Continuous variable quantum key distribution attack detection method and detection system thereof
A technology for quantum key distribution and attack detection, which is applied in the field of quantum communication and can solve problems such as application limitations in the quantum key distribution process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
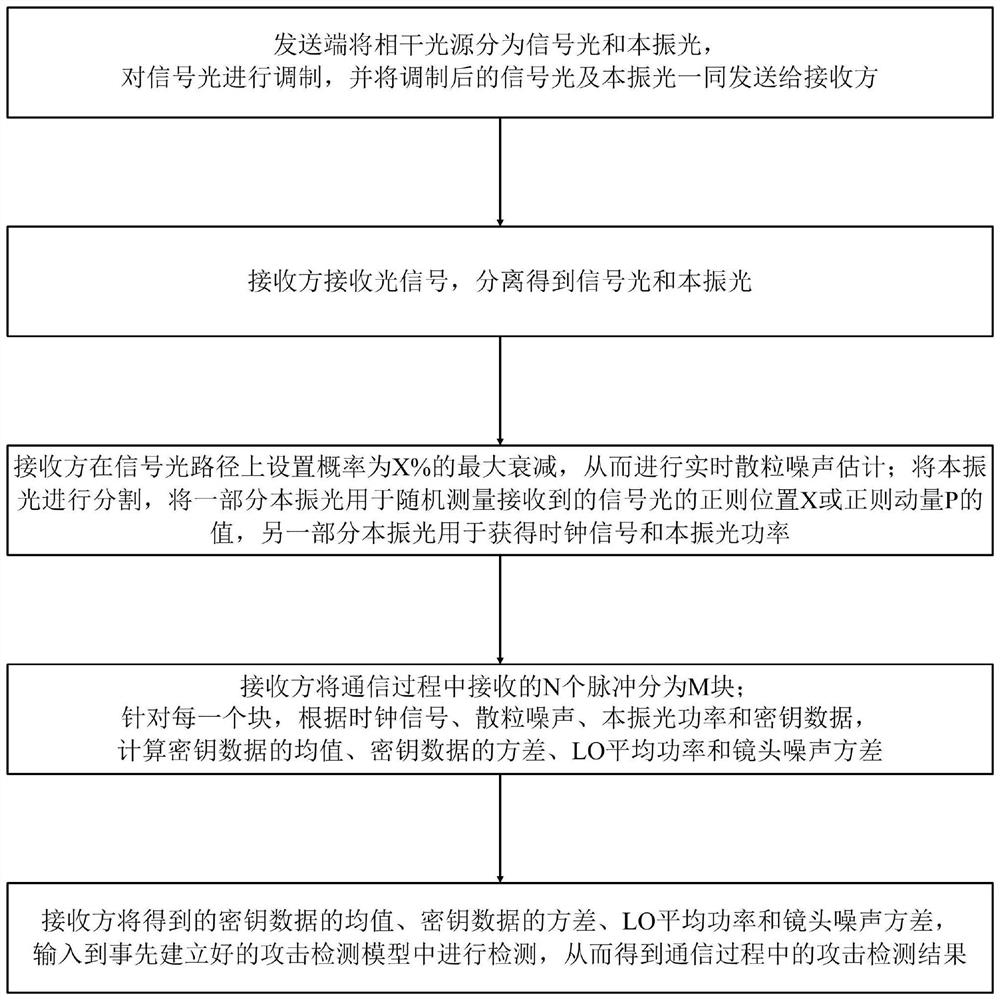
[0050] Such as figure 1 Shown is a schematic process flow diagram of the method of the present invention. The continuous variable quantum key distribution attack detection method provided by the present invention comprises the following steps:
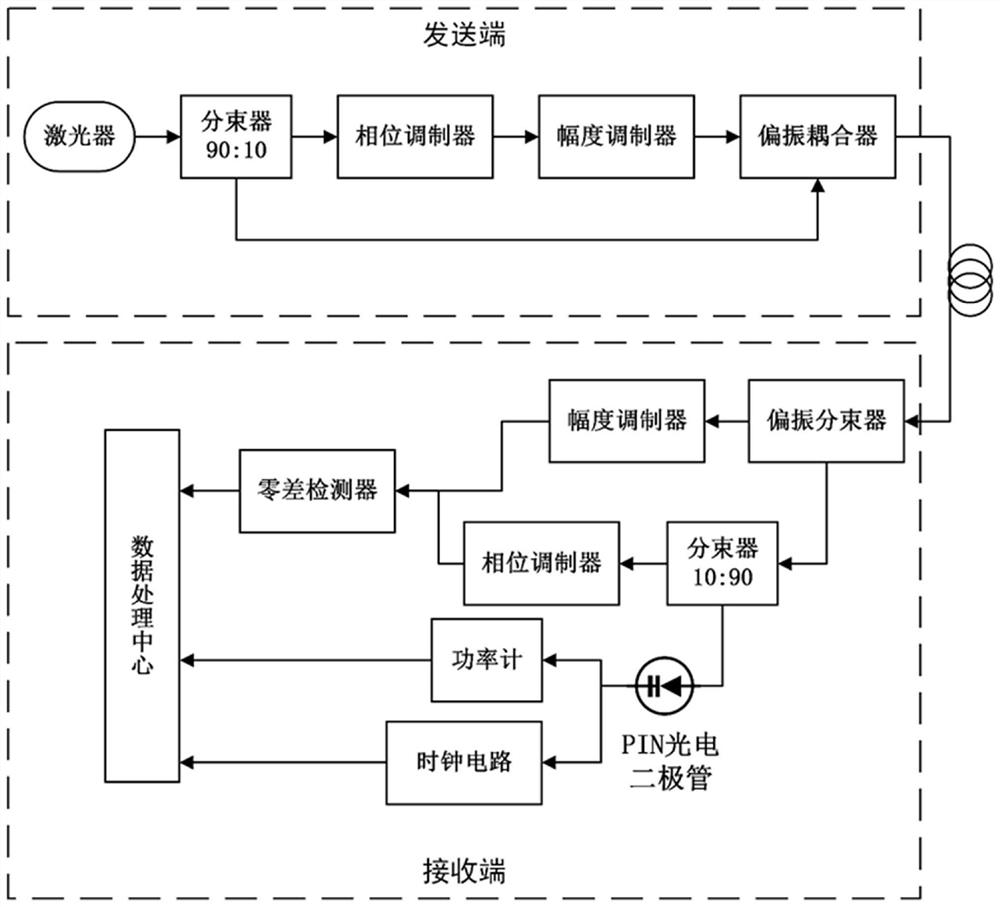
[0051] S1. The sender divides the coherent light source into signal light and local oscillator light, modulates the signal light, and sends the modulated signal light and local oscillator light to the receiver; specifically, the sender divides the coherent light source into signal light and local oscillator light, phase modulation and amplitude modulation on the signal light, and send the modulated signal light and local oscillator light to the receiver through polarization multiplexing;
[0052] In the specific implementation, the coherent state normal components X and P are encoded and modulated by phase and amplitude modulation, so that the signal light obeys a Gaussian distribution with a mean value of zero and a variance of VA; w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com