Gene sequence security comparison method and system supporting multi-attribute anonymous authentication
A gene sequence and anonymous authentication technology, applied in sequence analysis, computer security devices, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
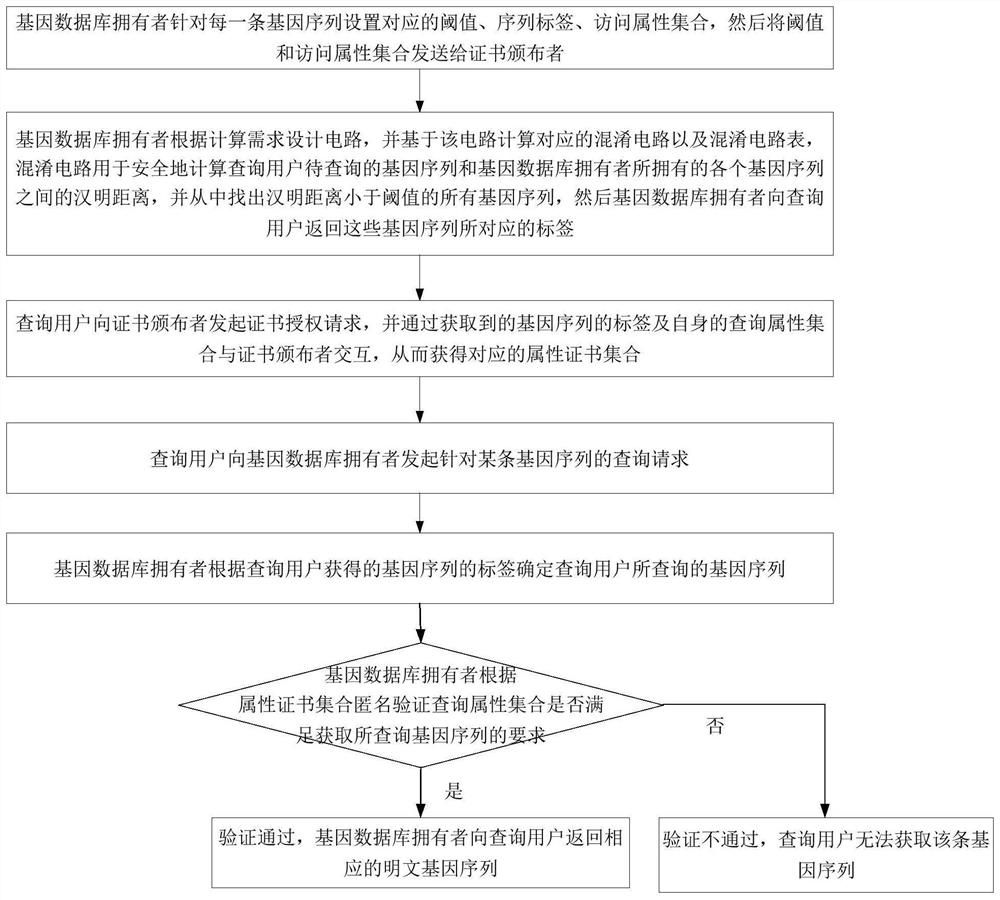
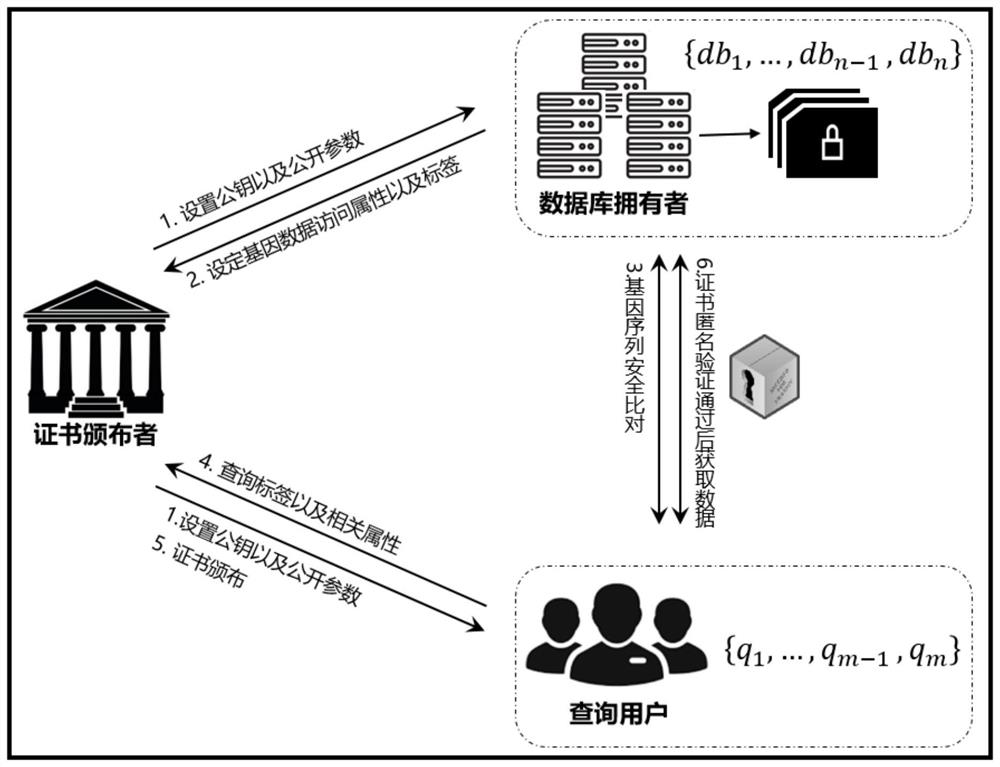
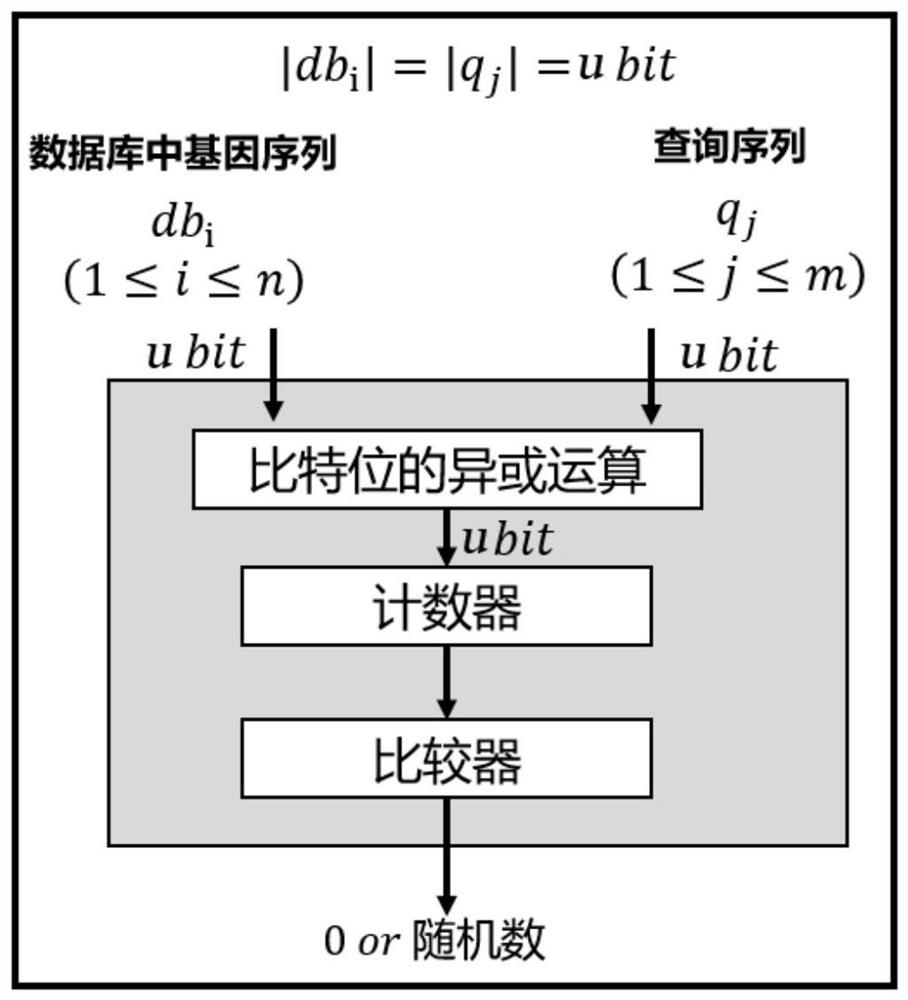
[0062] This embodiment discloses a gene sequence security comparison method that supports multi-attribute anonymous authentication, such as figure 1 with figure 2 shown, including the following steps:
[0063] S1. The owner of the gene database initializes the gene sequence it holds: set the corresponding threshold, label, and access attribute set for each gene sequence, and then send the threshold and access attribute set to the certificate issuer.
[0064] The initialization process is as follows:
[0065] S11. The certificate issuer generates its own private key sk issuer , generate and expose the system-wide parameter pk issuer , and determine the attribute set U that contains all possible attributes;
[0066] S12. The owner of the gene database obtains the public parameter pk of the issuer of the certificate issuer , based on the public parameter pk issuer Generate public-private key pair pk DB 、sk DB , for each gene sequence db it owns i Set index, access attr...
Embodiment 2
[0096] This embodiment discloses a gene sequence security comparison system that supports multi-attribute anonymous authentication. The system can implement the gene sequence security comparison method that supports multi-attribute anonymous authentication described in Example 1. The system specifically includes a query client , Gene database owner end, certificate issuer end.
[0097] Among them, the genetic data owner can be a plurality of independent database institutions, which can provide original genetic data. The query client can be a general client that only initiates a query request, or a genetic data owner that also provides genetic data. The certificate issuer can be a third-party trusted organization, which can be assumed by important departments, such as the National Institutes of Health (NIH) and the International Human Genome Organization (HUGO), which are responsible for generating and issuing attribute certificates.
[0098] The gene sequence safety compariso...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com