Method for confirming data in CPU (Central Processing Unit) card
A data and technology to be confirmed, applied in the field of information security, can solve problems such as unresolved computer clients, insecurity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0040] [Example 1] SMS confirmation
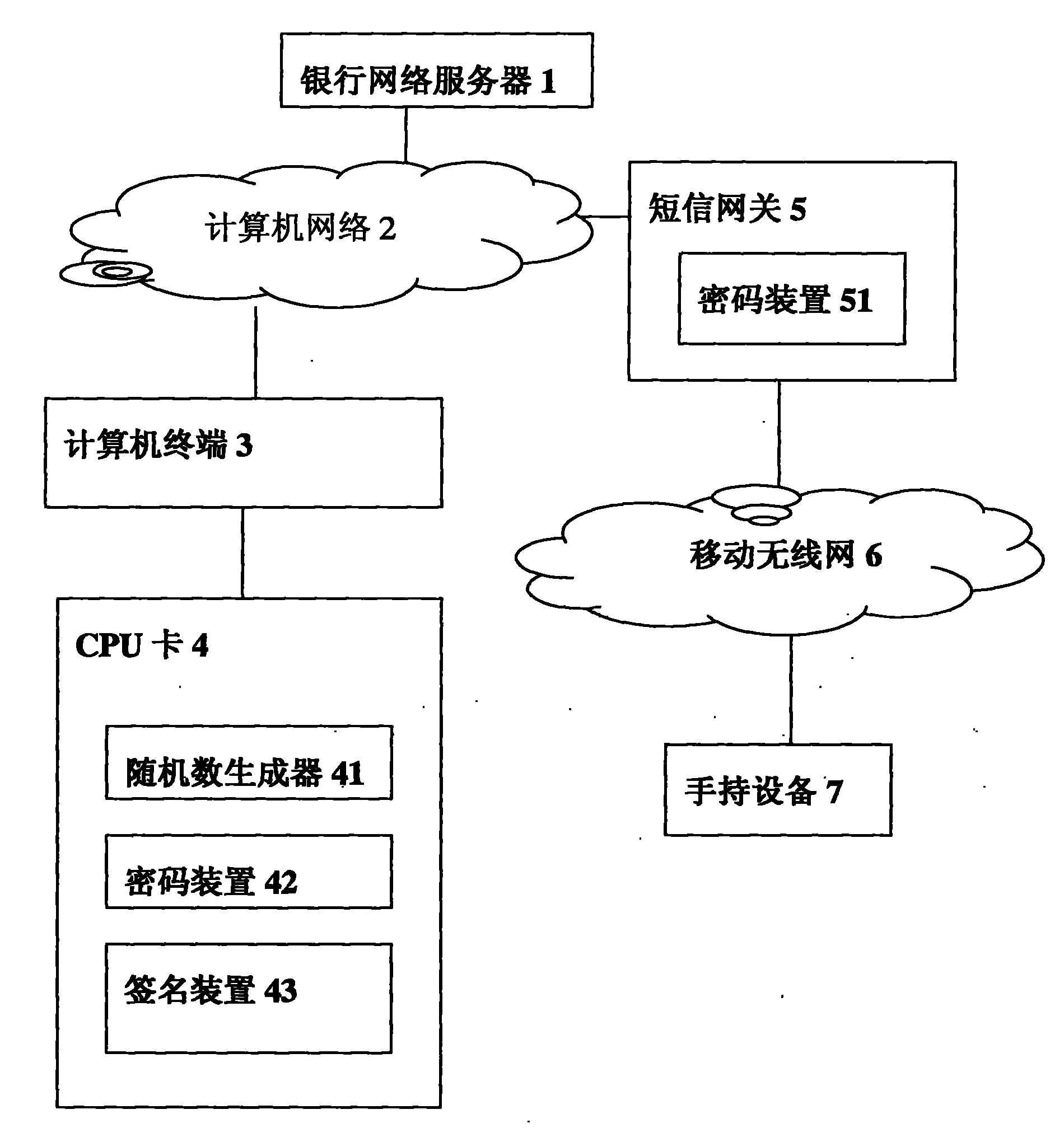
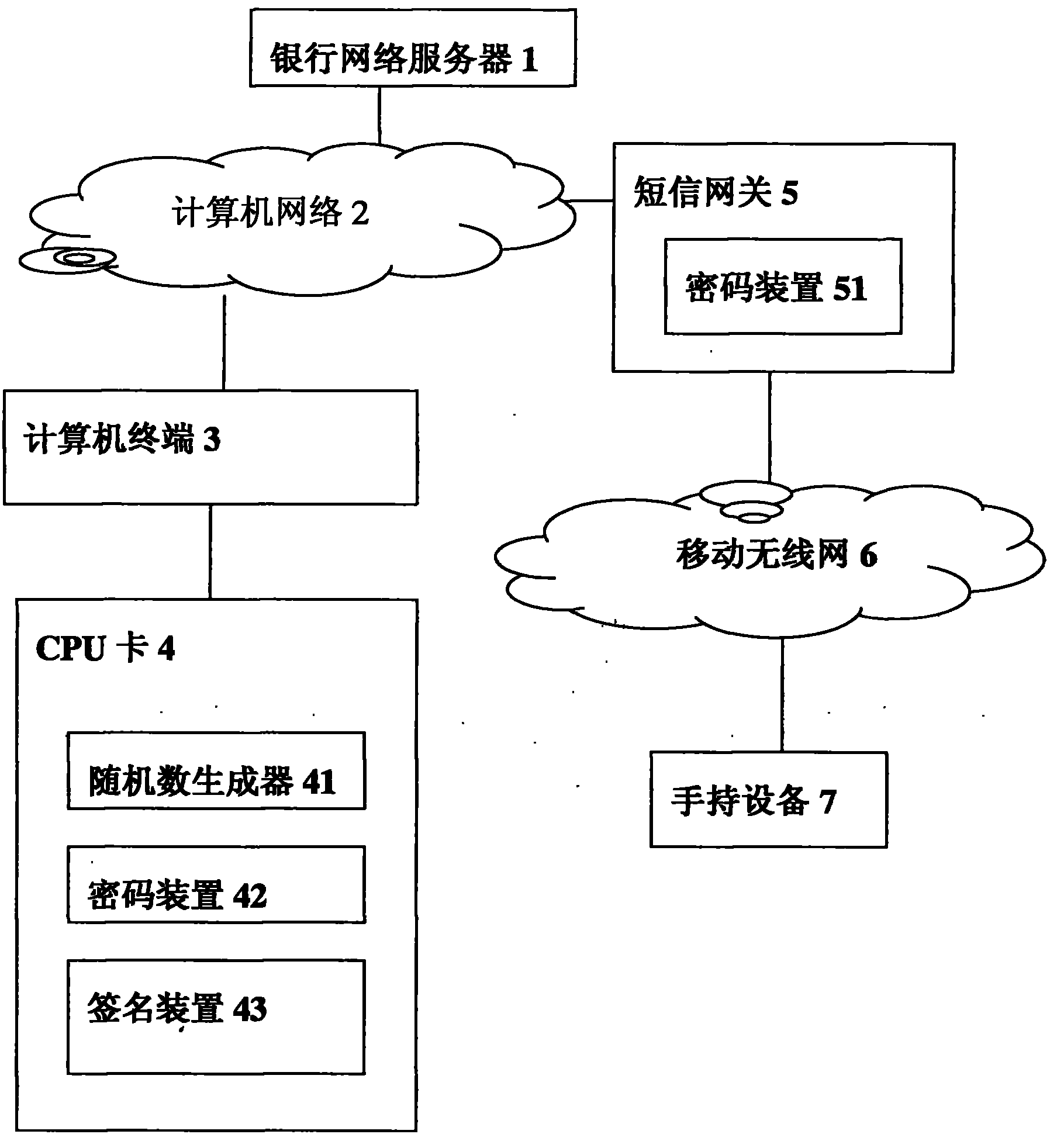
[0041] The core of the present invention is the data to be signed or to be used in the CPU card, which is output to the user's trusted device by a credible method, and the user confirms the data to be signed or to be used; after the user confirms, perform the corresponding signature or use the corresponding data . According to the first embodiment of the present invention, a system associated with a method for confirming data in a CPU card is as follows: figure 1 shown. This is an SMS confirmation scheme. In this figure, the data encrypted by the encryption device 42 corresponds to the encryption device 51 of the SMS gateway 5; that is, the encryption device 42 completes the encryption, and the encryption device 51 decrypts it. For example, cryptographic device 51 discloses the public key (E, M), and keeps secret private key (D, M); then cryptographic device 42 encrypts with public key (E, M), and cryptographic device 51 uses secret pri...
