Method for defending against DDos in address disjunction mapping network
An address and network technology, applied in the network field, can solve problems such as the inability to effectively prevent DDoS attacks, the inability to provide information support for network security technology, and the complexity of computing, to eliminate the possibility of DDoS attacks, and to facilitate deployment and technological innovation. Effects with low computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
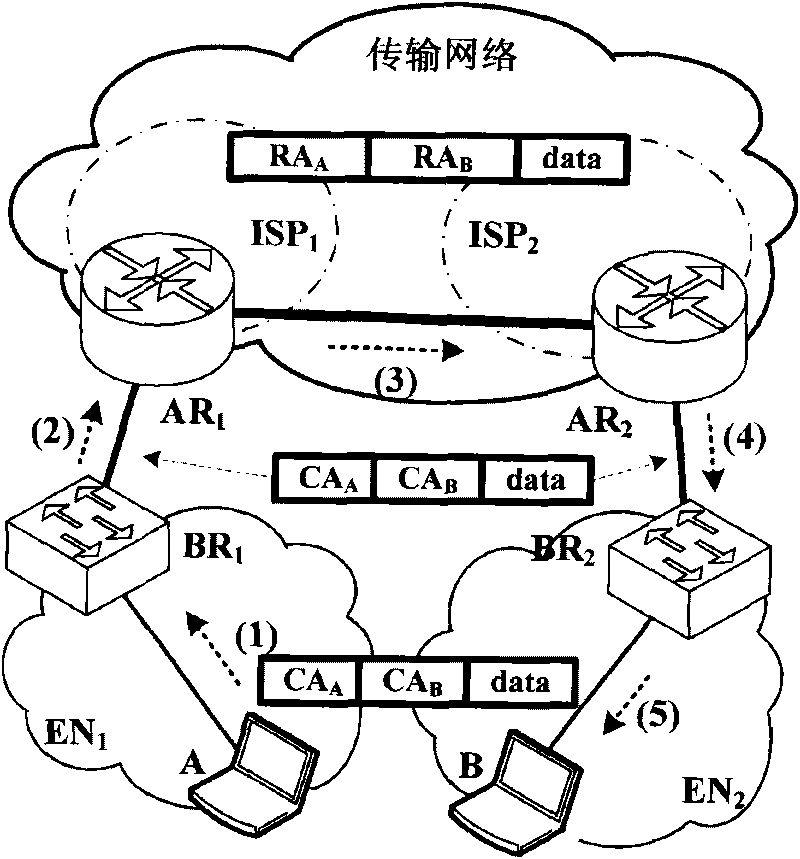
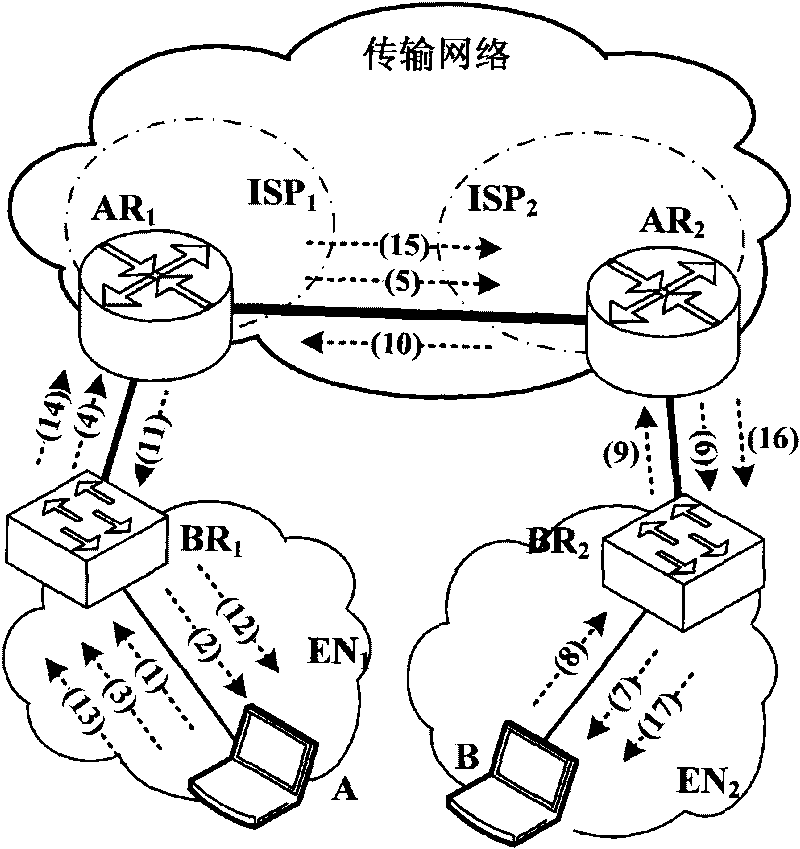
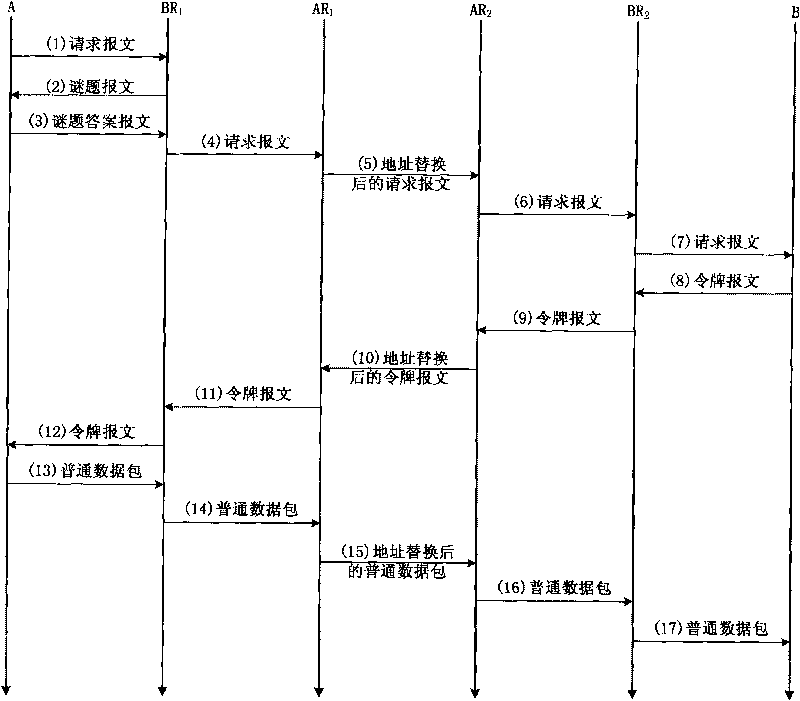
[0063] Such as figure 2 As shown, assume that host A is located in the edge network EN 1 , whose identity is CA A , host B is located in the edge network EN 2 , identified as CA B , and the corresponding routing addresses are RA A and RA B . see image 3 In the flow chart of protocol interaction in the present invention, the steps of the defense method of the present invention are as follows: Step 1: A sends a "request message" P to B request , whose source address is CA A , the destination address is CA B . P request It is an IP data packet with only a header, and in particular, the first bit of its "Flag" field is set to 1.
[0064] Step 2: P request Reaching the Border Router BR 1 After, BR 1 Generate puzzles N, K and package them into payloads P puzzle Send to A. where N is BR 1 A pseudo-random number updated periodically (every 60s), K is BR 1 Puzzle difficulty set according to its load.
[0065] Step 3: P received puzzle Finally, A performs enumerati...
Embodiment 2
[0087] In the deployment of the present invention, it is necessary to expand the functions of some network components in the "address separation mapping" network, mainly including:
[0088] (1) Terminals A and B: support the new access mechanism proposed by the present invention, that is, be able to solve puzzles and send messages (3); support the new token-based flow control mechanism proposed by the present invention, that is, be able to send messages (1) ), receive and process the request message, generate Token, verify the source of the Token, and send data packets according to the content of the Token.
[0089] (2)BR 1 : Support the new access mechanism proposed by the present invention, that is, the pseudo-random number N that can be periodically updated (every 60s), the puzzle difficulty K that can be set according to the load status, and the puzzle that can be generated and sent according to the request message sent by the end user Message (2), can verify the puzzle a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com