Power consumption analysis method based on mean ridge regression
A technology of power consumption analysis and ridge regression, applied in the field of information security, to achieve the effect of expanding correlation, reducing matrix dimension, and reducing computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
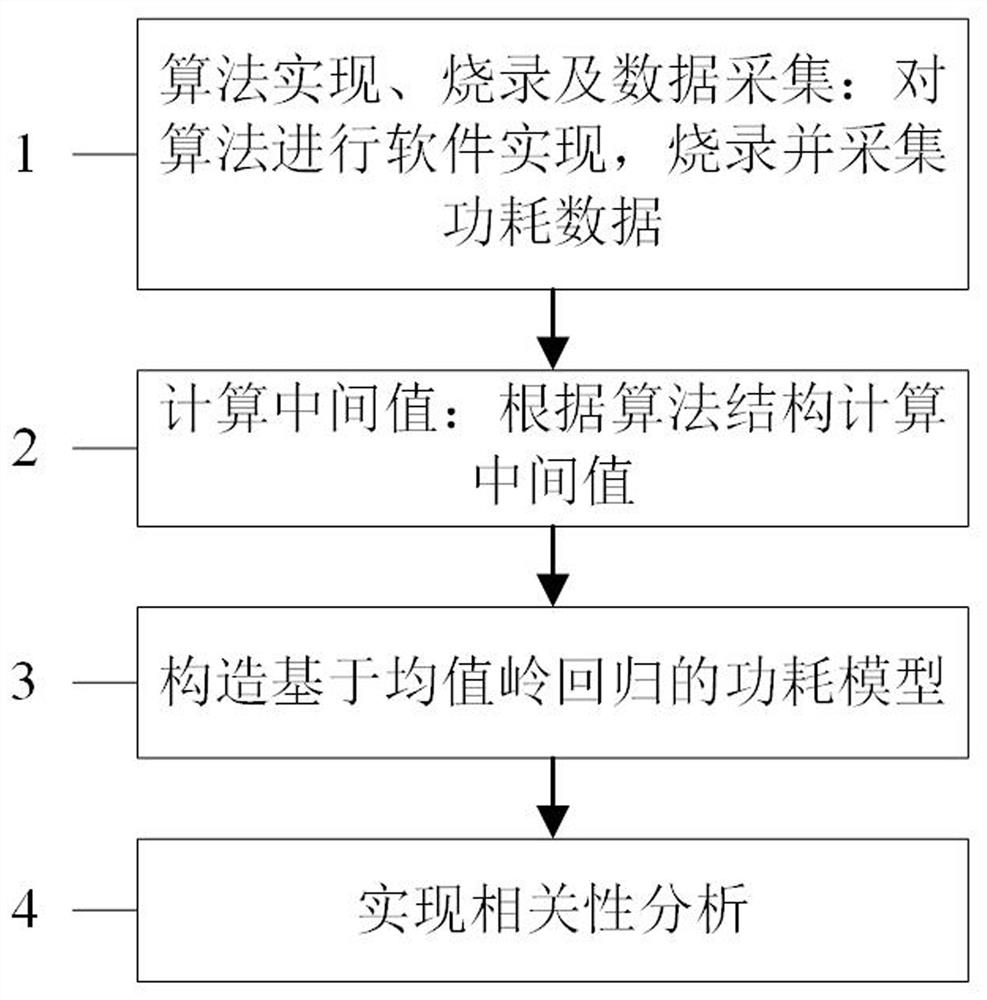
[0059] refer to figure 1 , a power consumption analysis method based on mean ridge regression. Taking the classic lightweight block cipher algorithm Present as an example, a power consumption model based on mean ridge regression is established and attacked. The specific steps are as follows:
[0060] (1) Collect the power consumption data of the Present algorithm during the operation of the cryptographic device;
