Method for authentication
a technology of authentication and method, applied in the field of authentication, can solve the problems of reducing security, limiting the range of use, and/or not providing a high security level, and achieve the effects of increasing length, facilitating use, and increasing security level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
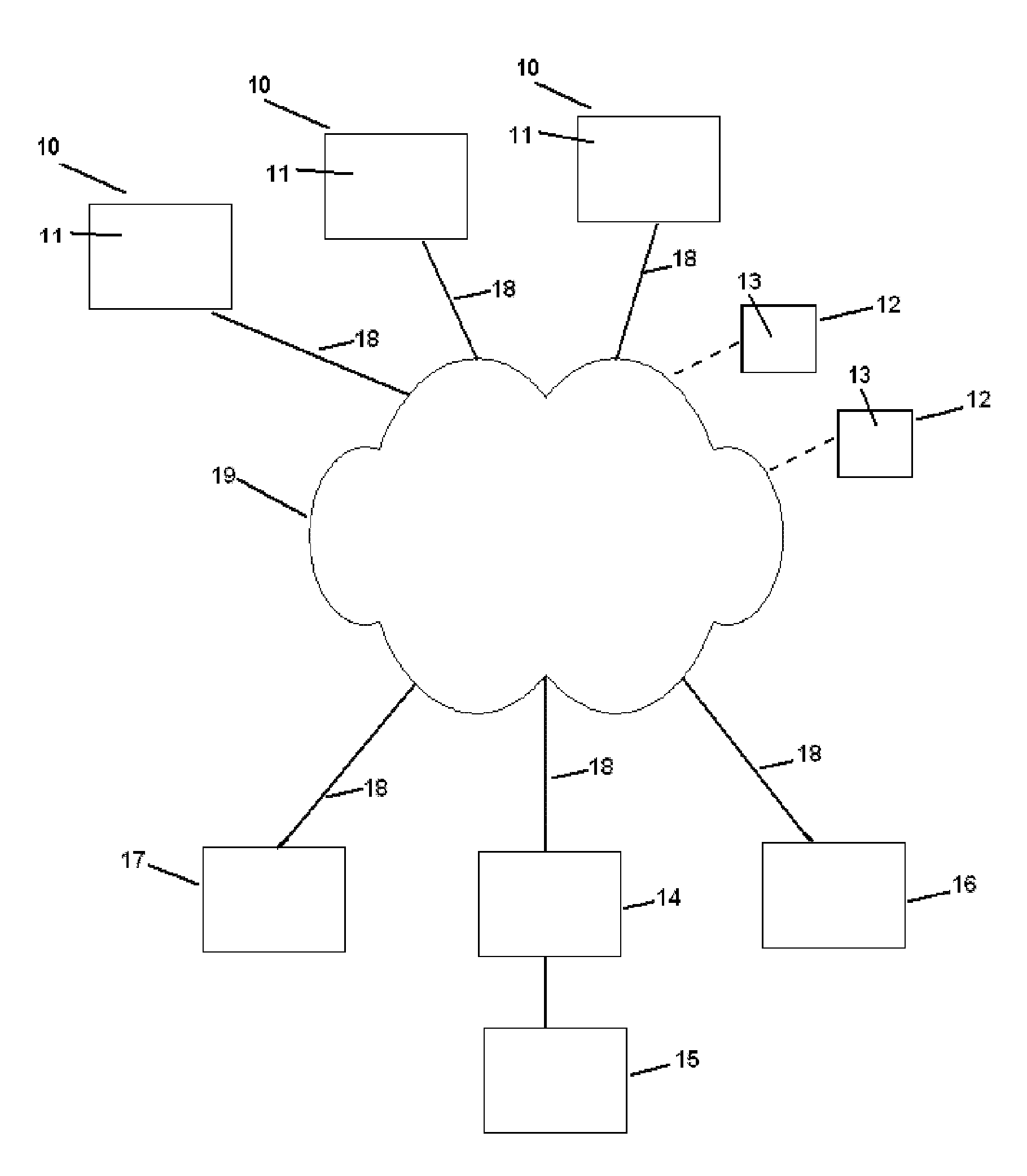
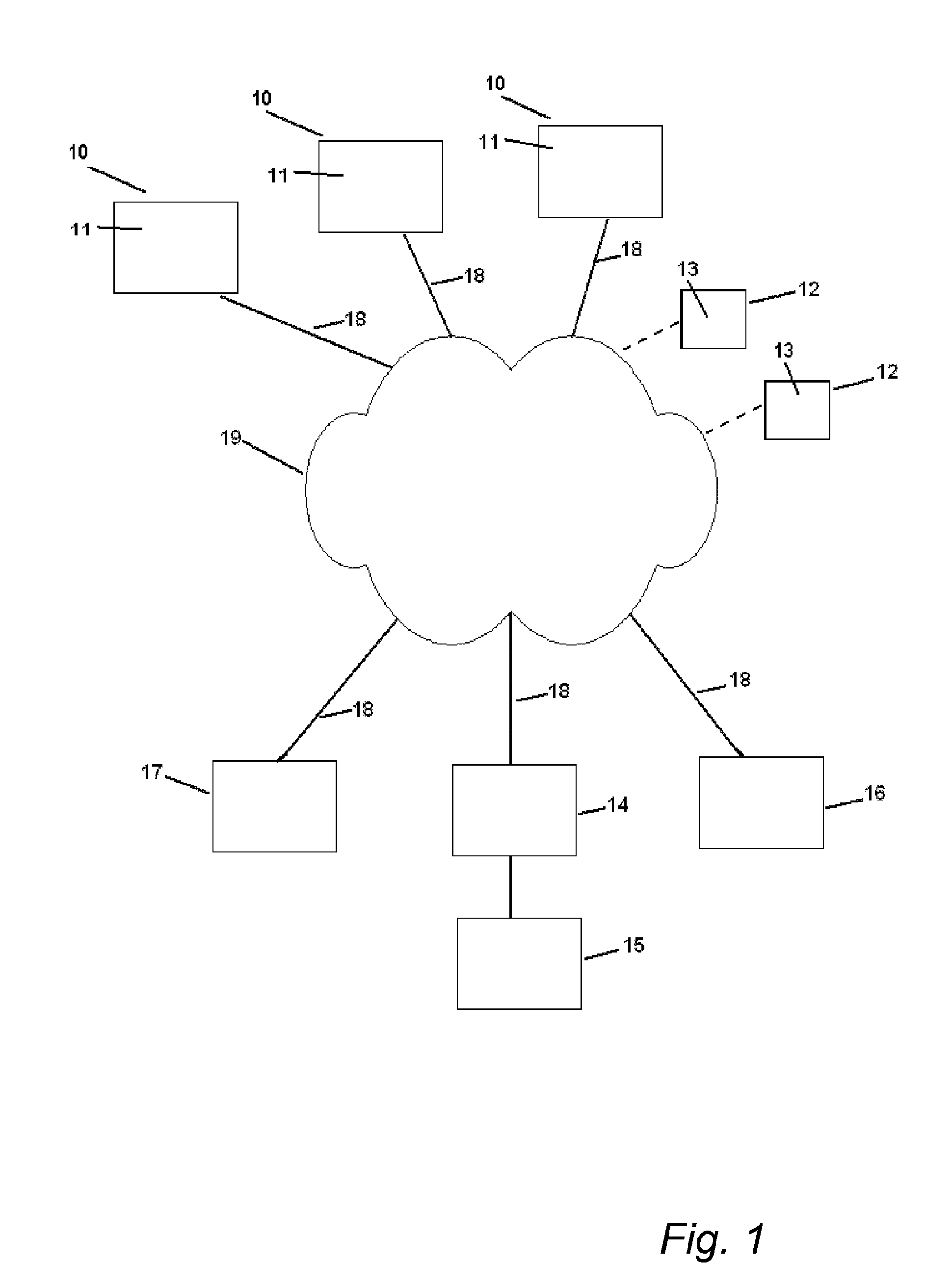
[0089]An overview of an example of a network structure in which the present invention can be used is illustrated in FIG. 1.
[0090]The illustrated network structure comprises a number of units 10, 12 and 14-17, in communicative connection via a communication network 19. The connection to the units may be wired, indicated by full lines in FIG. 1, or wireless, indicated by dashed lines in FIG. 1. The network 19 may be a public, semi-public or private network, for example internet or a private corporate network.