Embodiment 2
[0047] [Example 2] wireless confirmation (dedicated, mobile phone plus SD card, mobile phone plus SIM card)
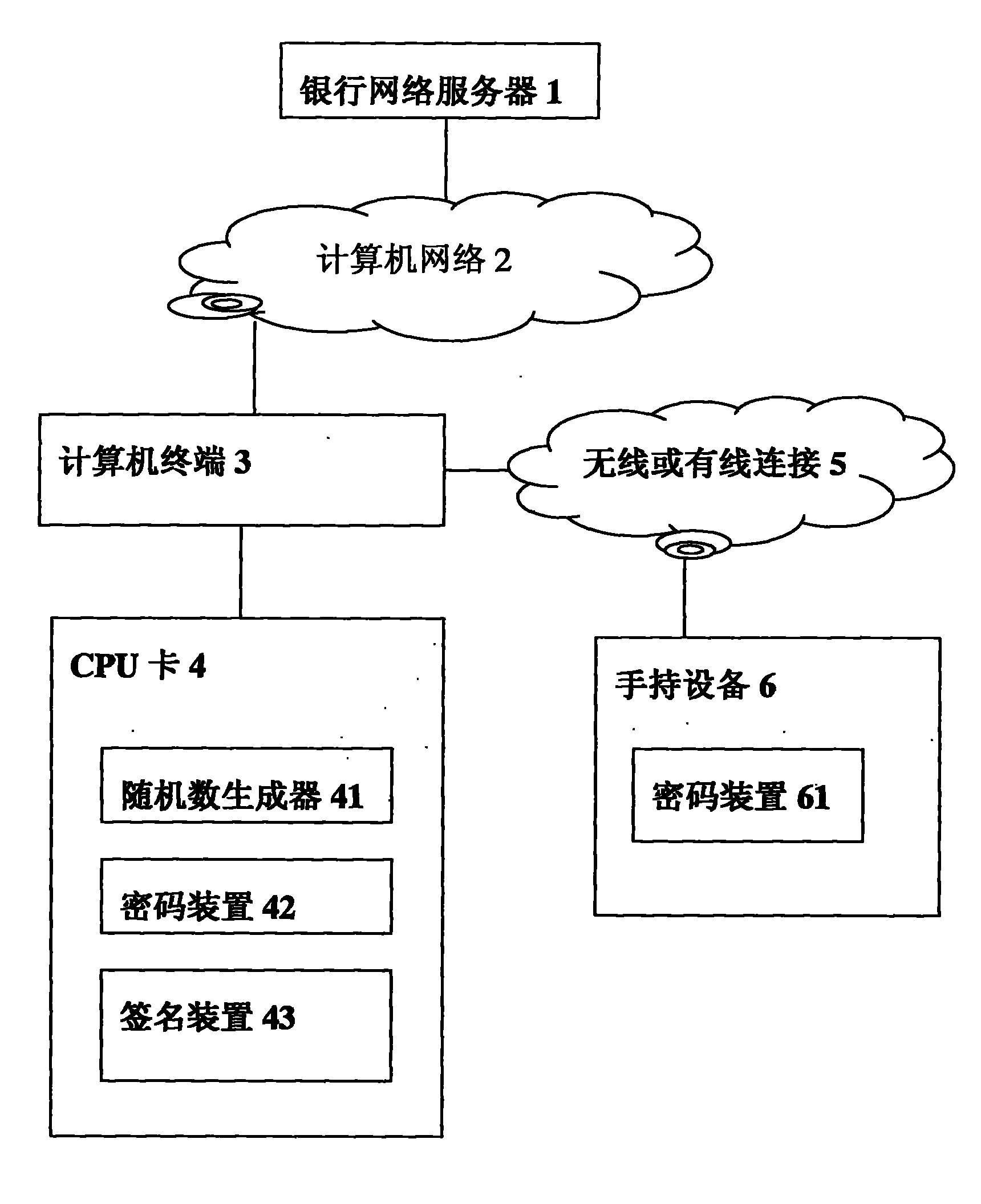
[0048] According to the second embodiment of the present invention, a system associated with a method for confirming data in a CPU card such as figure 2 shown. In this embodiment. The handheld device 6 in this figure can be connected with the computer terminal 3 with a wired connection (such as a USB cable) or a wireless connection (such as bluetooth), and this kind of connection is represented by "wireless or wired connection 5". Connect the CPU card 4 and the handheld device 6 . In addition, if the handheld device 6 is a mobile phone, it is preferable to add an SD card or change a SIM card to add the encryption device 61, and of course the function of the encryption device 61 can also be realized with the mobile phone software.
[0049] After the CPU card 4 is connected with the computer terminal 3, the user inputs or generates transaction key data according to t...
Embodiment 3
[0052] Embodiment 3 graphic confirmation
[0053] According to the third embodiment of the present invention, the core of the present invention is the data to be signed in the CPU card, which is output to the user's trusted device in a credible way, and the user confirms the data to be signed; after the user confirms, the corresponding signature is performed. see figure 1 to illustrate this method.
[0054] After the CPU card 4 is connected with the computer terminal 3, the user inputs or generates transaction key data according to the prompt of the computer terminal 3, such as key data such as the account name, account number, and amount of funds received; the computer terminal 3 transmits these key data to the CPU In card 4; CPU card 4 generates confirmation password (PIN) with random number generator 41, and this confirmation password and key data are generated figure (as JPEG format), and disturb and make it difficult for computer to recognize, and people can recognize ....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com