A hybrid access selection method for macro-femto network based on cloud computing
A hybrid access and cloud computing technology, applied in network planning, advanced technology, climate sustainability, etc., can solve problems such as unreasonable hybrid access selection strategies, save power consumption, suppress interference levels, and reduce latency and the effect of packet loss rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
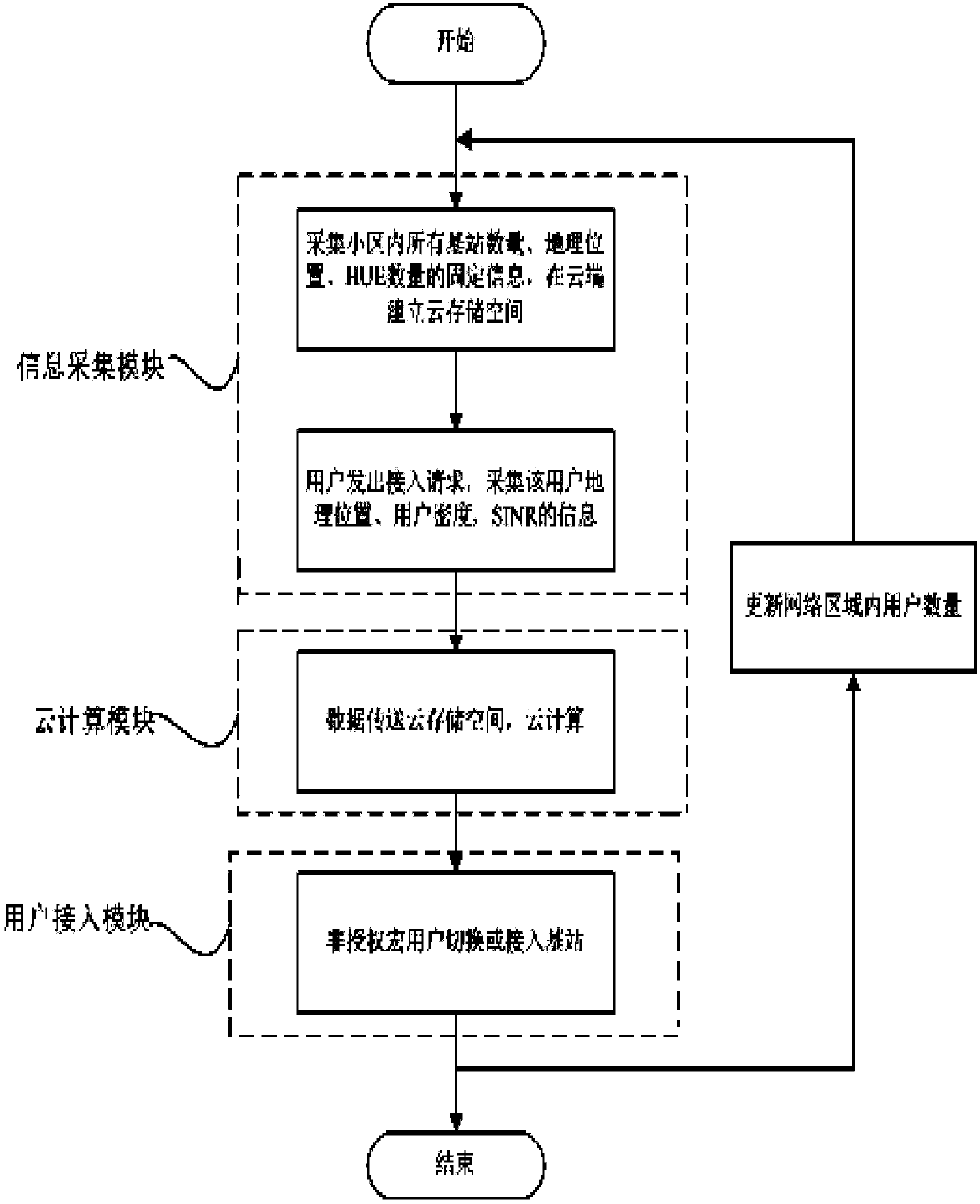
[0024] Embodiment 1 Information collection process of the present invention
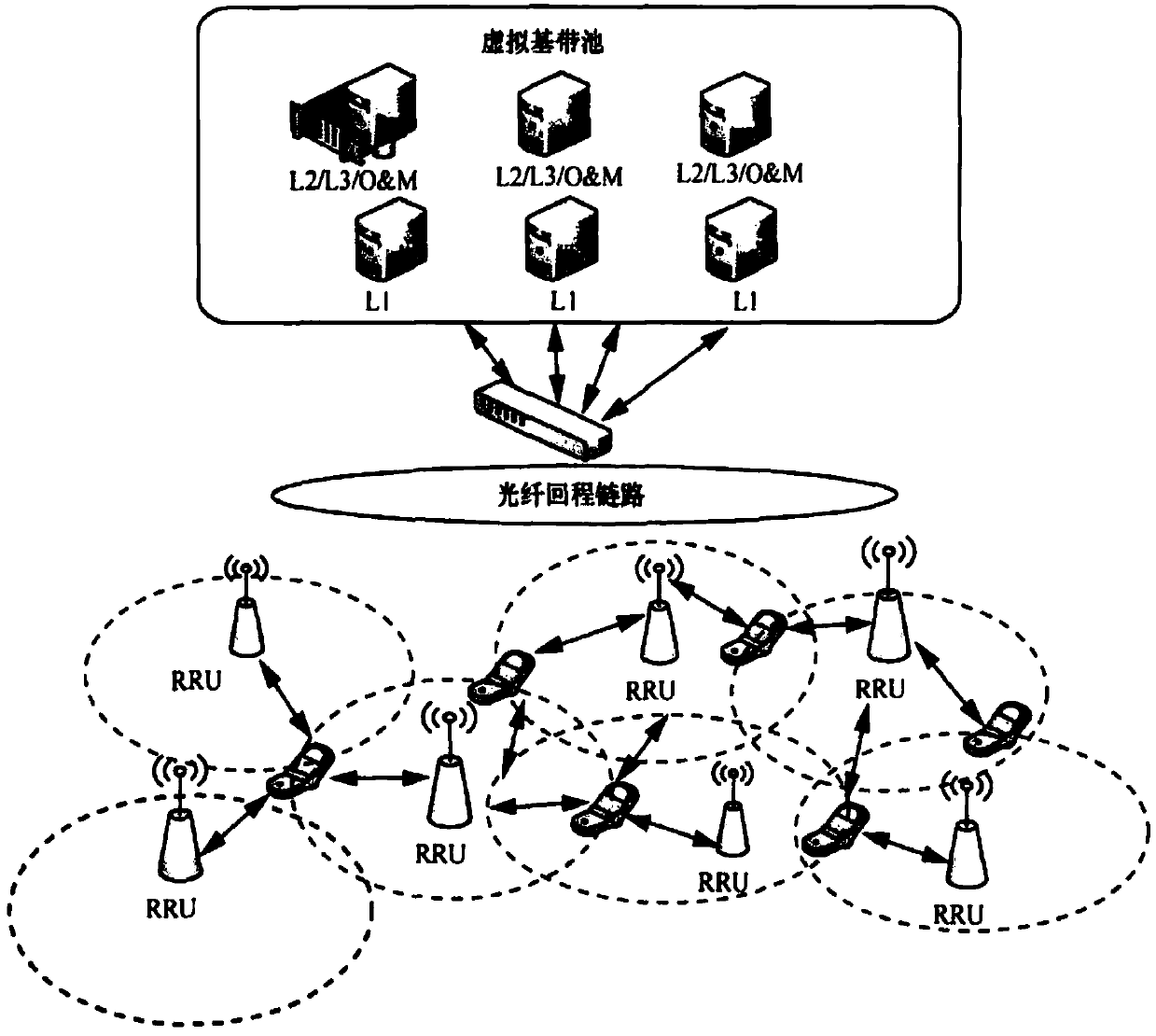
[0025] refer to figure 1 , the present invention is a hybrid access selection method of a macro-femto network based on cloud computing. In this embodiment, the collection of data is through a base band unit (Base Band Unit, BBU) and a remote radio unit ( Remote Radio Unit (RRU), RRU is responsible for digital-to-analog conversion of data and radio frequency transmission and reception, and BBU concentrates all digital baseband processing functions. The BBU is placed in the centralized storage cabinet, while the RRU is placed at the coverage point, using the existing equipment room resources to cover the surrounding area three-dimensionally. The RRU is connected to the BBU through an optical fiber or an optical fiber transmission network, and the RRU can be deployed at a remote site (such as 1-10Km) away from the physical location of the BBU. To facilitate deployment, the RRU is designed to be small ...
Embodiment 2
[0026] Embodiment 2 The cloud computing process of the present invention
[0027] Taking the rate that each base station can provide for macro users as the selection standard, the cloud calculates the service rate that each FBS can provide for macro users based on the geographical location, occupied bandwidth, and interference level of the FBS. The minimum rate required by a macro user to meet the basic communication needs, expressed in demand throughput. Only base stations that provide a service rate greater than the minimum rate required by macro users are considered as candidate access base stations, and the cloud finally selects the base station that provides the highest service rate among the candidate base stations as the access base station. The calculation of the supply throughput and demand throughput is determined according to the formula (1), and the SINR in the formula (1) is determined according to the formula (2).