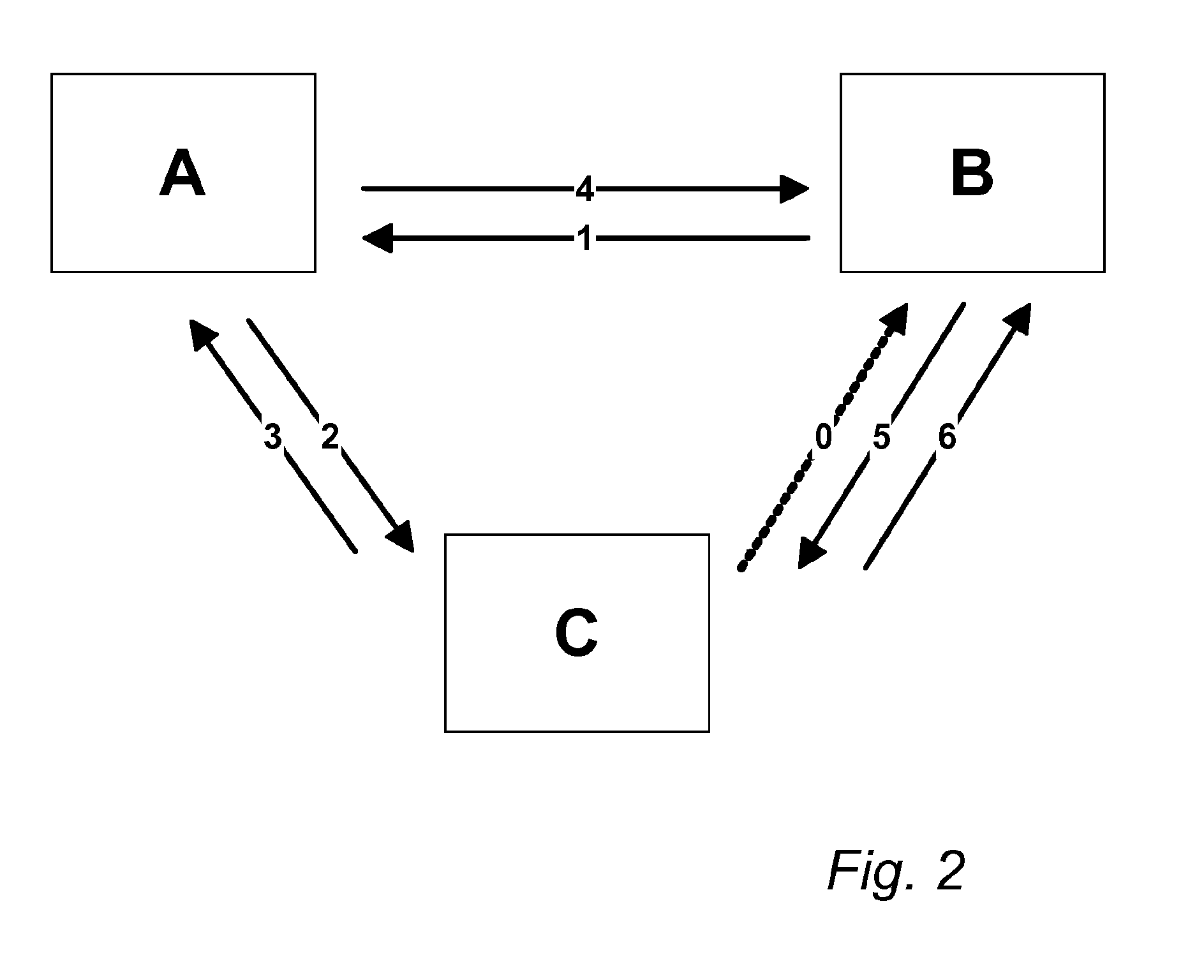
[0091]In the following description, some of the units are denoted first party 12, i.e. a unit requesting authentication, some units are denoted second party 10, from which authentication is requested, and some units are denoted trusted third party 15, by which the authentication is provided. In principle, any unit may take the role of first, second or third party, and a unit may also take the role of more than one of first, second and third party in different authentication proces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com