Intrusion detection system and method
An intrusion detection system and intruder technology, applied in instruments, electrical alarms, anti-theft alarms, etc., can solve the problems of high maintenance costs and high investment in video detection systems, and achieve strong anti-destructive ability and convenient system construction. , to ensure the effect of concealment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The intrusion detection system and method of the present invention will be further described in detail below with reference to the accompanying drawings. It should be noted that the described embodiments are only intended to facilitate the understanding of the present invention, rather than limiting it in any way.
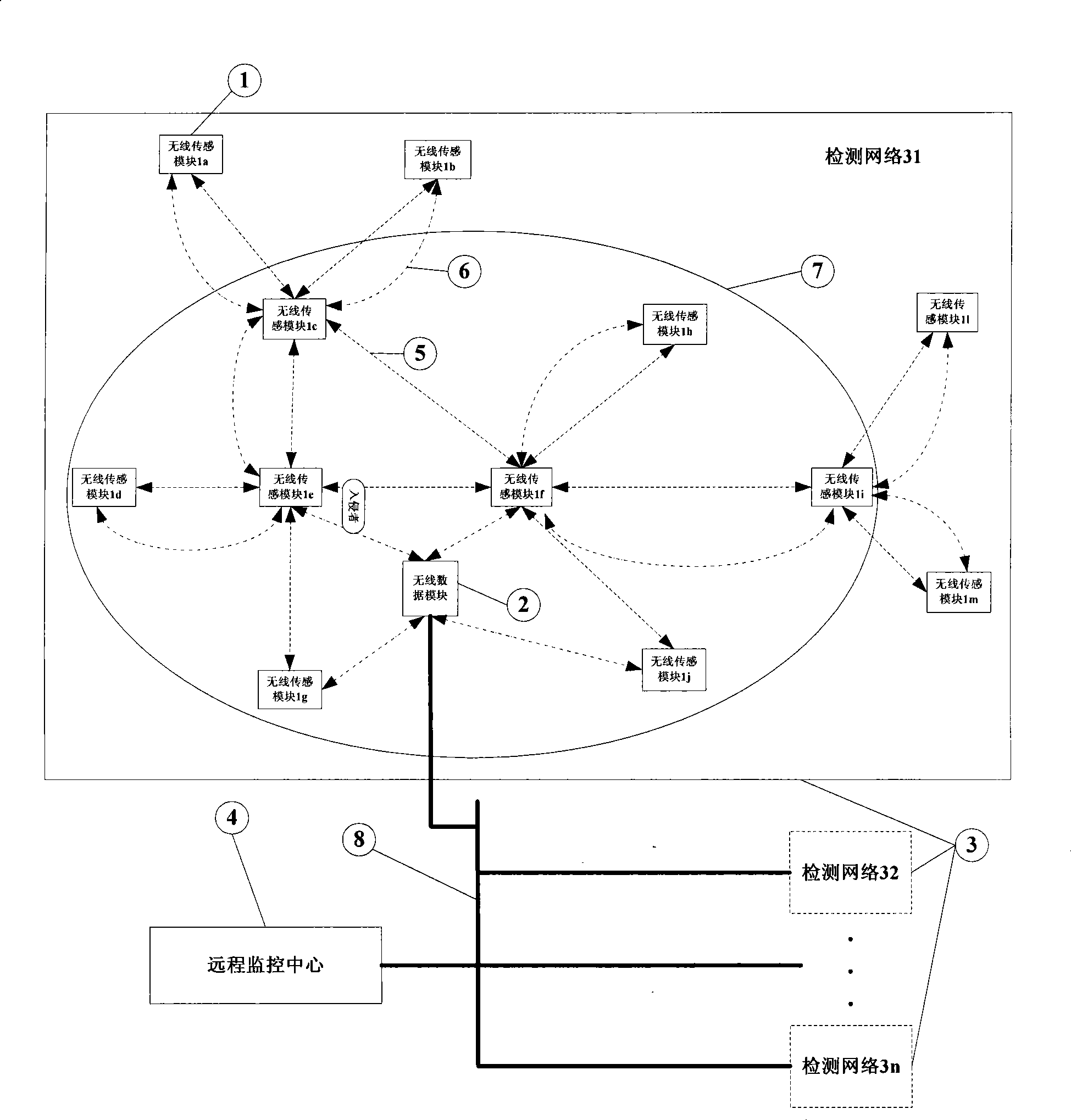
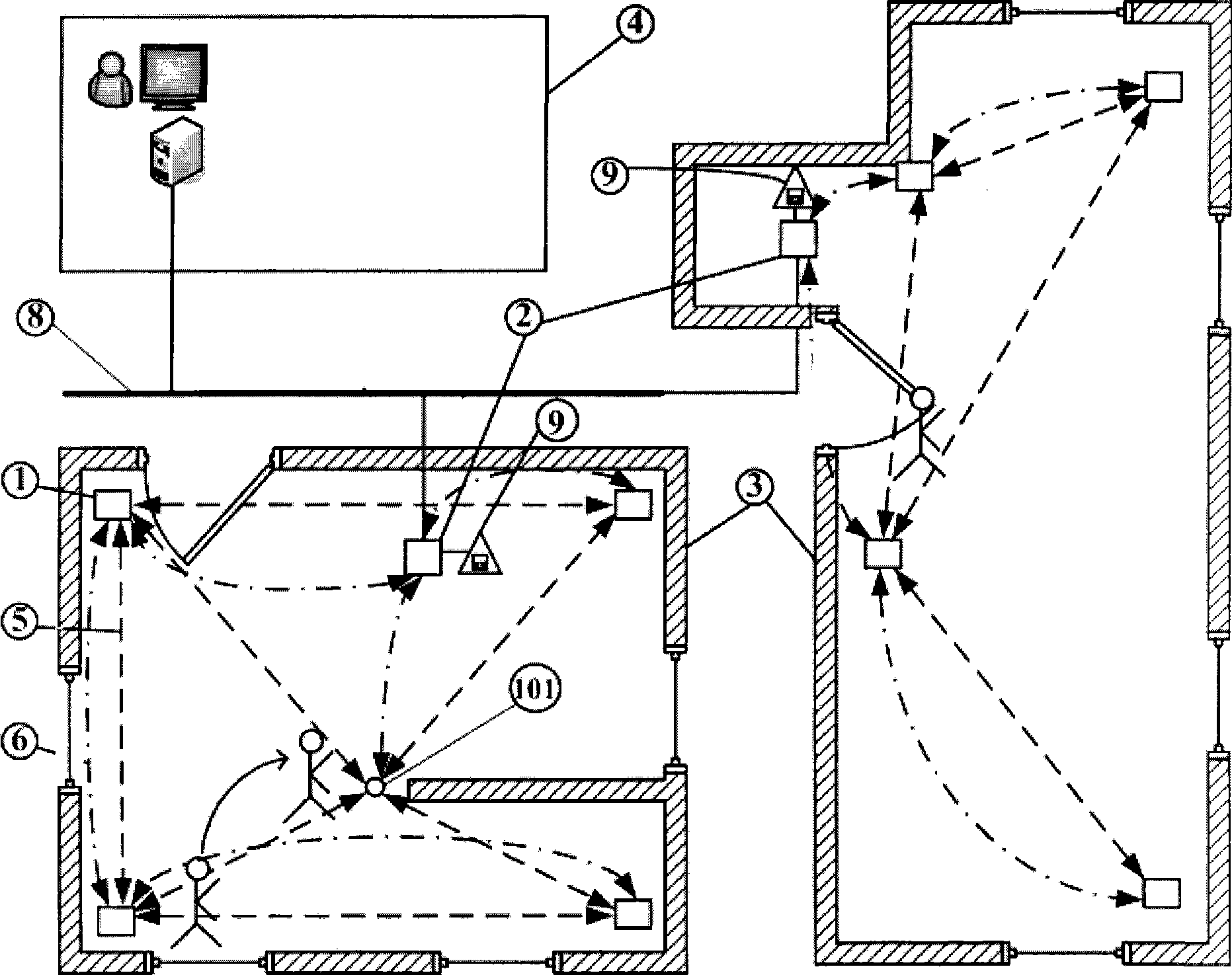
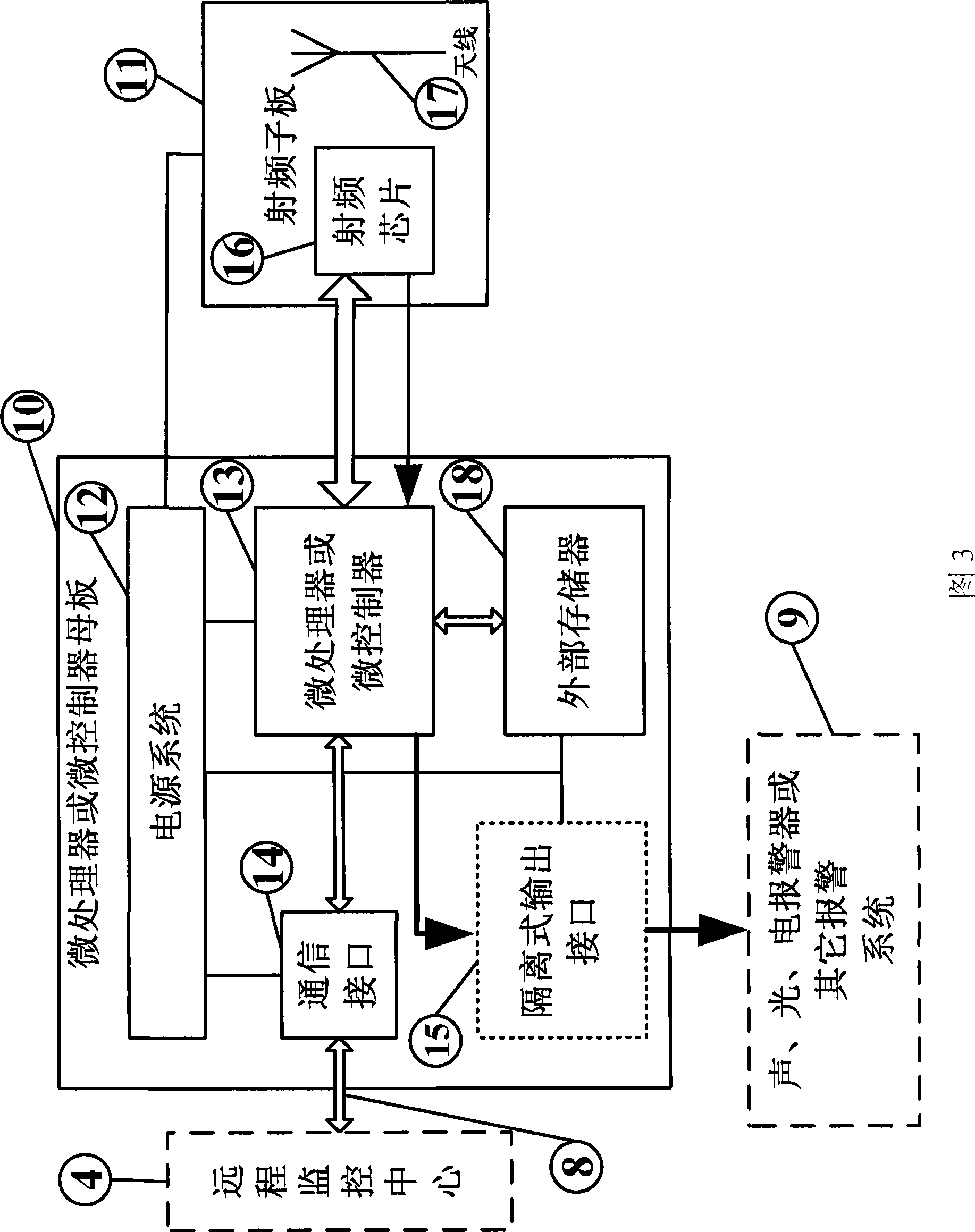
[0049] Such as figure 1 It shows a schematic block diagram of the structure of the embodiment of the present invention, including: detection network 31, detection network 32... The detection network 3n is located in the three-dimensional space of the prevention site 3, n=1, 2, 3... . The detection network is connected to the remote monitoring center 4 through the bus 8, which is used to detect whether there is an intrusion in the coverage area of the detection network and the current approximate location of the intruder; the bus 8 is used to connect the detection networks distributed in different geographical locations to the remote monitoring center 4. Re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com