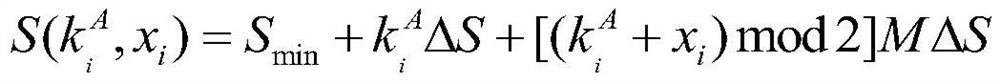A method of secure information transmission based on photon noise aliasing multi-ary transformation
A photon noise and transmission method technology, applied in the field of optical information security transmission, can solve the problems of insufficient confidentiality, data content being cracked, and the inability to eliminate optical communication network eavesdropping, etc., so as to enhance the difficulty of analysis and realize the effect of information security transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
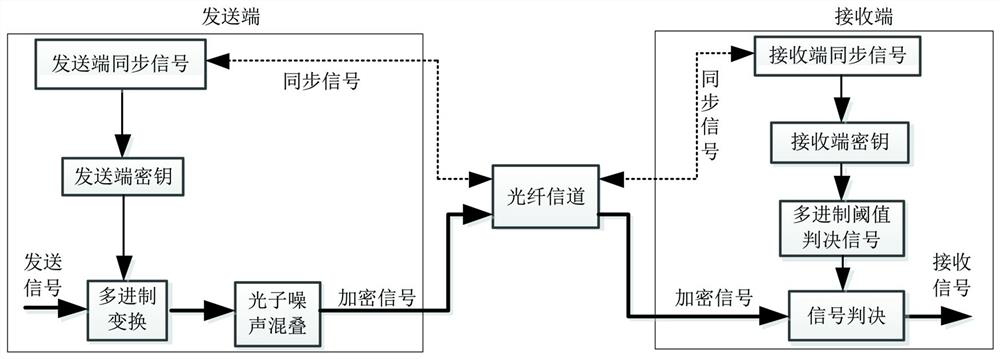
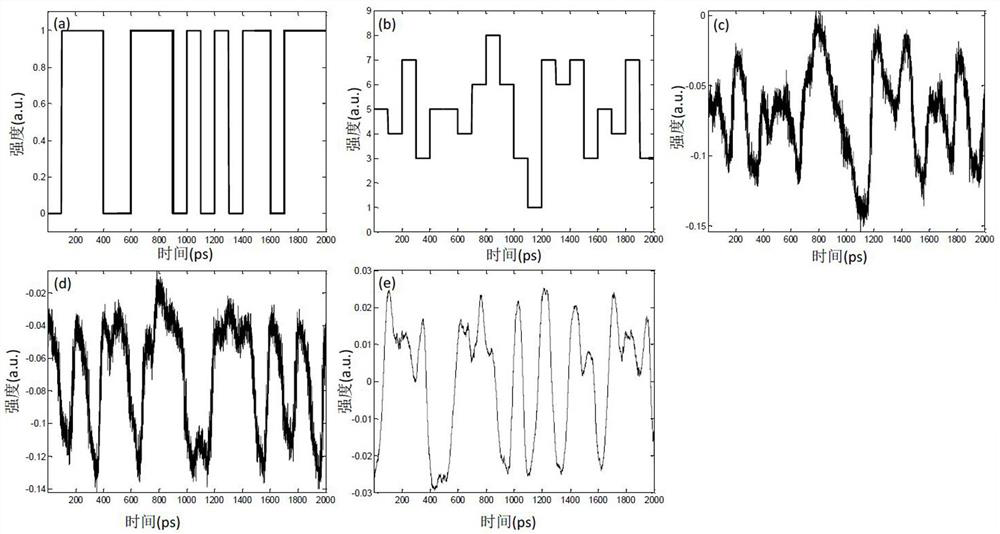
[0037] The sender will be as figure 2 The binary signal shown in (a) is jointly modulated with the random key signal as follows figure 2 The high-order signal shown in (b) utilizes the characteristic that the high-order signal is sensitive to noise, and hides the low-order signal in the photon noise, forming the figure 2 (c) For the secret signal shown in the solid line, due to the reciprocity of the optical fiber channel, the receiving end and the transmitting end measure the characteristics of the optical fiber channel by sending synchronization information, so as to realize the matching of the synchronizing signal at the transmitting end and the synchronizing signal at the receiving end to generate a synchronization key, and then generated as figure 2 The multi-ary system threshold judgment signal shown in (d) is finally compared bit by bit by receiving the confidential signal and the multi-ary system threshold judgment signal, and the recovery is as follows: figure ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com