Method of implementing fast rerouting
A routing and fast technology, applied in the field of network communication, can solve the problems of degraded multicast application service quality, multicast data loss, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0121] The first implementation mode: Only when the protected link fails, the backup path calculated in advance is used to maintain the PIM neighbor relationship and the multicast tree to reduce the data loss in the routing protocol convergence process.
[0122] The second implementation mode: only when the protected node fails, the network element calculated in advance is used to maintain the PIM neighbor relationship and the multicast tree to reduce the data loss during the convergence process of the routing protocol.
[0123] The third implementation mode: only when the protected node fails, the backup multicast tree established in advance is used to reduce the data loss in the process of routing protocol convergence.
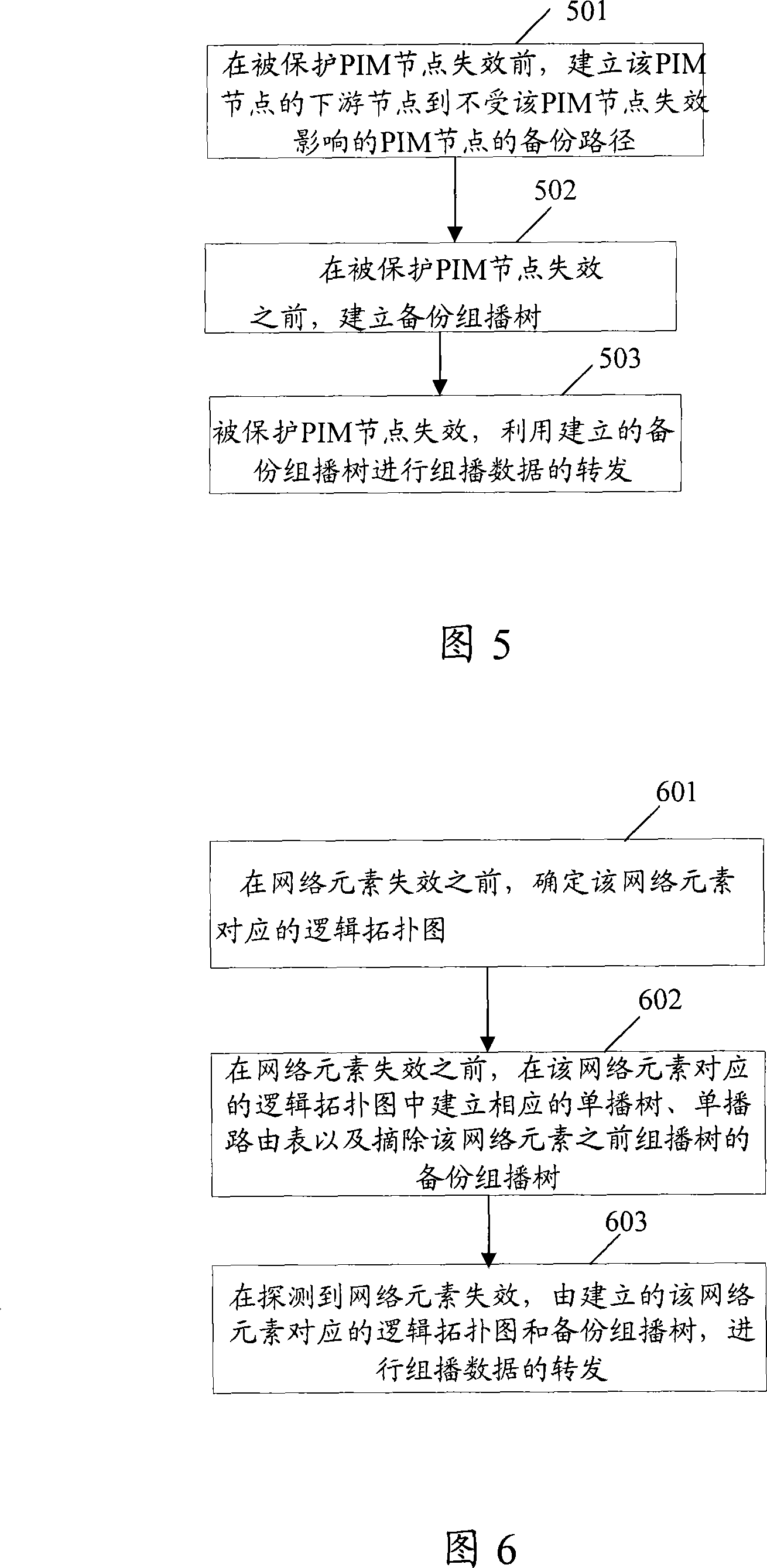
[0124] The fourth implementation mode: when the protected link fails or the protected node fails, or the protected link and the protected node fail at the same time, use the establishment of multiple logical topology planes in advance and the establishment an...
