Information leakage preventing method and system based on internet of things
An Internet of Things and information encryption technology, applied in the field of information leakage prevention based on the Internet of Things, can solve problems such as security and privacy threats, and achieve the effect of protecting information security, ensuring privacy, and increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
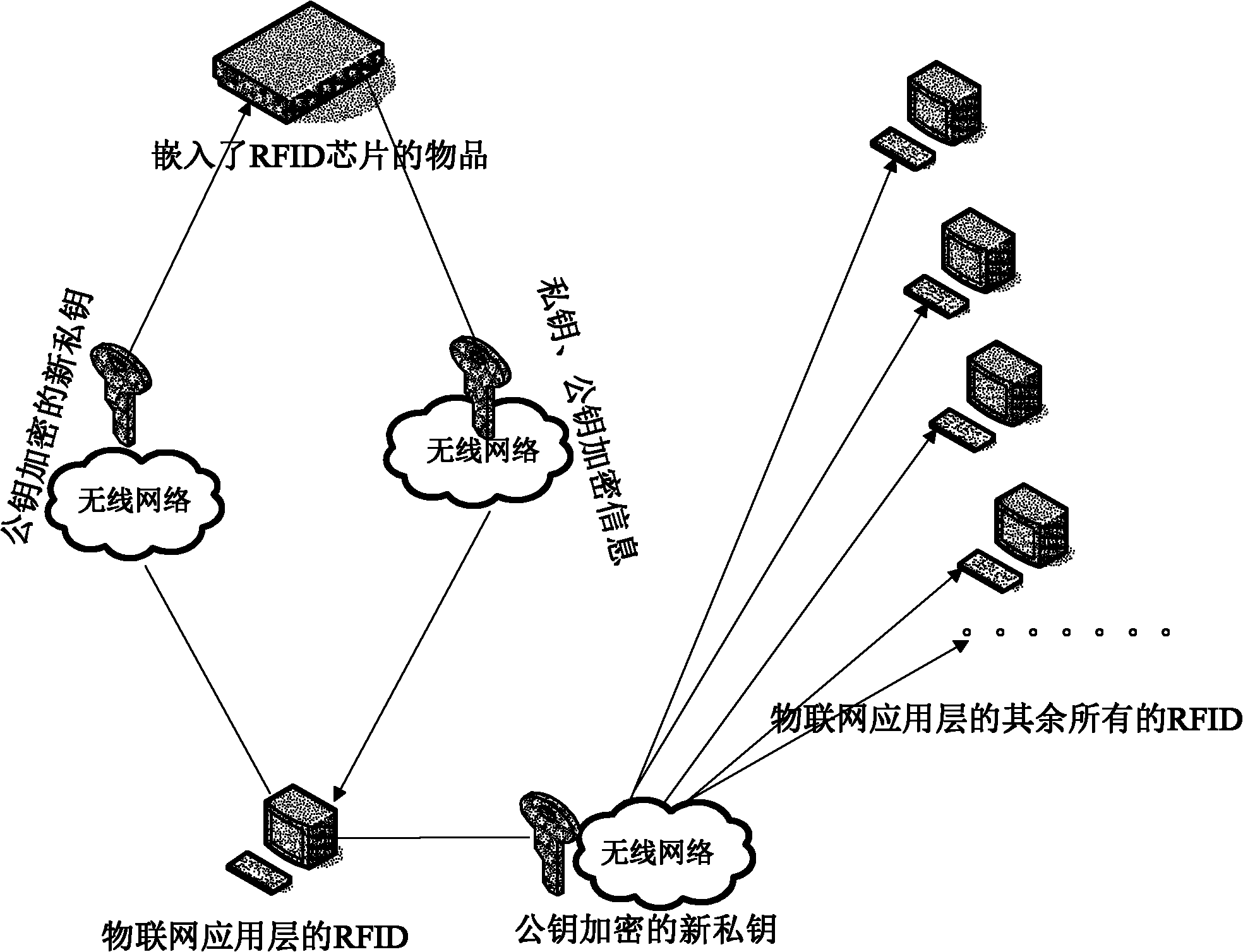
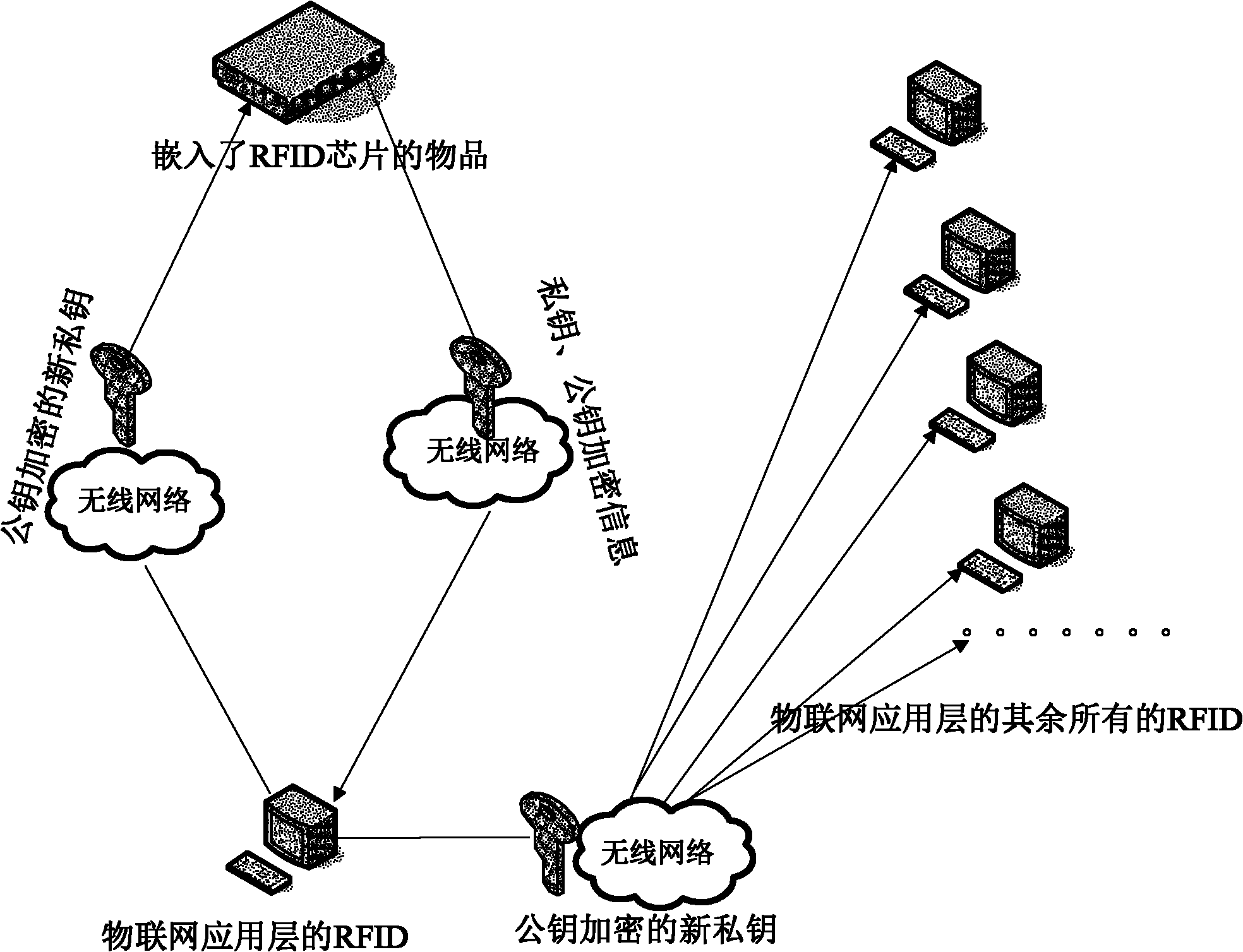
[0049] see figure 1 , the present invention discloses an information leakage prevention method and system based on the Internet of Things, the system uses a public key private key encryption mechanism, and the system includes an RFID chip transponder, a reader at the application layer of the Internet of Things; the RFID chip transponder An electronic carrier that stores the identification information of "things" in the Internet of Things.
[0050] The method includes: the RFID chip transponder encrypts the private key and the public key; the reader at the application layer of the Internet of Things decrypts the public key and the private key, and the reader at the application layer of the Internet of Things generates a new private key; the reader at the application layer of the Internet of Things The reader forwards the new private key to the RFID chip transponder and all other readers of the IoT application layer.
[0051] Encryption mechanism used: When the IoT perception l...
Embodiment 2
[0057] The invention discloses an information leakage prevention method and system based on the Internet of Things. The system includes an RFID chip transponder communicating with each other and a reader at the application layer of the Internet of Things.
