Application security detection task automatic arrangement method based on vulnerability fingerprint identification
A technology for detection tasks and application security, applied in character and pattern recognition, computer security devices, instruments, etc., can solve the problems of inability to determine the implementation effect of security activities, effective improvement, no security guarantee, lack of security management and control knowledge base, etc., to achieve improvement The quality and speed of alert classification, the resolution of detection timing lag, the effect of reducing manual workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
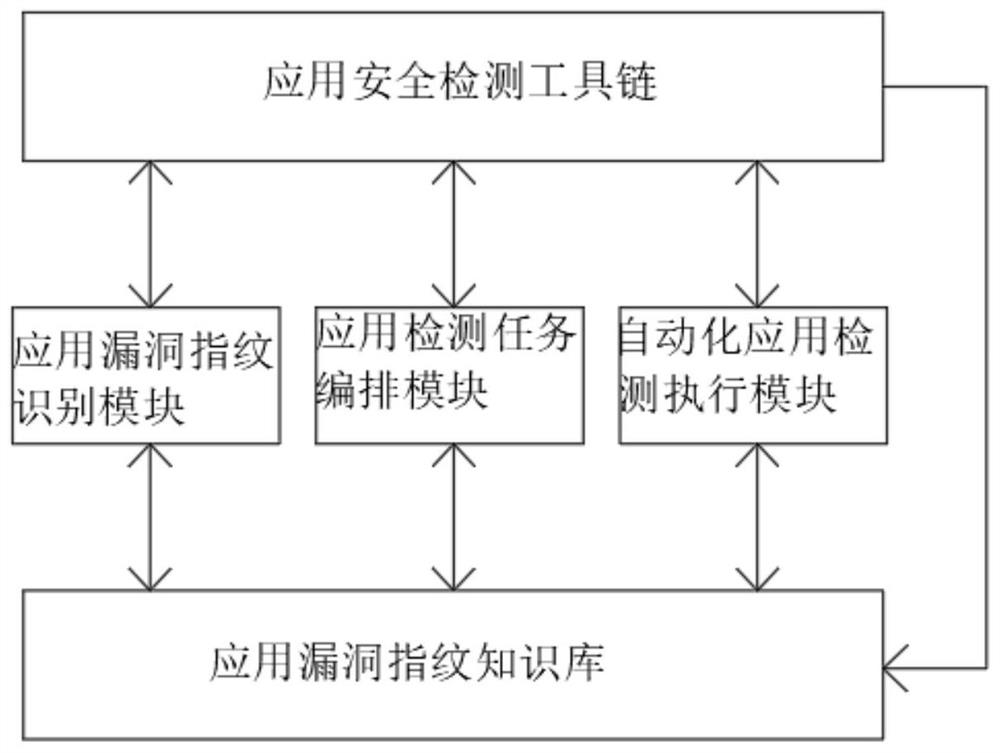
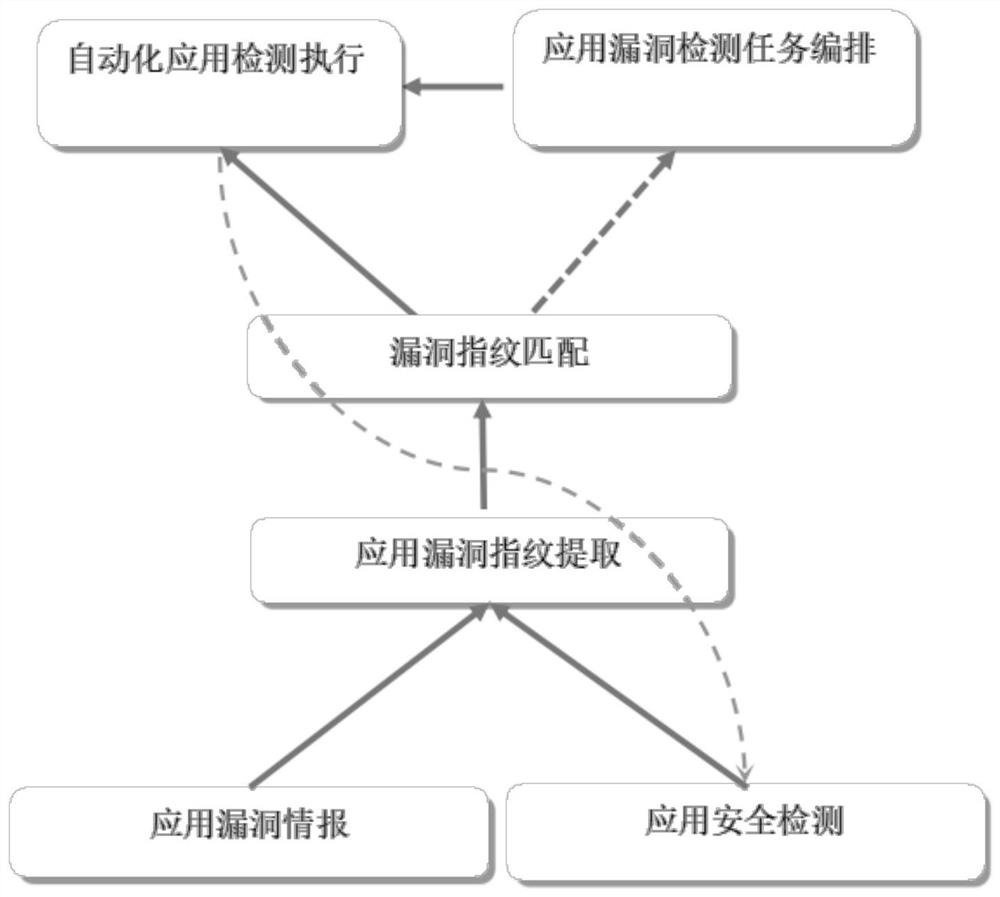
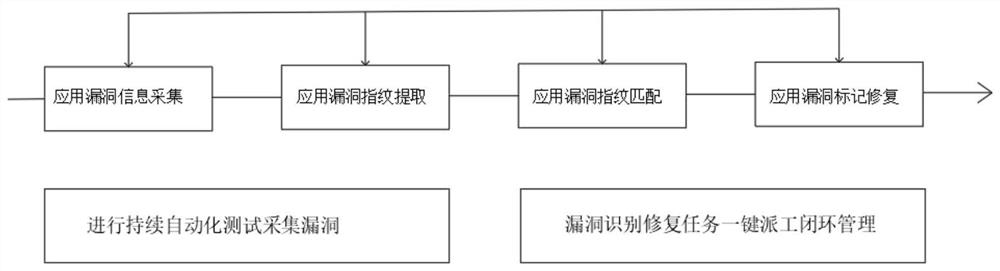
[0039] see Figure 1 to Figure 4 , the present invention provides a technical solution: a method for automatically arranging application security detection tasks based on vulnerability fingerprint identification, which mainly includes an application vulnerability fingerprint knowledge base, three working modules and a set of tool chains;
[0040] Application Vulnerability Fingerprint Knowledge Base: Summarize, analyze and discover application vulnerability fingerprints, which are used to mark and detect application vulnerabilities;
[0041] The three working modules include: the application vulnerability fingerprint identification module; the vulnerability identification is completed by matching with the vulnerability fingerprint knowledge base;
[0042]Application detection task arrangement module; can integrate different vulnerability data sets and security detection technologies together to complete task arrangement configuration;
[0043] Automated application detection e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com