Trusted computing based white list static measurement method
A measurement method and trusted computing technology, applied in computing, computer security devices, instruments, etc., can solve problems such as not updating the virus database in time, time-consuming matching check abnormalities, blacklist expansion, etc., to avoid finding malicious programs and codes , ensure safe and stable operation, and prevent malicious code and other attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The specific embodiments of the present invention will be further described in detail below with reference to the accompanying drawings.
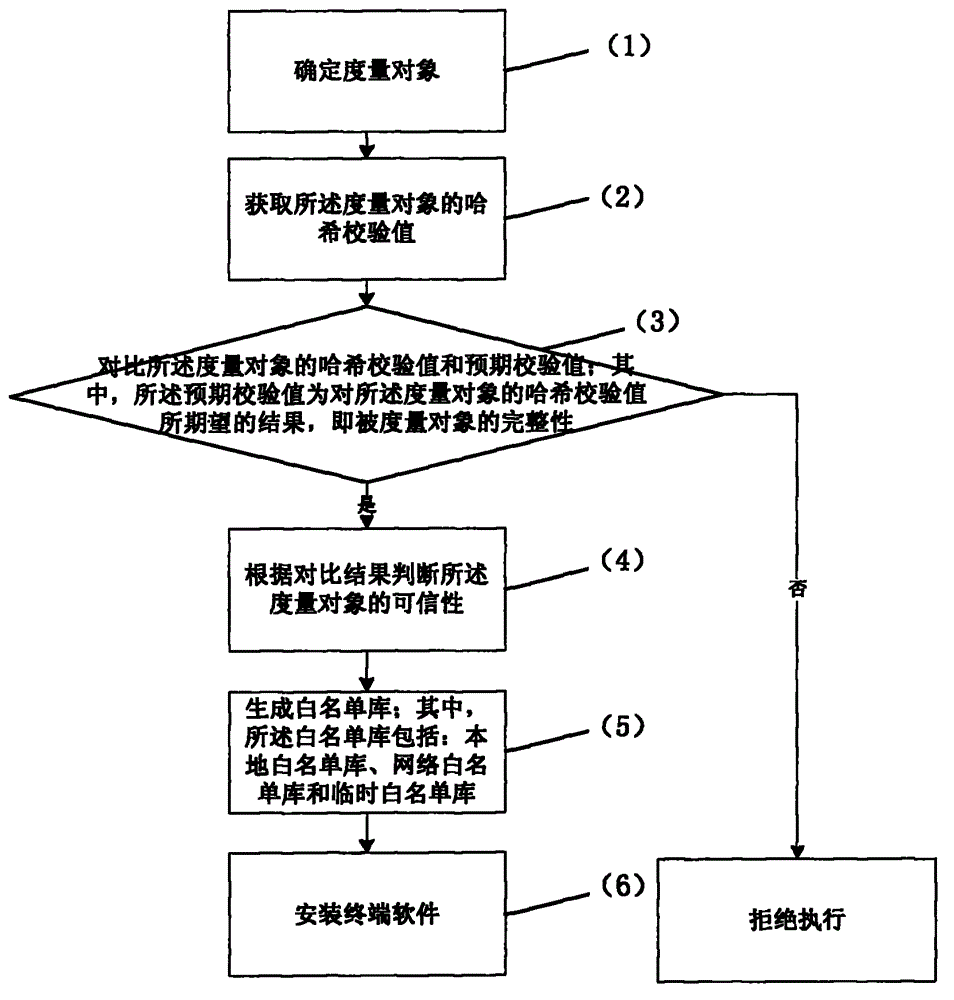
[0043] like figure 1 As shown, a whitelist static measurement method based on trusted computing, the method includes:
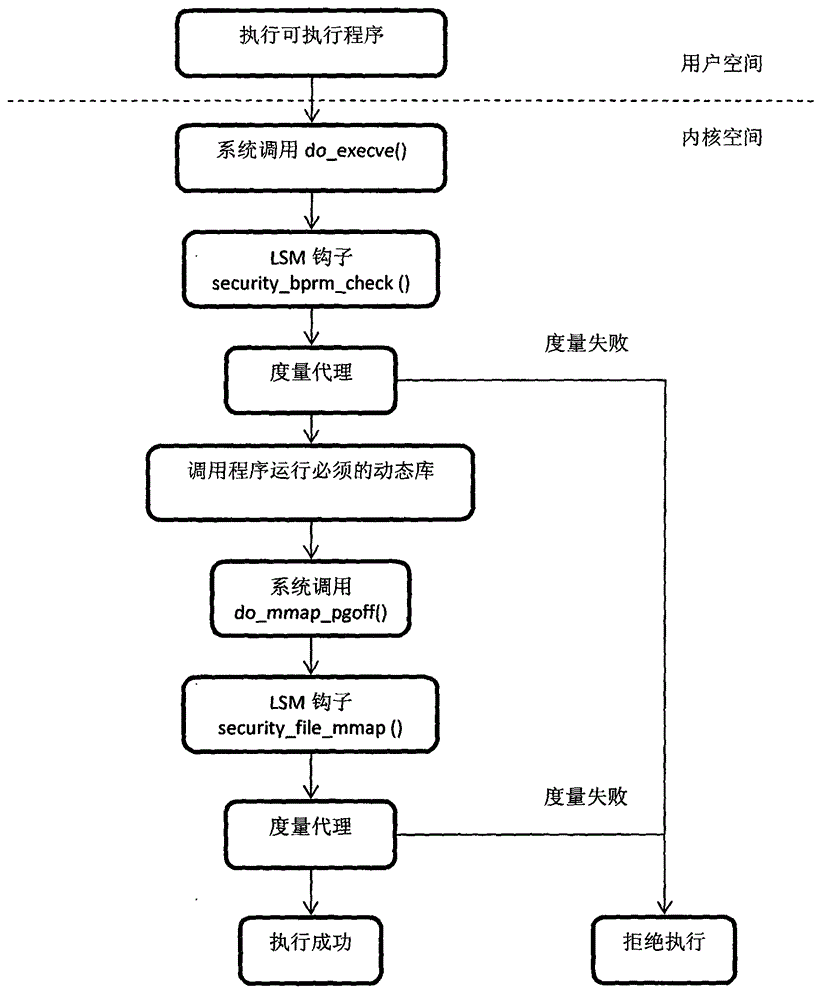
