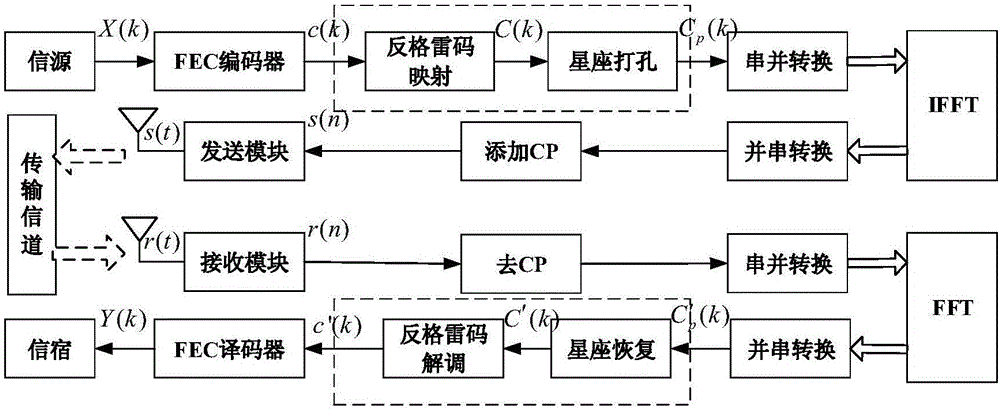
Method for reducing safety gap of COFDM system
A technology of safety circle and constellation point, which is applied in the field of reducing the safety circle of COFDM system, can solve the problems of large safety circle, low signal-to-noise ratio, narrowing of the safety circle, etc., and achieve less restrictions, good safety performance, and reduce the system safety circle Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0037] This embodiment takes the 16QAM (Quadrature Amplitude Modulation) constellation modulation mode as an example to describe in detail the specific method for reducing the security margin of the C-YP-OFDM system.
[0038] Step 1, the information source outputs the information bit stream X(k), uses the FEC encoder to perform channel coding on X(k), and obtains the codeword sequence c(k);
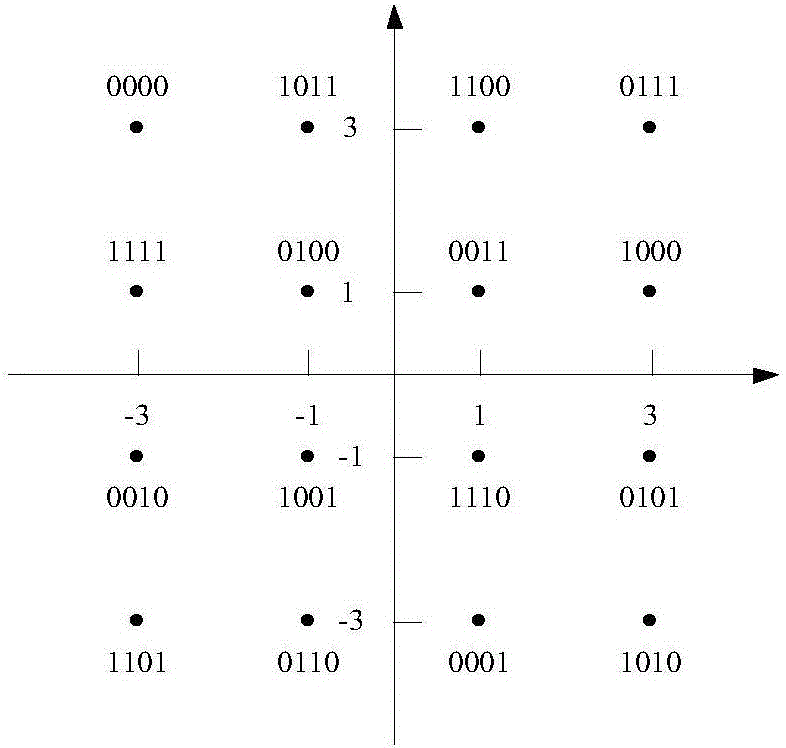
[0039] Step 2: Perform inverse Gray code mapping on the codeword sequence c(k) to obtain the complex symbol sequence C(k), construct a 4-bit inverse Gray code, and map it to the constellation map to form a 16QAM inverse Gray code constellation map , specifically as figure 2 shown.