[0028]
[0029]
[0030] Among them, N ...
Embodiment 3
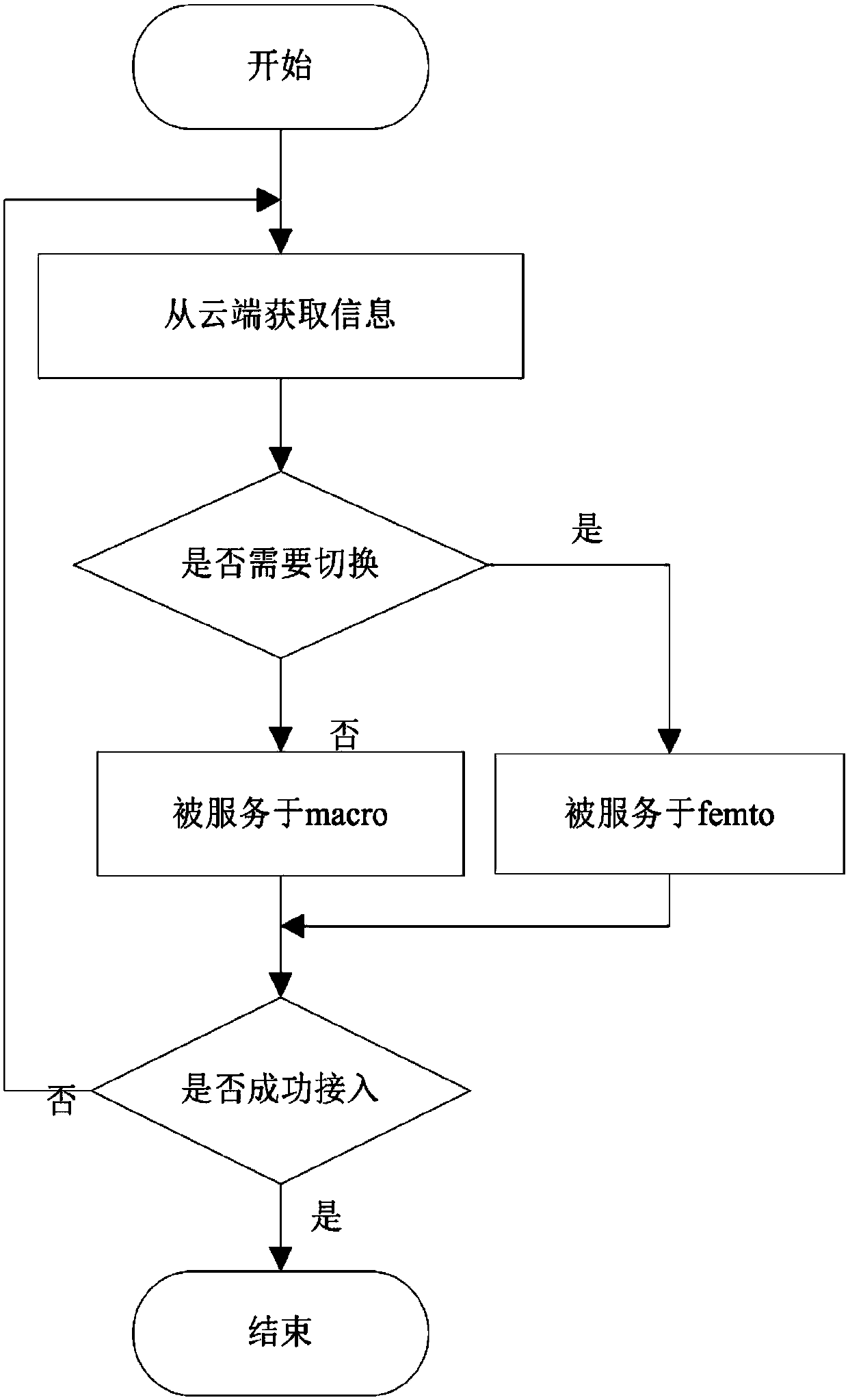
[0034] Embodiment 3 The specific process of user access in the present invention
[0035] image 3 It is a flow chart of user access in the present invention, and the specific access process steps of an unauthorized user are:
[0036] Step 1: The unauthorized macro user waits for the access information fed back from the cloud after sending the access request.
[0037] Step 2: Access according to the allocated base station, if the allocated access is a femtocell, switch to the allocated femtocell, if the allocated access is a macrocell, no switching is required.
[0038] Step 3: If the user drops or is interrupted midway, the request needs to be sent again, and the cloud will allocate base station access again; if the access is successful until the user's service ends, the access is completed.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com