Vulnerability association mining method for industrial control system
An industrial control system and vulnerability technology, applied in the field of network security, can solve the problems of inaccurate and in-depth vulnerability threat risk assessment of industrial control systems, without considering the vulnerability correlation system, etc., so as to improve the comprehensive coverage of mining and the accurate and effective results. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
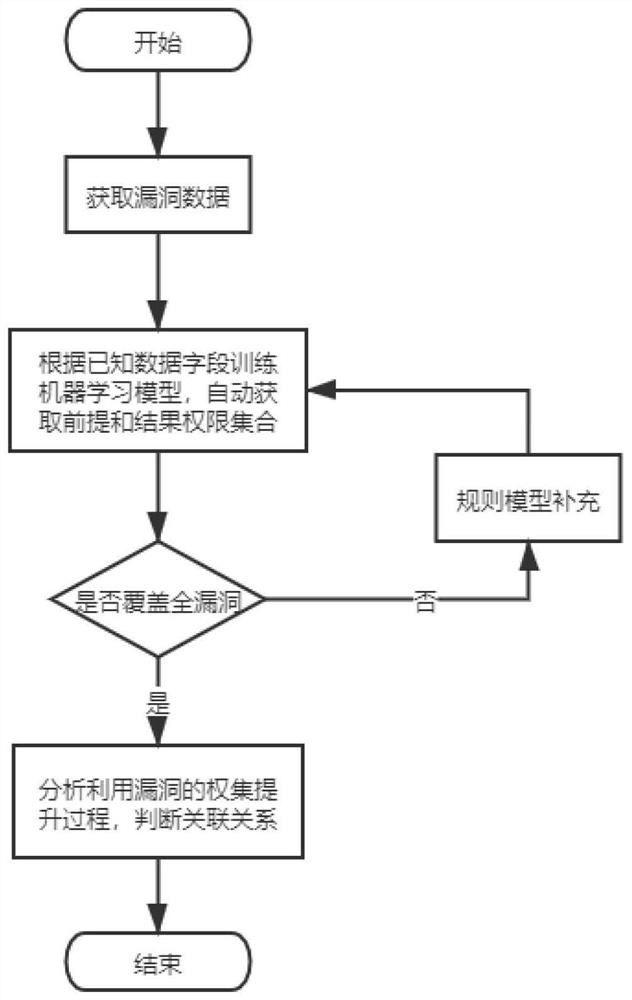
[0052] A vulnerability association mining method for industrial control systems, such as Figure 1-4 shown, including the following steps:
[0053] (1) Obtain network vulnerabilities from the National Information Security Vulnerability Sharing Platform (CNVD) and the Industrial Internet Security Emergency Response Center (ICS-CERT);
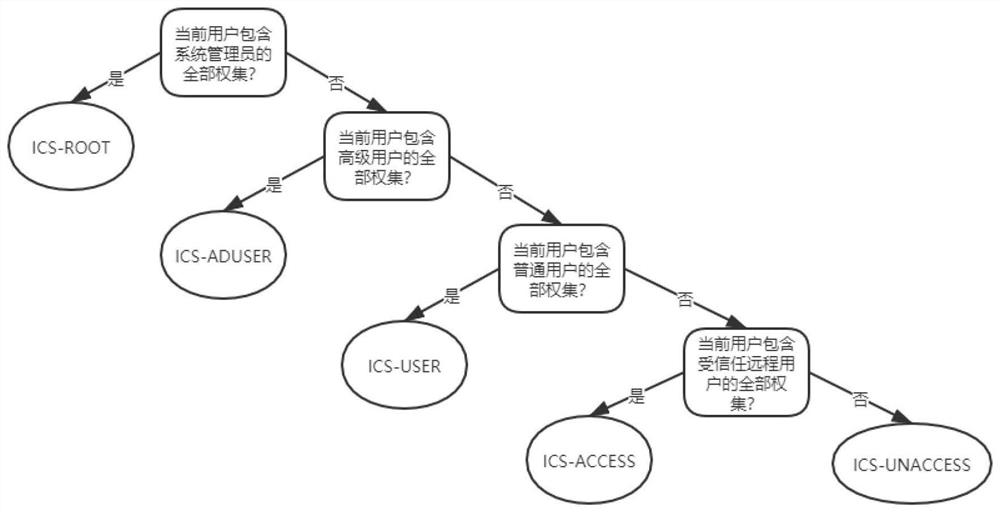
[0054] (2) Vulnerabilities are classified, and when describing the properties of the vulnerability, the premise of the permission set required to exploit a certain vulnerability and the result of the permission set that can be achieved by successfully exploiting the vulnerability are added to describe;
[0055] (3) Adopt the method of combining machine learning algorithm and rule processing to automatically generate the whole process of extracting authority collection;
[0056] (4) Carry out association analysis on the automatically obtained permission set fields contained in the description attribute, and dig out the pre-post logical relationsh...
