Digital information risk monitoring method and device
A monitoring device and risk technology, which is applied in the field of big data, can solve problems such as insufficient processing of sensitive data, untimely risk monitoring, and low efficiency of message data, and achieve the effects of convenient risk management, high degree of automation, and simple use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
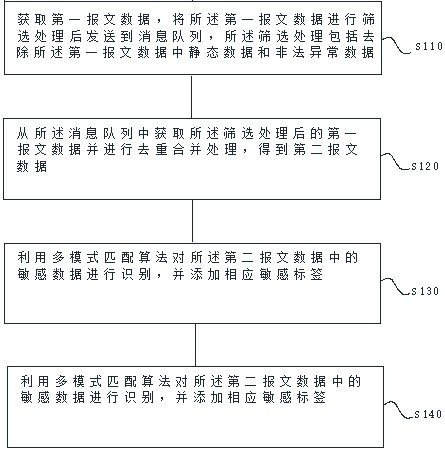
[0058] Such as figure 1 As shown, a digital information risk monitoring method includes the following steps:
[0059] S110. Acquire the first message data, and send the first message data to the message queue after screening, the screening process includes removing static data and illegal abnormal data in the first message data;
[0060] S120. Acquire the filtered first message data from the message queue and perform deduplication and combination processing to obtain second message data;
[0061] S130. Using a multi-pattern matching algorithm to identify sensitive data in the second message data, and add a corresponding sensitive label;
[0062] S140. Put the second message data after the identification process into storage, and perform risk monitoring.
[0063] In Example 1, digital information mainly refers to information asset data of an enterprise, while sensitive data refers to data that may cause serious harm to society or individuals if leaked. Including personal pri...
Embodiment 2
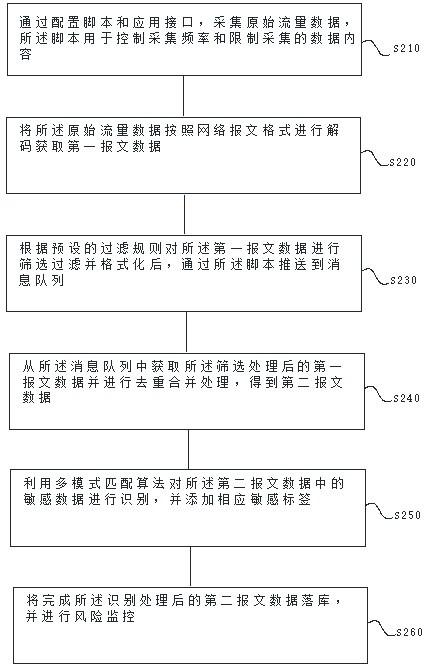
[0065] Such as figure 2 As shown, a digital information risk monitoring method includes:
[0066] S210. Collect raw traffic data by configuring scripts and application interfaces, where the scripts are used to control collection frequency and limit collected data content;
[0067] S220. Decode the original traffic data according to the network packet format to obtain the first packet data;
[0068] S230. After filtering and formatting the first message data according to preset filtering rules, push it to the message queue through the script;
[0069] S240. Acquire the screened first message data from the message queue and perform deduplication and merging processing to obtain second message data;
[0070] S250. Use a multi-pattern matching algorithm to identify sensitive data in the second message data, and add a corresponding sensitive label;
[0071] S260. Put the second message data after the identification process into storage, and perform risk monitoring.
[0072] It...
Embodiment 3
[0074] Such as image 3 As shown, a digital information risk monitoring method includes:
[0075] S310. Acquire the first message data, and send the first message data to the message queue after screening, the screening process includes removing static data and illegal abnormal data in the first message data;
[0076] S320. Obtain the screened first message data from the message queue, extract key parameters therefrom, use an information digest algorithm to concatenate and encrypt the key parameters sequentially to generate a unique hash value; according to the hash The value is deduplicated and merged;
[0077] S330. Match the text content of the second message data according to a preset keyword and a preset regular expression, and add a sensitive label to the matching text content if the match matches; the preset keyword Represents personal privacy identity data, and the preset regular expression representation is used to retrieve and replace text that matches a certain pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com