[0061] (2) Calculate the intermediate value according to the Present algorithm structure;
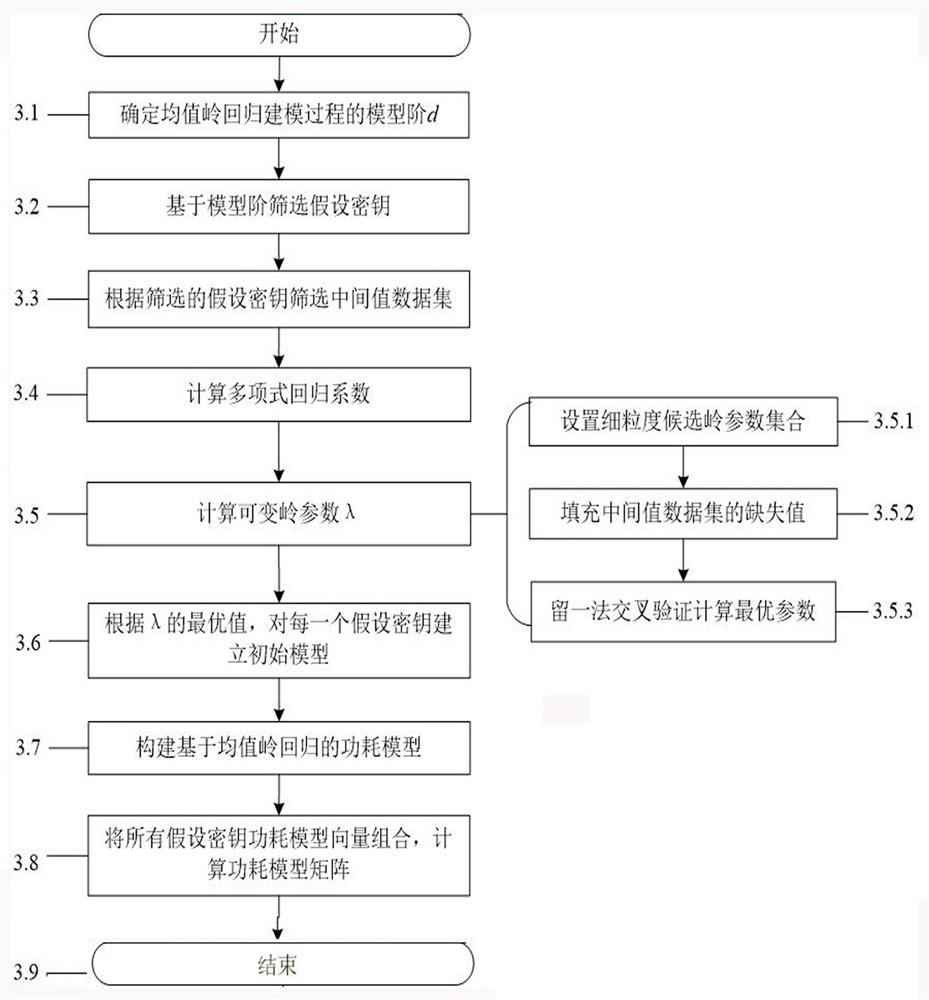
[0062] (3) Construct a power consumption model based on mean ridge regression;
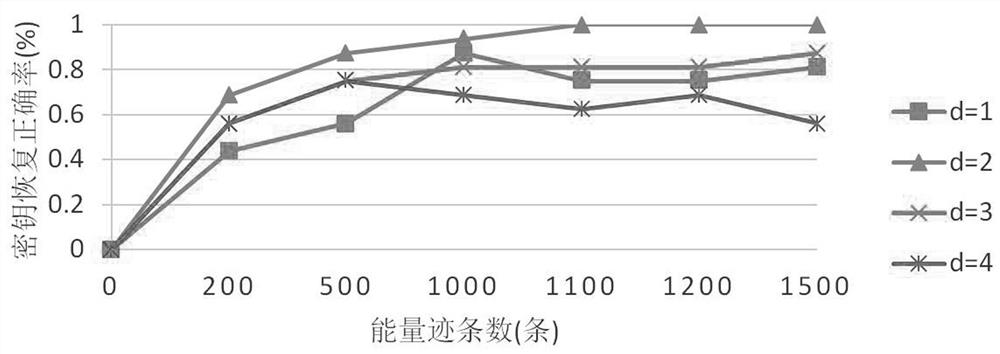
[0063] (4) Realize correlation analysis and restore the key information of the Present algorithm.
[0064] In step (1), the power consumption data of the Present algorithm during the operation of the cryptographic device is collected, and the specific steps are as follows:
[0065] (1.1) For the classic lightweight cryptographic algorithm Present, implement the Present algorithm based on the A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com