[0040] Step 3: Select the punctured constellation point Q for the complex symbol sequence C(k) according to the 16QAM inverse Gray mapping constellation diagram w Perform constellation punching and zeroing and output symbol sequence C p (k);
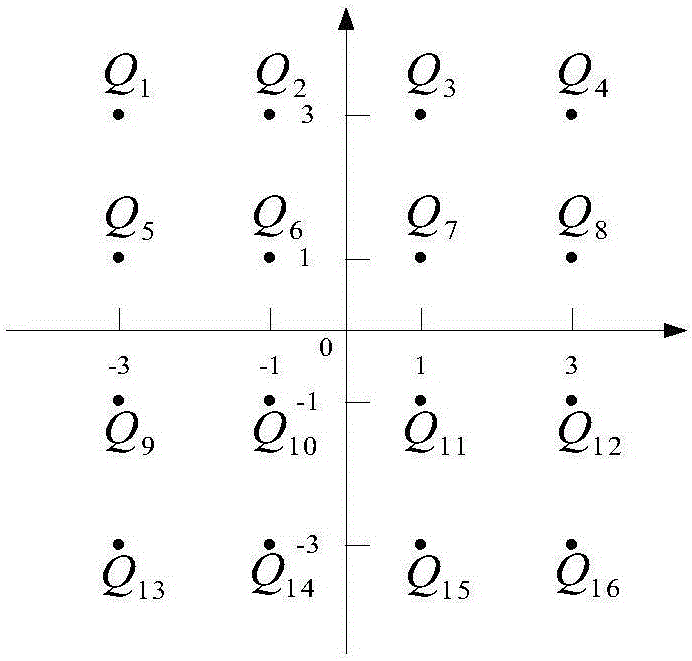
[0041] Will figure 2 Each constellation point in corresponds...
Embodiment 2
[0055] Choose LDPC code as the forward error correction code to form the LDPC-YP-COFDM security system, specifically select the QC-LDPC code defined in the 802.16e standard and the RU fast coding algorithm, and the decoding scheme uses Log -BP joint decoding algorithm, the LDPC code length is 2304, the code rate is 1 / 2, the number of decoding iterations is 10, the number of subcarriers of OFDM is 576, and the 16QAM constellation modulation method is selected. The recovery threshold ε under this constellation mapping is 0.1.
[0056] For various constellation mapping methods, the constellation diagrams are symmetric. Therefore, when each constellation point with the same Euclidean distance is selected as the perforated constellation point, the result of the security boundary is the same. Therefore, this Embodiment random from the constellation point candidate set {Q with the largest Euclidean distance 1 ,Q 4 ,Q 13 ,Q 16} select Q 16 When the constellation point is used as ...
Embodiment 3
[0061] The existing representative three security methods, a: perforated LDPC security coding method (see literature [1] for specific methods, Klinc D., Ha J., Mclaughlin S.W., et al.LDPC codes for physical layer security[ J].University of Windsor,2009), b: add disturbance matrix method (see literature [2] for specific methods, Baldi M., Bianchi M., Chiaraluce F..Non-systematic codes for physical layersecurity[C] / / Information Theory Workshop (ITW), 2010IEEE.IEEE, 2010:1-5), c: Inverse Gray code mapping method (see literature [3] for specific methods, Kwak B.J., Song N.O., Park B., et al.PhysicalLayer Security with Yarg Code[C] / / Proceedings of the 2009First International Conference on Emerging Network Intelligence.IEEE Computer Society, 2009:43-48) and the traditional LDPC-COFDM system were compared with the C-YP-COFDM algorithm of the present invention, and the specific results are shown in Table 2. Among them, both methods a and b are designed to reduce the system security bo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com