Communication system, communication apparatus, communication method, and program
A technology of a communication system and a communication device, applied in the field of communication, can solve the problems of time-consuming, installation-consuming, information leakage, etc., and achieve the effect of reducing the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
[0149] [Structure Description]
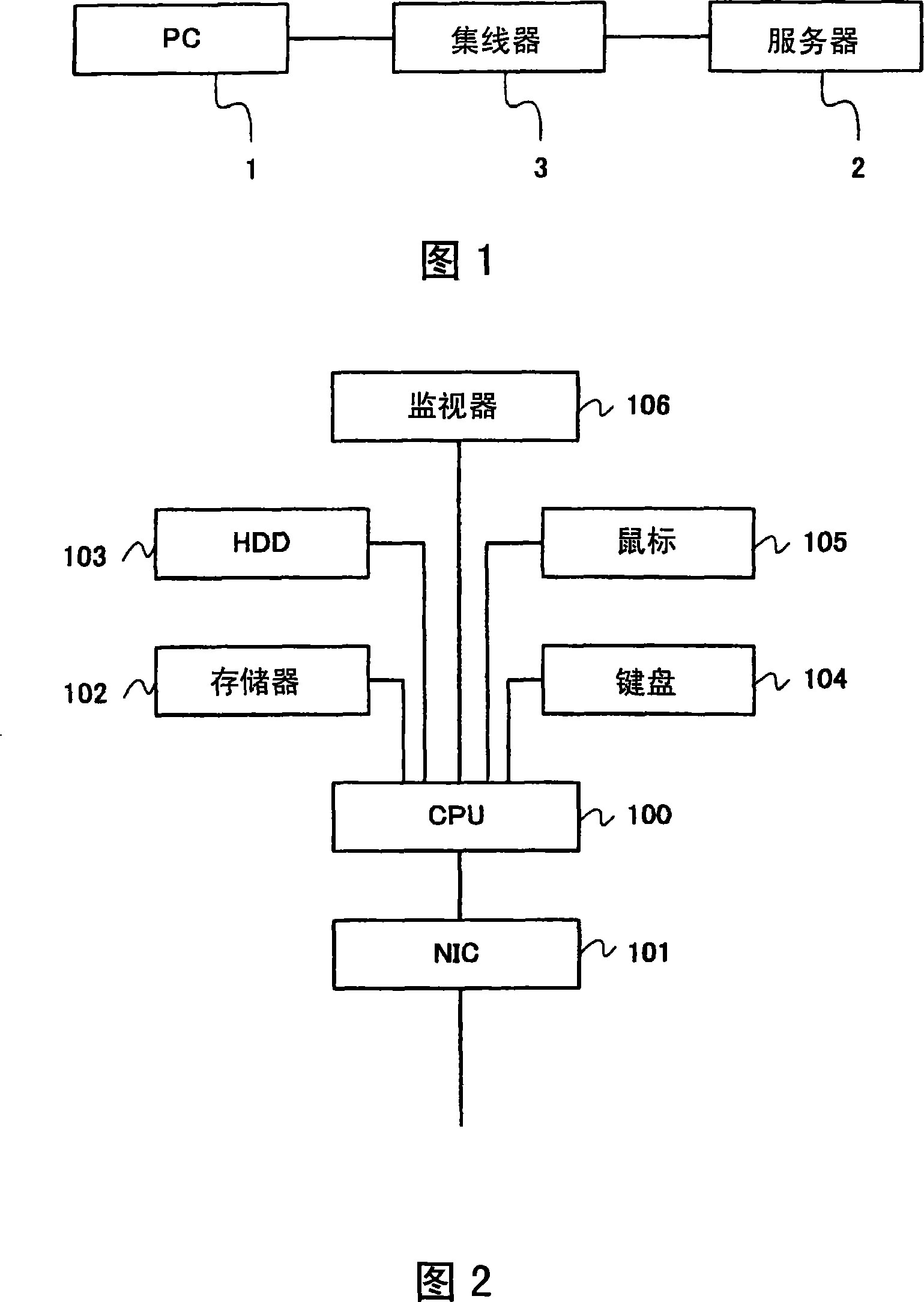
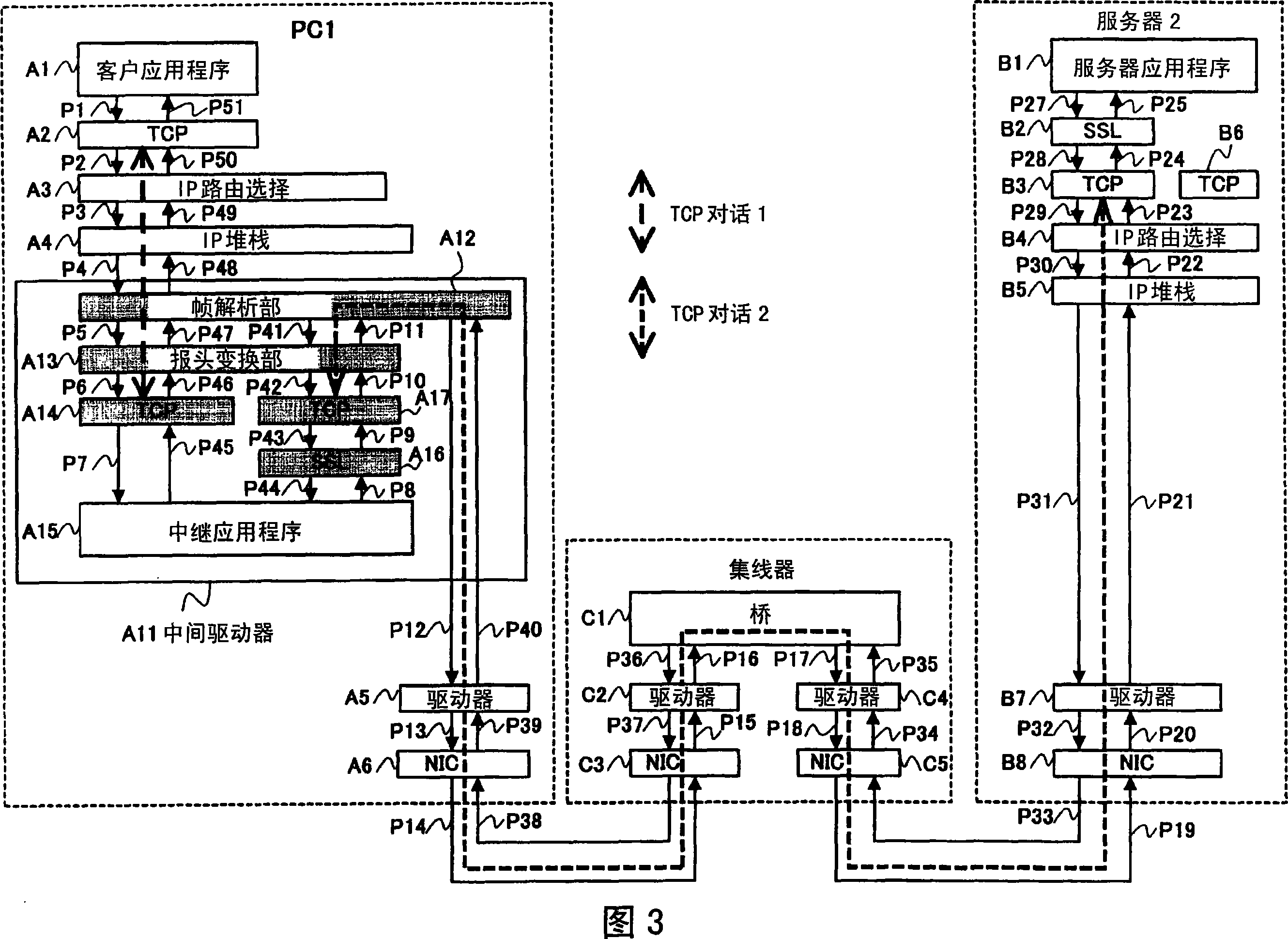
[0150] A first embodiment for carrying out the first invention of the present invention will be described in detail with reference to the drawings. FIG. 1 is a diagram showing the network configuration of the first embodiment, and includes a PC 1 , a server 2 and a hub 3 .
[0151] The PC1 is connected to the hub 3, acquires frames from the hub 3, and performs desired processing on the acquired frames. Moreover, PC1 transmits the frame generated by the internal processing of PC1 to the hub 3 .
[0152] The server 2 is connected to the hub 3, acquires frames from the hub 3, and performs desired processing on the acquired frames. Also, the server 2 transmits the frame generated by the internal processing of the server 2 to the hub 3 .
[0153] The hub 3 is connected to the PC1 and the server 2 . The hub 3 acquires the frame from the PC1, analyzes the acquired frame, and transfers the frame to an appropriate port based on the analysis result. ...
no. 2 approach
[0301] [explanation of the structure]
[0302] Next, a second embodiment for carrying out the second invention of the present invention will be described in detail with reference to the drawings. The network configuration of the second embodiment is the same as the network configuration of the first embodiment shown in FIG. 1 , and therefore description thereof will be omitted.
