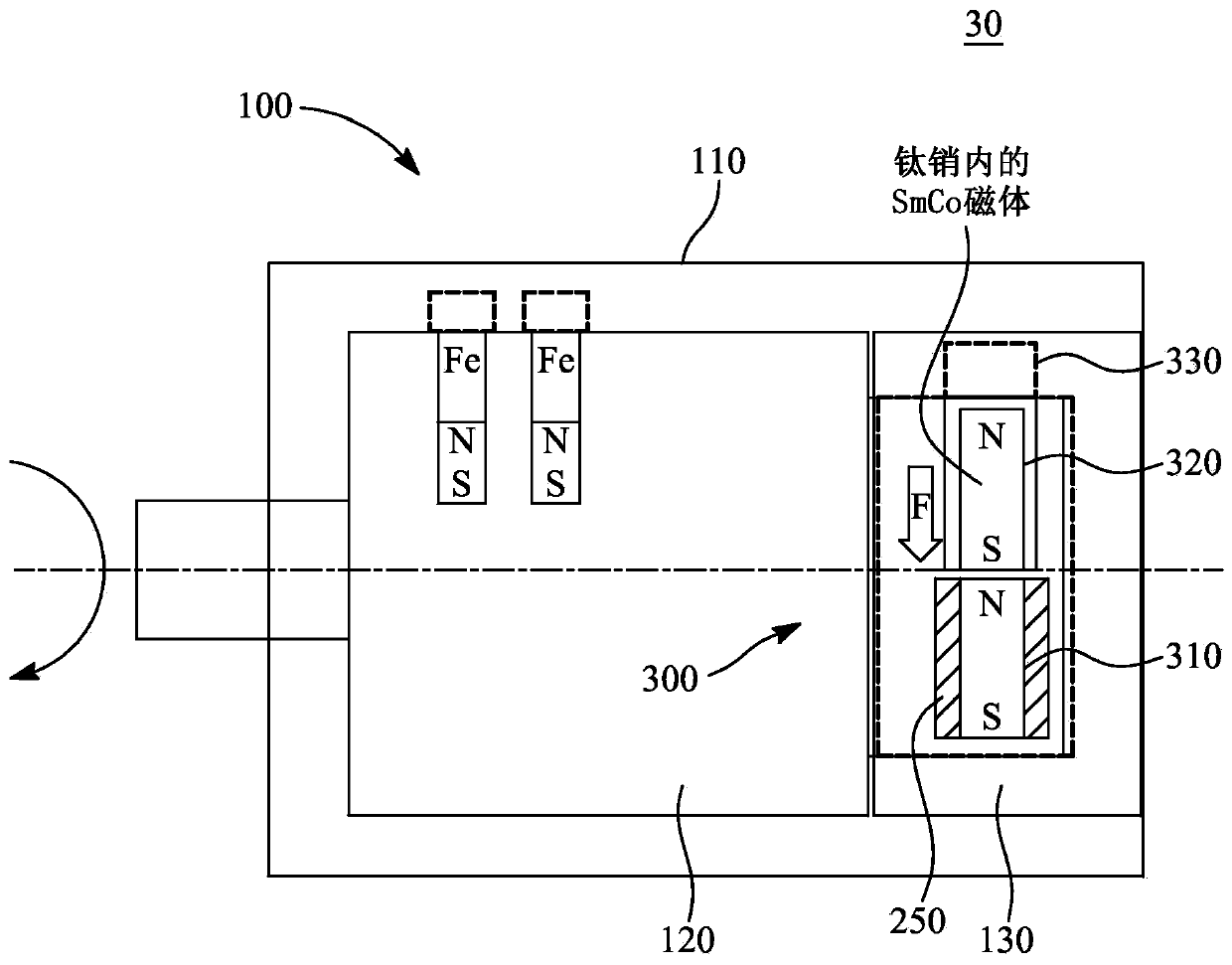
[0090] image 3 An embodiment 30 of a digital lock 100 according to the invention is shown in a block diagram in a locked state 300 . The digital lock 100 includes a semi-hard magnet 310 and a hard magnet 320 configured to open or close the digital lock 100 . Semi-hard magnet 310 is placed adjacent to hard magnet 320 . Additionally, a semi-hard magnet 310 is located within the magnetizing coil 250 . In this embodiment, the semi-hard magnet 310 is made of Alnico, and the hard magnet 320 is made of SmCo. In particular, the semi-hard magnet 310 is made of an iron alloy composed of aluminum (Al), nickel (Ni), and cobalt (Co) in addition ...
Embodiment approach 30
[0095] Any feature of embodiment 30 can be readily combined with other embodiments 10, 20, 40, 50, 51, 60, 70, 80, 90, 91, 92, 93, 94, 95, 96, 97, 98 according to the invention , 99, 101, 102, 103, 104, 105, 106, 107, 108, 109, 116, 111, 112, 113, 114, 115, 117, 118, 119, 121, 122, 123, 124 and / or 125 Any combination or permutation of them.
[0096] Figure 4 An embodiment 40 of a digital lock 100 according to the invention is shown in a block diagram in an openable state 400 . as before about image 3 As depicted, the digital lock 100 includes a semi-hard magnet 310 and a hard magnet 320 configured to open or close the digital lock 100 . The semi-hard magnet 310 is placed adjacent to the hard magnet 320 . Additionally, a semi-hard magnet 310 is located within the magnetizing coil 250 . When the polarity of the half-hard magnet 310 is changed by the magnetizing coil 250 , the half-hard magnet 310 is configured to push or pull the hard magnet 320 to open or close the digit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com