Digital information anti-interference soft encrypted method and system based on Turbo code-encode
A technology of digital information and soft encryption, which is applied in the direction of interference to communication, usage of multiple keys/algorithms, secure communication, etc. It can solve the problems of information encryption without considering information noise or electronic attack, etc., and achieve superior error correction performance And the effect of anti-interference ability, good encryption effect and good scrambling effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0060] The general framework of the present invention is as figure 1 As shown in the figure, the digital information source can be a digital voice signal, a digital image signal or a data signal, that is, a series of letters, numbers and symbols representing concepts, commands and other texts or other forms of information. The sender forms an encrypted file with the digital information through the encryption module, and realizes the transmission of the information on the network through the communication interface. After the channel transmission, the receiver realizes the reception of the encrypted data through the communication interface, and then decrypts the information by the decryption module of the receiver. .
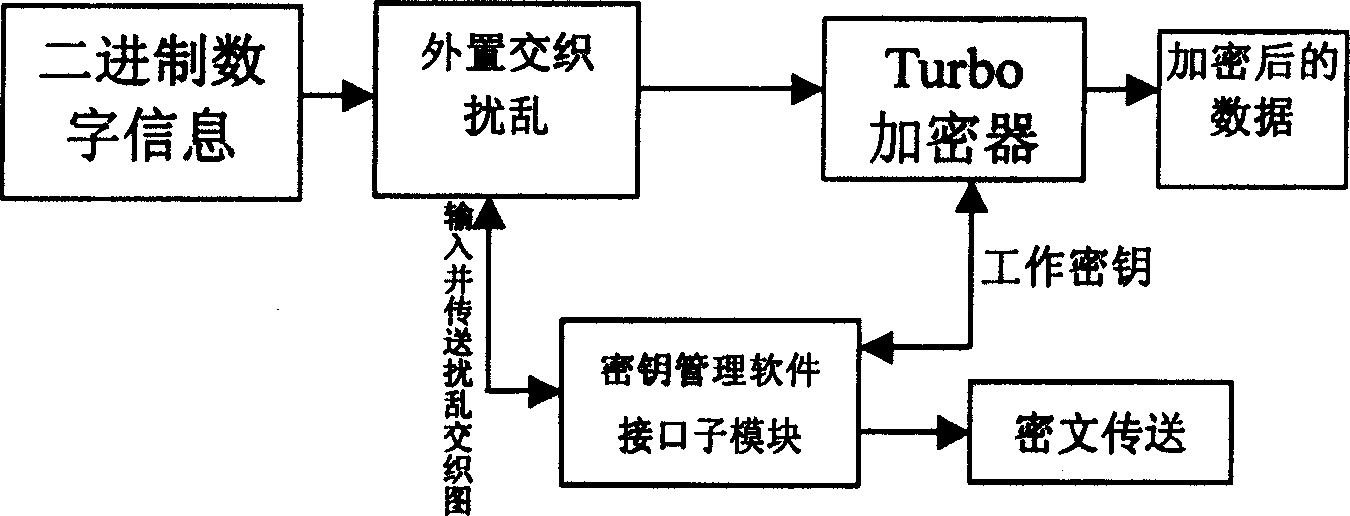
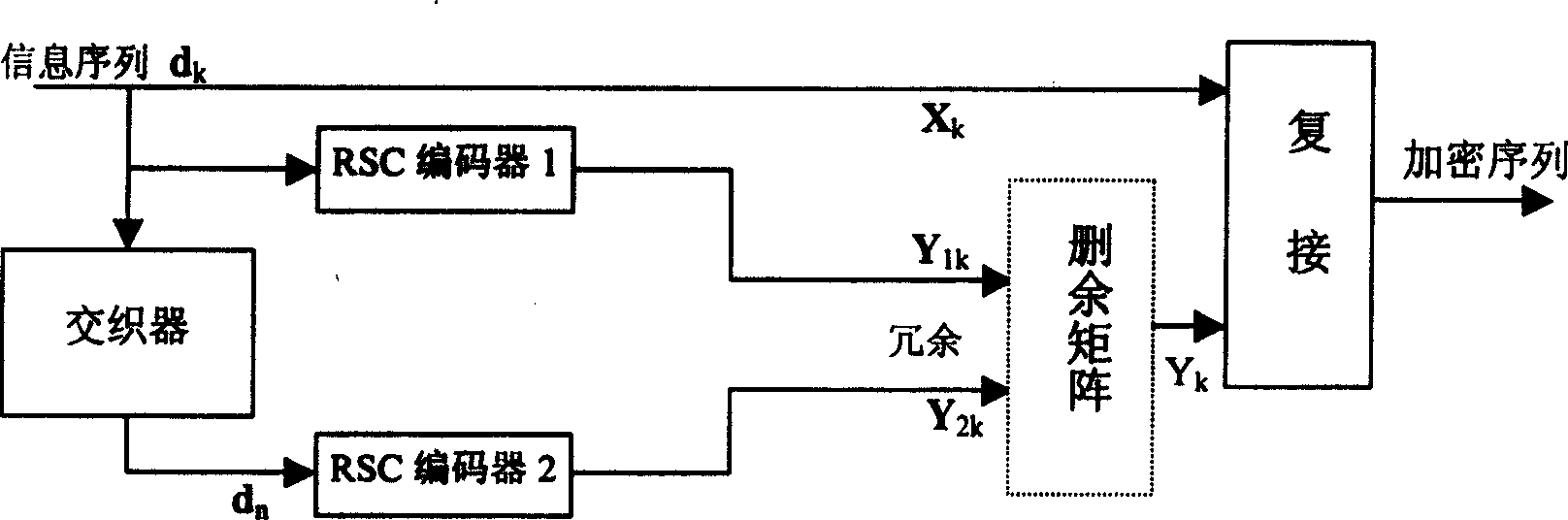
[0061] The structure of the encryption module is attached figure 2 shown. It consists of three parts: an external interleaving and scrambling submodule, a Turbo encryptor and a key management software interface submodule. The binary digital information is inp...
Embodiment 2
[0121] The present invention introduces an example of the effect after encrypting a section of voice signal and a digital image, and performs a performance simulation on the effect of encryption.
[0122] 1. Voice signal
[0123] A section of voice signal has been selected in the example of the present invention, and its amplitude sampling is as attached Figure 8 shown.
[0124] The encrypted signal is attached as Figure 9 shown. Figure 9 In the experiment, because the code rate is 1 / 2 in the experiment, the number of sampling points is doubled after Turbo encoding (from 128 to 256); the source encoding adopts PCM quantization encoding; and because the experiment uses BPSK Modulation, so the encoded data values are +1 / -1.
[0125] What needs to be declared is that the original voice signal is not interleaved and scrambled for the voice signal, and the encryption effect after scrambling will be explained in the image information.
[0126] The decrypted signal is attac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com