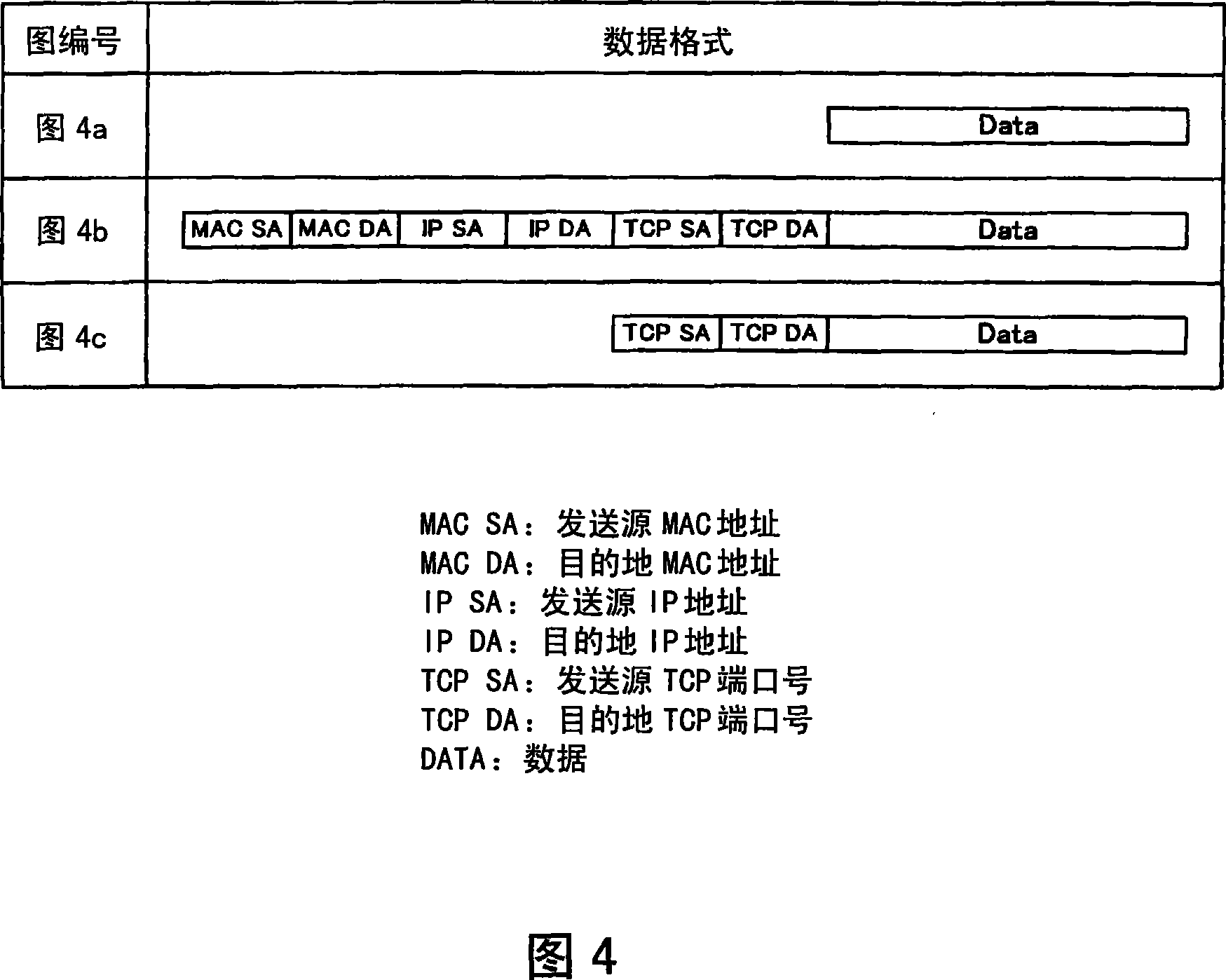
[0303] FIG. 12 is a diagram showing communication processing performed by a CPU and an NIC mounted in each device of the present embodiment. Referring to FIG. 12 , the second embodiment differs from the first embodiment in that it has a drive A19 and a virtual NICA 20 in addition to the configuration of PC1 in the first embodiment in FIG. 3 .
[0304] The function of the driver A19 is the same as that of the driver A5 shown in FIG. 3 , and therefore description thereof will be omitted.
[0305] The NICA 20 is assumed to be software that mediates the driver A19 and the relay application A15. It is a...
no. 3 approach
[0349] [explanation of the structure]
[0350] Next, a third embodiment for carrying out the second invention of the present invention will be described in detail with reference to the drawings. The network configuration of the third embodiment is the same as the network configuration of the first embodiment shown in FIG. 1 , so description thereof will be omitted.
[0351] FIG. 15 is a diagram showing communication processing of the CPU and NIC mounted in each device of the present embodiment. Referring to FIG. 15, the third embodiment can eliminate the driver A19 and the virtual NICA20 in the structure of the PC1 in the second embodiment shown in FIG. It is different from the second embodiment. Along with this, the function of each module changes as follows.
[0352] The outline of the function of TCPA25 is substantially the same as that of TCPA21 of the second embodiment shown in FIG. .
[0353] The outline of the function of the relay application A26 is almost the sam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com