Preset network protection method capable of sharing bandwidth
A technology for network protection and bandwidth sharing, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as complex signaling and inability to achieve protection and recovery, and achieve the effect of simplifying network operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to better understand the technical solutions of the present invention, the implementation manners will be described in detail below in conjunction with the accompanying drawings and examples.
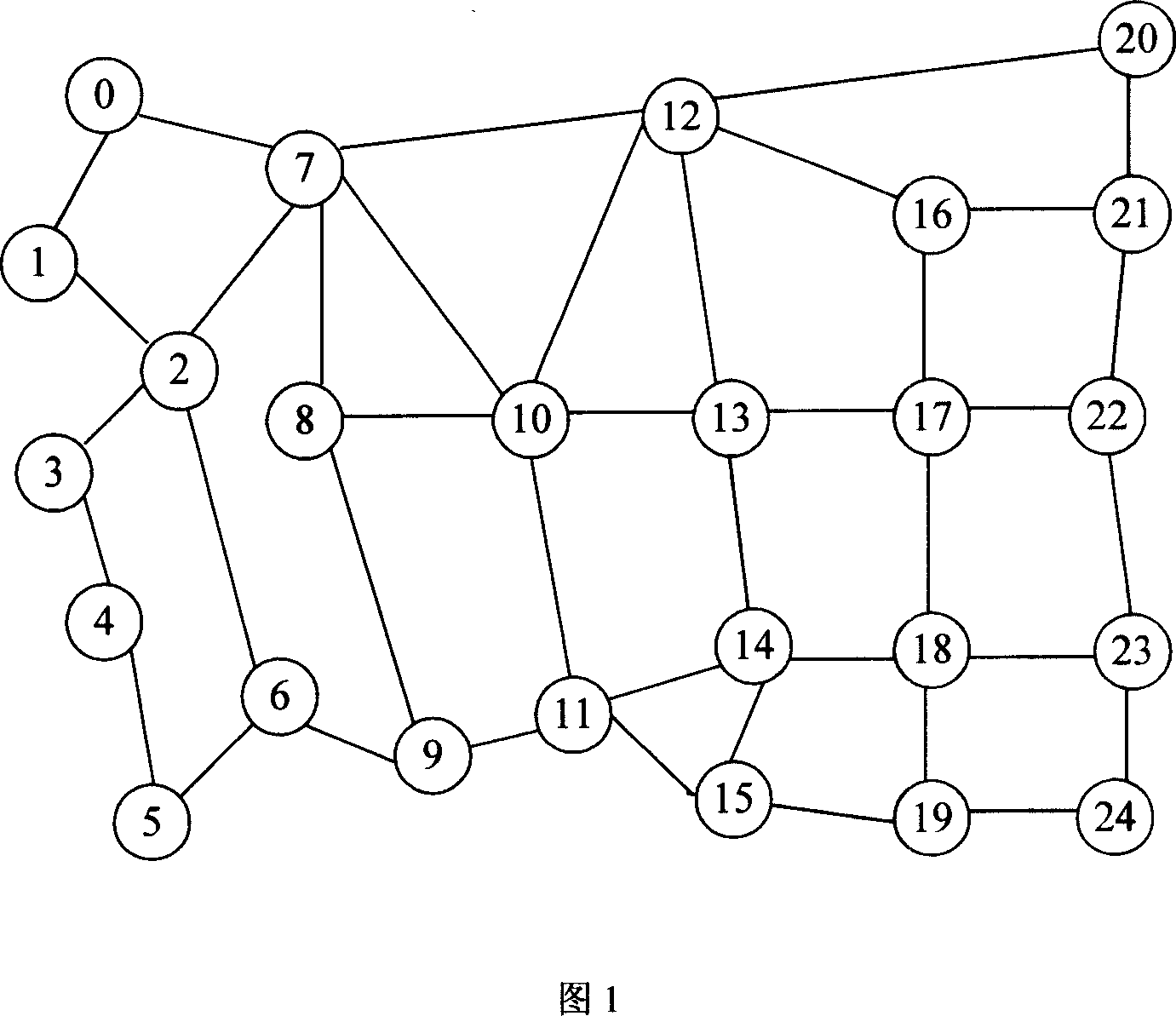
[0020] Fig. 1 is an example of the network topology adopted by the present invention, and there are 25 nodes in Fig. 1, numbered from 0 to 24. Assume that all network nodes have wavelength conversion capability, and each link has a pair of unidirectional optical fibers with opposite directions, and each optical fiber has 16 wavelengths. Each wavelength request in the network arrives at the network according to an independent Poisson distribution, and the average arrival rate is λ. The hold time of each connection follows a negative exponential distribution, and the average hold time of a connection is 1 / μ=1 unit time. Without loss of generality, it is assumed that all time units are "seconds", that is, 1 / μ=1s. The load of the network can be expressed by ρ=λ / μ, because 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com