Embodiment 1
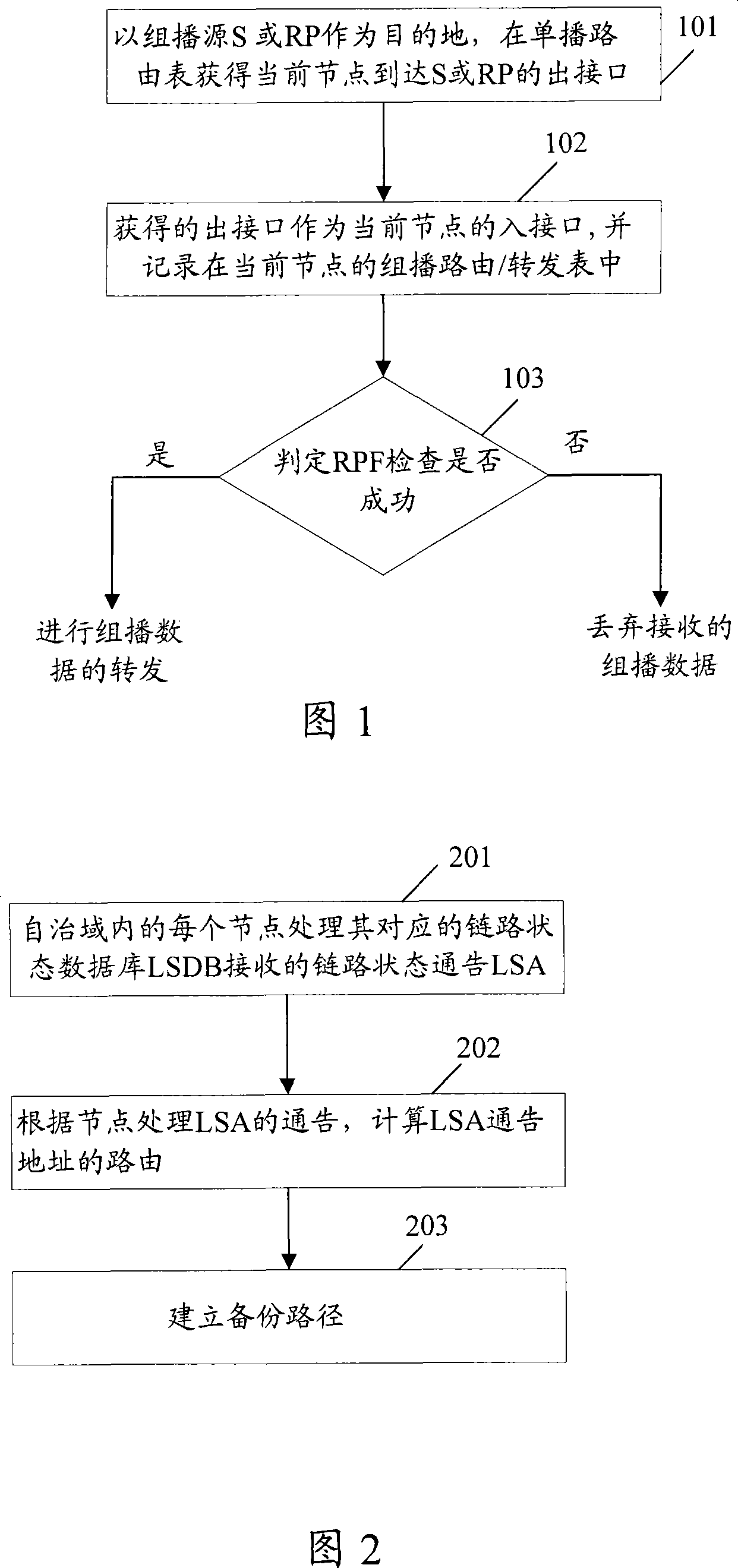
[0127] Referring to Fig. 3, Fig. 3 is a schematic flow chart of the first preferred embodiment of the rerouting method after the protected link fails in the present invention, including:
[0128] Step 301: Establish a backup path of the protected link before the protected link fails.
