Internet of vehicles crowd sensing reputation management system and method based on blockchain
A crowd-sensing and blockchain technology, applied in transmission systems, digital transmission systems, mechanical equipment, etc., can solve problems such as the inability to quantify data quality fairly, not proposing privacy protection technology, and erroneous calculation results of reputation value, etc. The effect of avoiding single point of failure, resisting Sybil attacks, and low system latency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
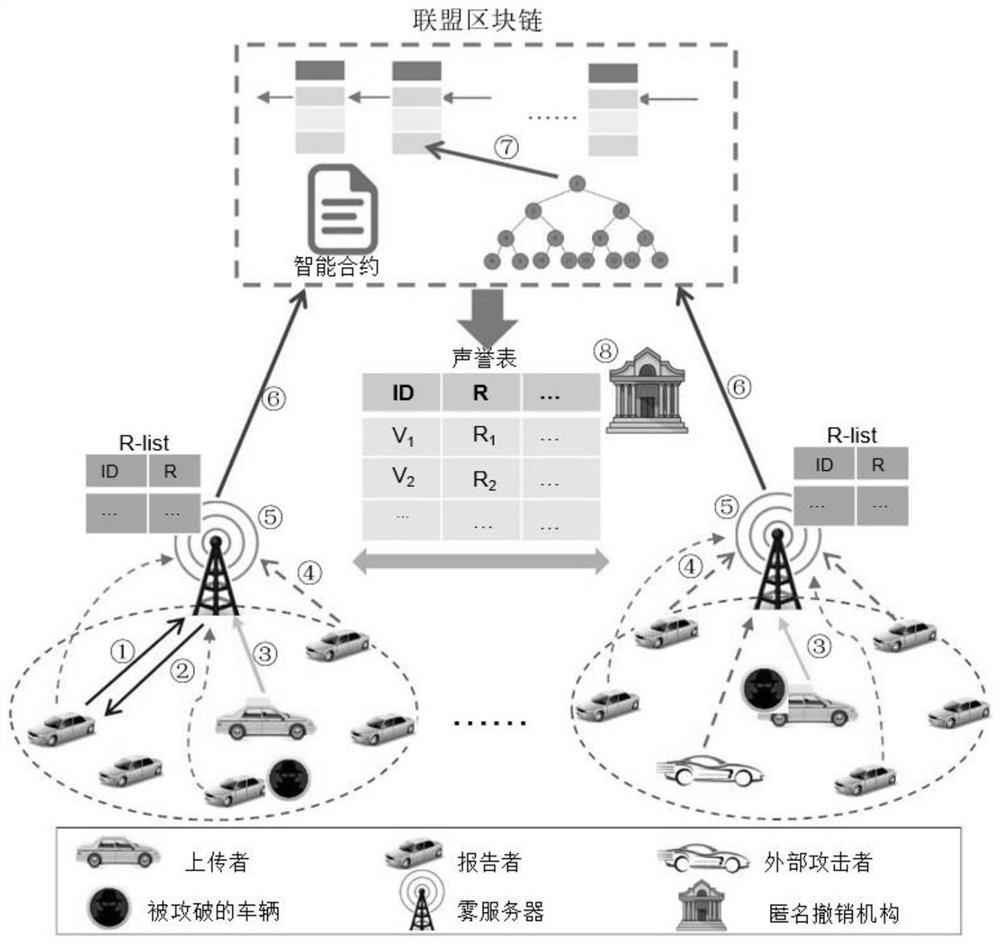
[0042] A block chain-based car networking group intelligence perception reputation management system, such as figure 1 As shown, the system includes a blockchain network, fog servers, vehicles, and an anonymous revocation mechanism.
[0043] The blockchain network refers to the alliance blockchain composed of fog servers in different traffic areas, which mainly realizes the function of updating the reputation through smart contracts. The fog server acts as a consensus node in the PoA-based consortium blockchain, which is used to verify and package the newly added blockchain to maintain the blockchain network, and is responsible for task release, data reception and data quality quantification; in addition, the local The fog server maintains a reputation list (R-list), which includes the vehicle's identity and reputation. Vehicles are divided into two categories: uploaders and reporters. The uploaders will always generate data reports on traffic information in the Internet of V...
Embodiment 2
[0045] A privacy-protected Internet of Vehicles crowd-sensing reputation management method based on blockchain, the method adopts the system of Embodiment 1, and specifically includes the following steps:
[0046] Step 1. Anonymous authentication; when the vehicle performs the task of group intelligence sensing, the submitted data should be authenticated by the fog server. The fog server first releases the security parameters, and the registered vehicle sets the public key and private key of the traceable ring signature through Pedersen commitment , to achieve anonymous authentication; the local fog server maintains a reputation list, which is used for ring selection for ring signature generation, and any submitted data will be authenticated anonymously. The detailed steps are as follows:
[0047] ①System settings: Fog server F runs Setup(1 λ ) algorithm to generate public parameters para={G, q, g, h, ch, H, H'}. G is a group of order q>2λ, where λ is a security parameter. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com