[0058] The use of public key and private key encryption mechanisms includes private key and public key encryption for RFID chip transponders (electronic carriers that store the identification information of "things" in the Internet of Things), and public and private key decryption for readers at the application layer of the Internet of Things And every time a new private key is generated, and the newly generated private key is forwarded to the RFID chip transponder and all other readers of the Internet of Things application layer.
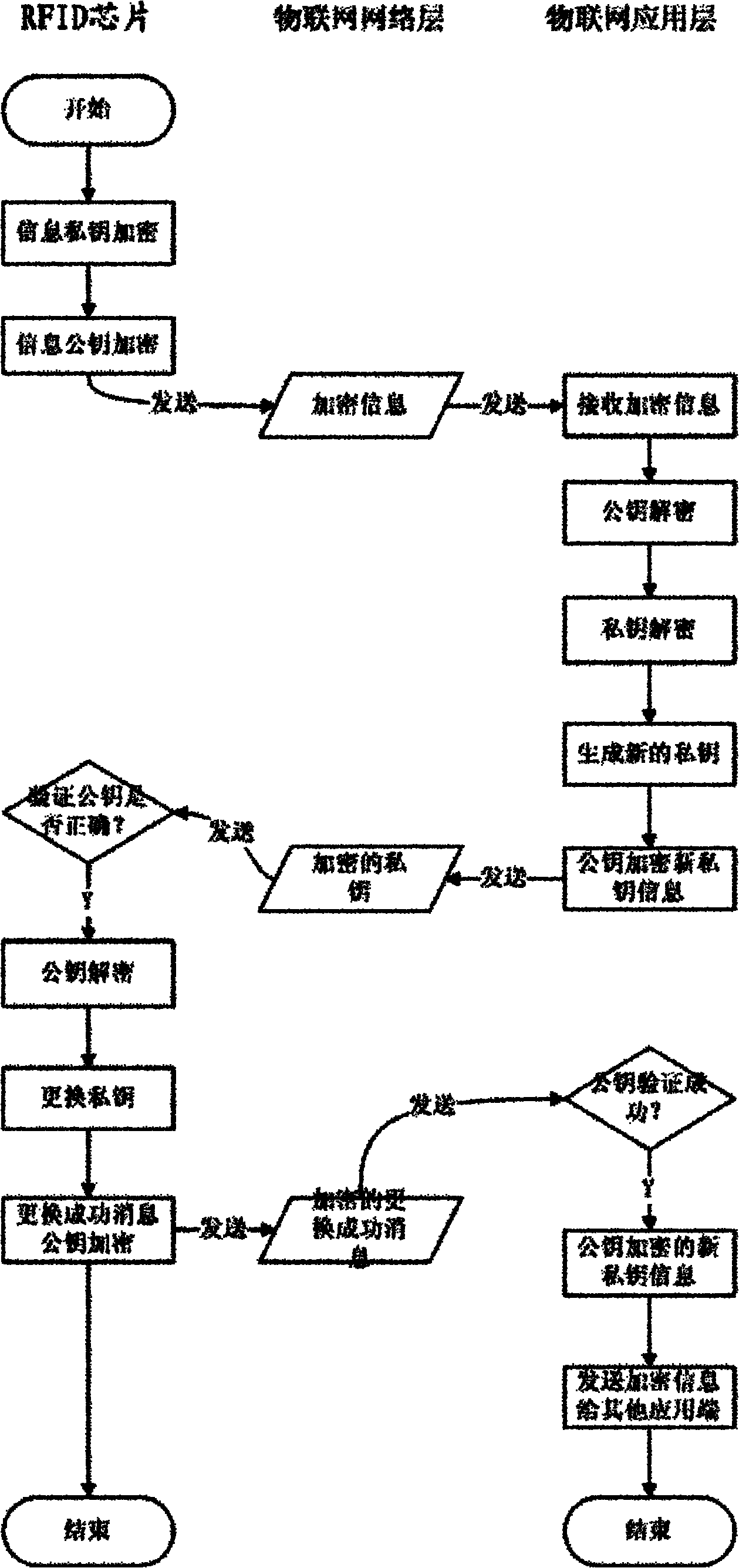
[0059] see figure 2 , the present invention is based on the Internet of Things anti-information leakage method comprising the following specific steps:
[0060] I. The RFID chip transponder in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com