Method of digit identity authentication based on features of non-biophysics
A technology of physical characteristics and digital identity, applied in the field of group encryption, it can solve the problems of inability to generate passwords freely, difficult for ordinary people to understand and trust, and insecurity. Simple and clear effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
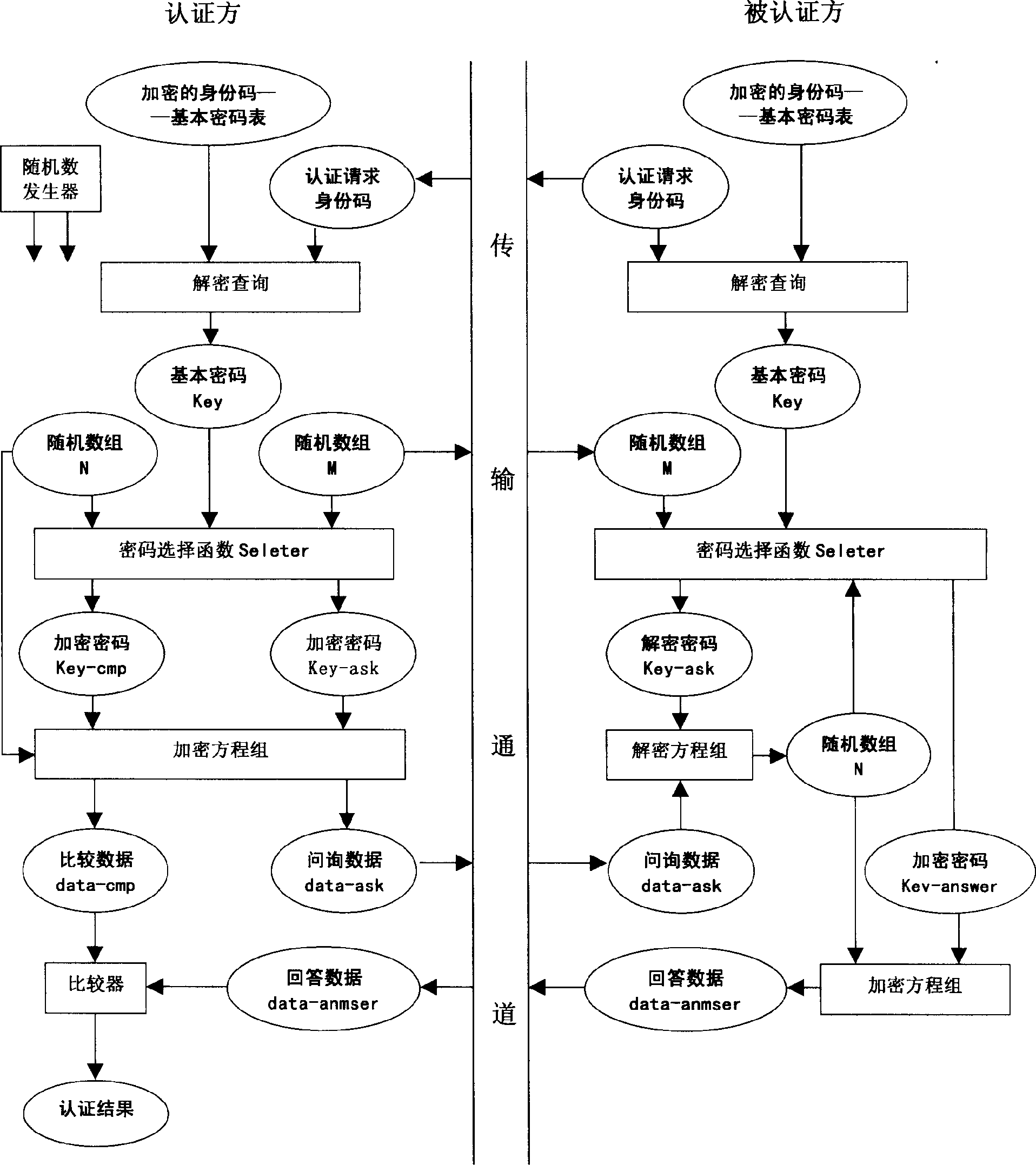
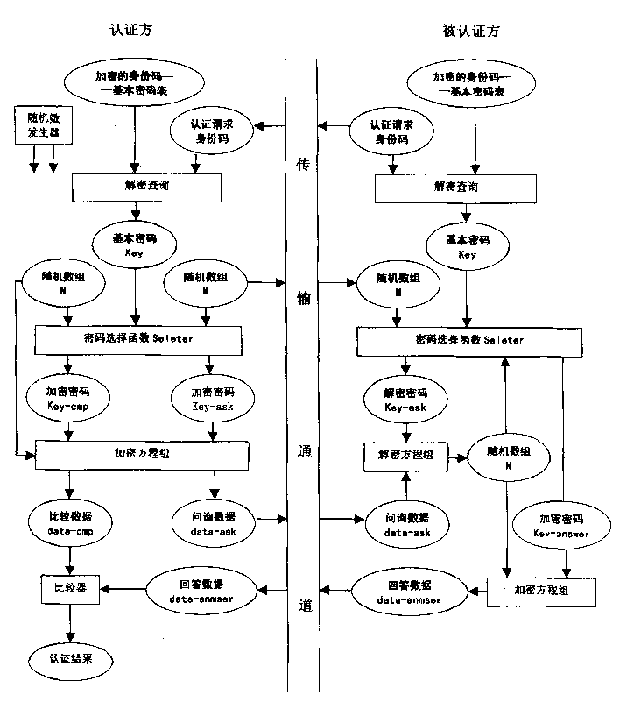
[0021] Embodiment 1: Use an electronic identity token to realize identity authentication and data transmission of a network system.
[0022] 1. The electronic identity token includes a processor, memory, display screen, keys, and an infrared, USB or wireless transmission interface. The transmission interface is used to communicate and transmit data with the corresponding communication interface of the computer, and the key is used to input the identity code. With various passwords, processors, memory and corresponding software, the algorithm and process of identity authentication of the present invention are automatically completed, and the display screen is used to display processing results, time, etc.
[0023] 2. System registration: The two parties who need identity authentication, such as the network service computer and the user, register the identity code generated by each other with each other, and use reliable confidential means to transmit and generate a basic password (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com