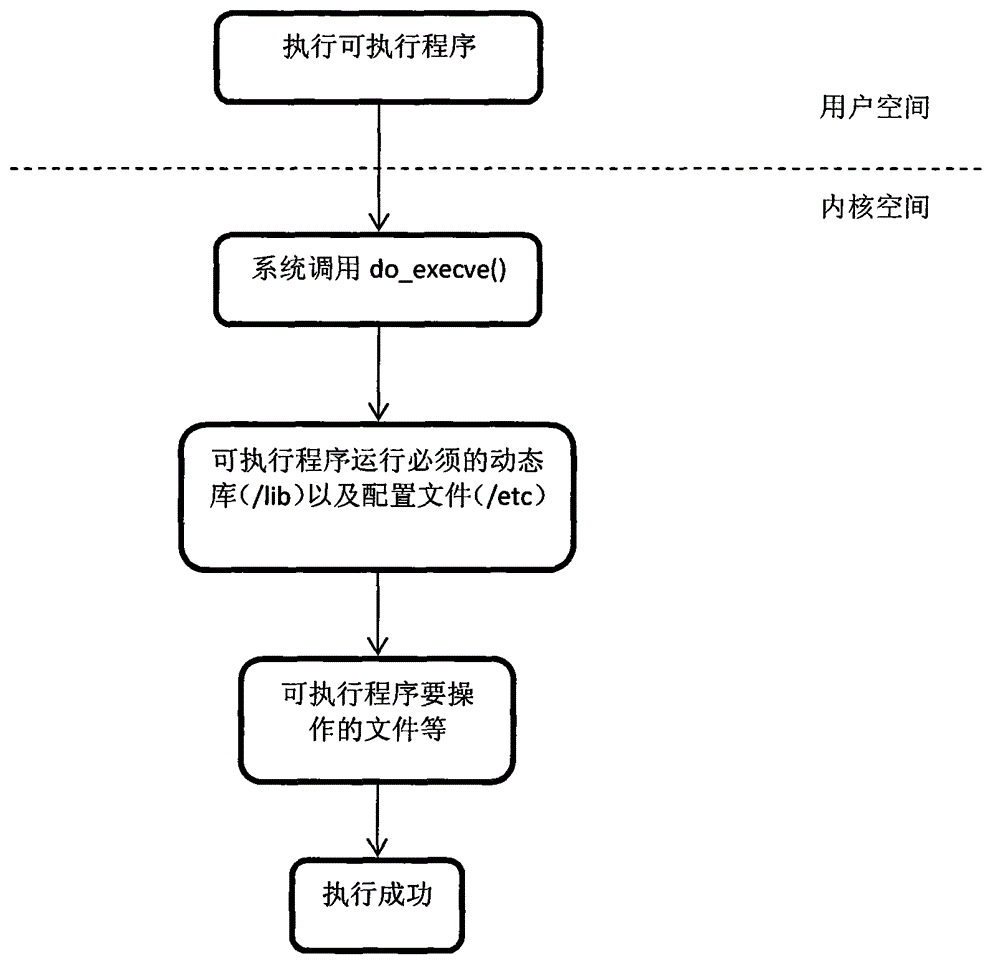
[0044] combine Figure 2-3 As shown, (1) determine the measurement object; in the step (1), the measurement object includes an executable program, a dynamic library and a kernel module.
[0045] (2) Obtain the hash check value of the measurement object; as Figure 5 As shown, the step (2) includes: obtaining the parameter value of the executable program, sending it to the static measurement agent, and calculating the hash check value of the executable program.
[0046] When calling the subroutine created by the fork system and executing the execve system to load a new executable program, call do_execve (), the parameter value of the executable program is sent to the kernel and encapsulated in the struct linux_bi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com