Embodiment 2
[0059] A vulnerability association mining method for an industrial control system, as described in Embodiment 1, the difference is that step (2) is further as follows:
[0060] After screening the obtained vulnerability data, keep the following key information, that is, vulnerability feature data, including: Common Vulnerability (CVE) number, Common Vulnerability Scoring System (CVSS) score, Attack Vector (AV), identity authentication, common Platform (CPE), Confidentiality Impact, Integrity Impact, Usability Impact, and Vulnerability Damage Description; the description and values of related fields are as follows:
[0061] Common vulnerability number: You can quickly find the corresponding information in the CVE-compatible database, regardless of the number of vulnerabilities, the value of the number is different, for example: CVE-2018-4858;
[0062] Common Vulnerability Scoring System Score: evaluates the severity of the vulnerability and helps determine the urgency and imp...
Embodiment 3
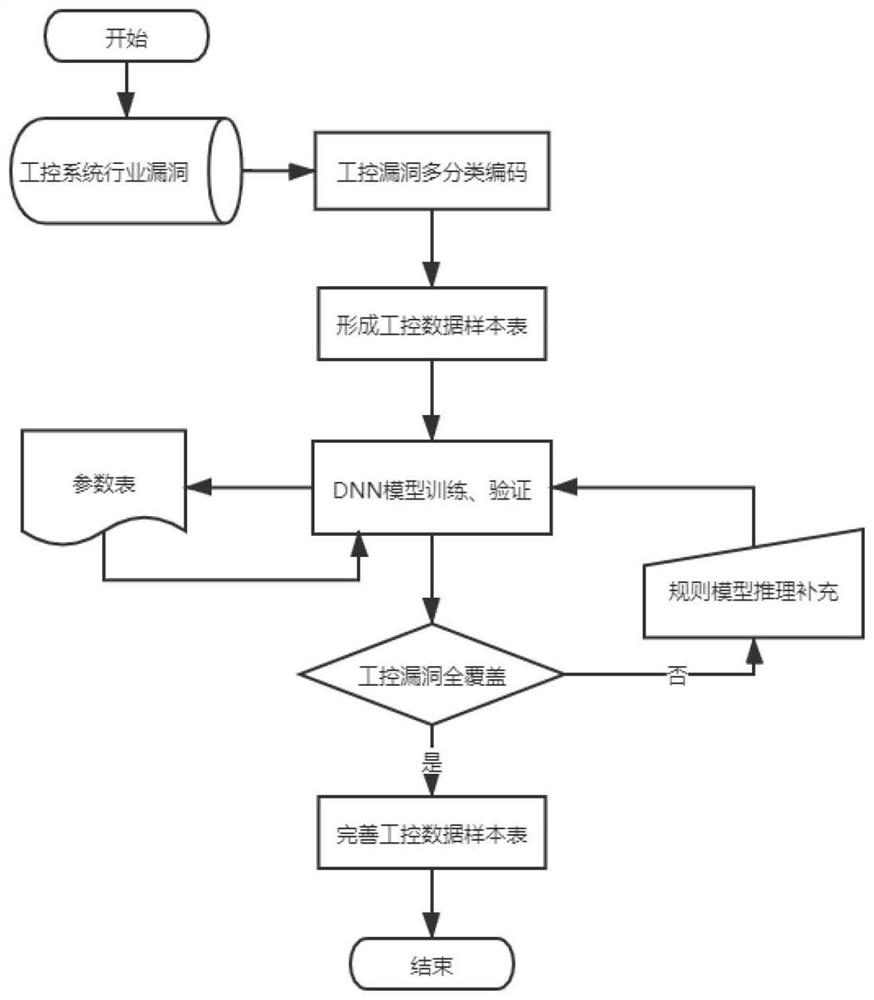
[0076] A vulnerability association mining method for an industrial control system. The difference from that described in Embodiment 1 is that manual extraction of the mark of the authority set of vulnerabilities is inefficient and prone to data loss. Therefore, machine learning algorithms and rule processing are adopted. In the combined way, step (3) is: input the data description field of the industrial control vulnerability into the deep neural network (DeepNeural Networks, DNN) model for training and learning, obtain the permission set label as the output, and then deal with the situation that the perceptron model cannot cover Next, the rule model is used to supplement, and a complete process of automatically generating and extracting permission set tags is obtained. Finally, the correlation structure analysis is carried out for the vulnerabilities that already have the precondition permission set and the result permission set value, and the logical relationship between the v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com