[0129] In this embodiment, the protected link is the protected link connected between the two PIM nodes; the backup path for the protected link is established to establish a backup for the protected link connected between the two PIM nodes path. In the following, for simplicity of description, the protected link connected between two PIM nodes is referred to as a protected link for short.
[0130] In this step, before the protected link fails, the established backup path of the protected link is a backup path calculated for two nodes directly connected to the protected link. Through the backup path, the two nodes directly connected to the protected link can continue to communicate. The method...
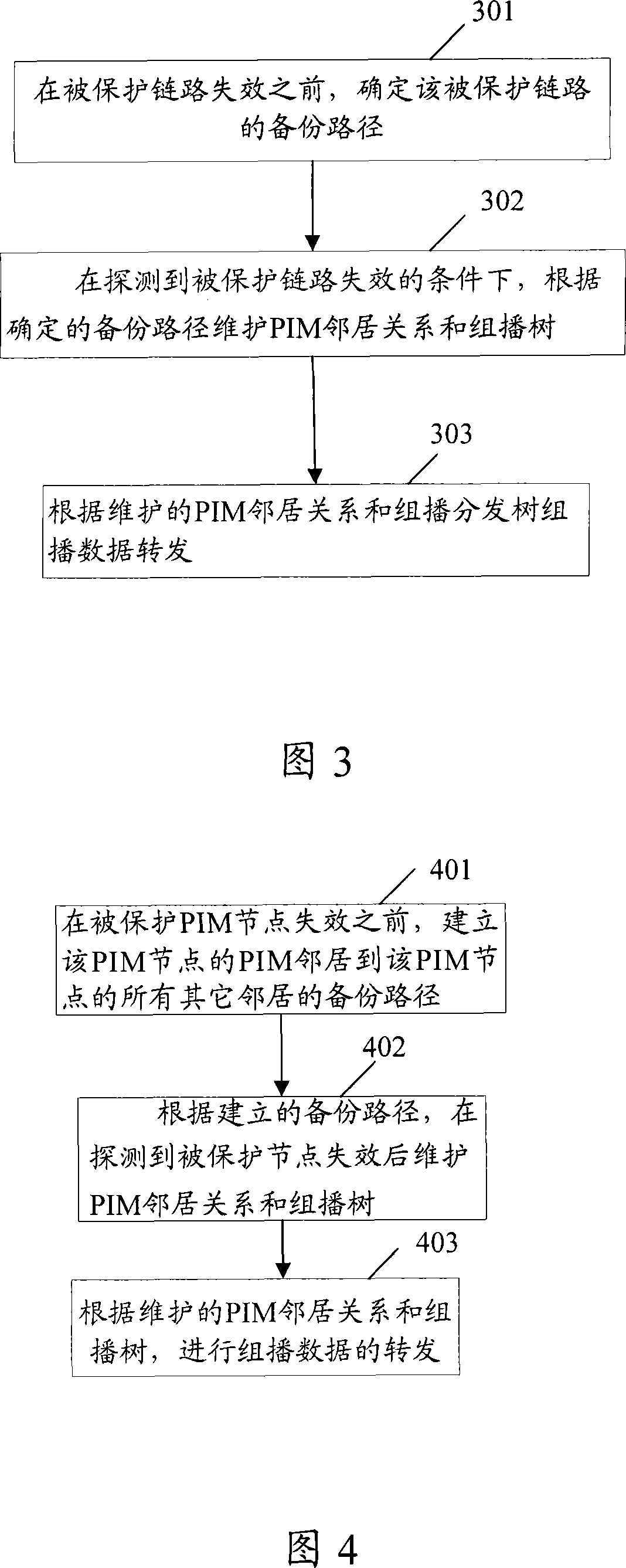
Embodiment 2
[0151] Before the protected PIM node fails, the protected PIM node is a switching point, and multiple downstream network elements are aggregated at the protected PIM node and continue to be sent to the downstream node through the protected node, and vice versa. Usually the state of the multicast tree is maintained in the MRIB of each node, and the MRIB is composed of multiple MRIB multicast routing / forwarding entries. In addition to (S, G), or (*, G), or (*, *, RP) information, each multicast routing / forwarding entry also includes RPT-bit, SPT flag, iif and the corresponding state machine state; the state of the outgoing interface (oif: outgoing interface) and the corresponding state machine.
[0152] Under normal circumstances, the multicast data and PIM protocol messages belonging to a multicast tree are sent to the protected PIM node of the multicast tree, and the protected PIM node is responsible for updating the MRIB entry, and will generate the PIM The response message ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com