Industrial control system anomaly detection method based on dual-contour model
An industrial control system, anomaly detection technology, applied in general control systems, control/regulation systems, testing/monitoring control systems, etc., can solve problems such as wrong decision-making by enterprise management, poor security awareness, and difficult to detect attacks, and achieve Improve accuracy and improve real-time effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
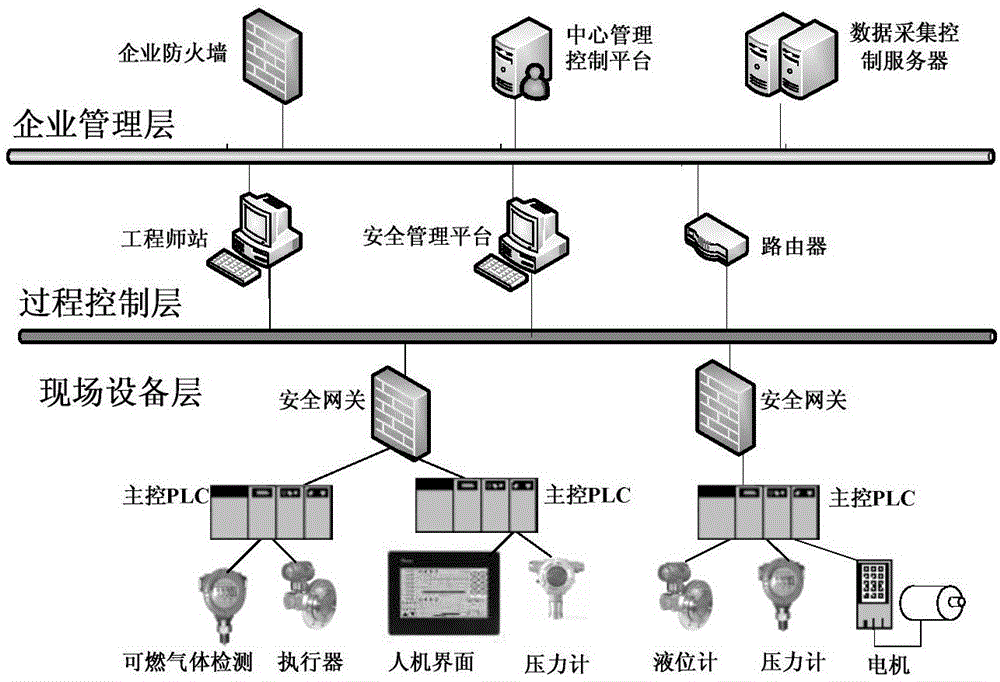
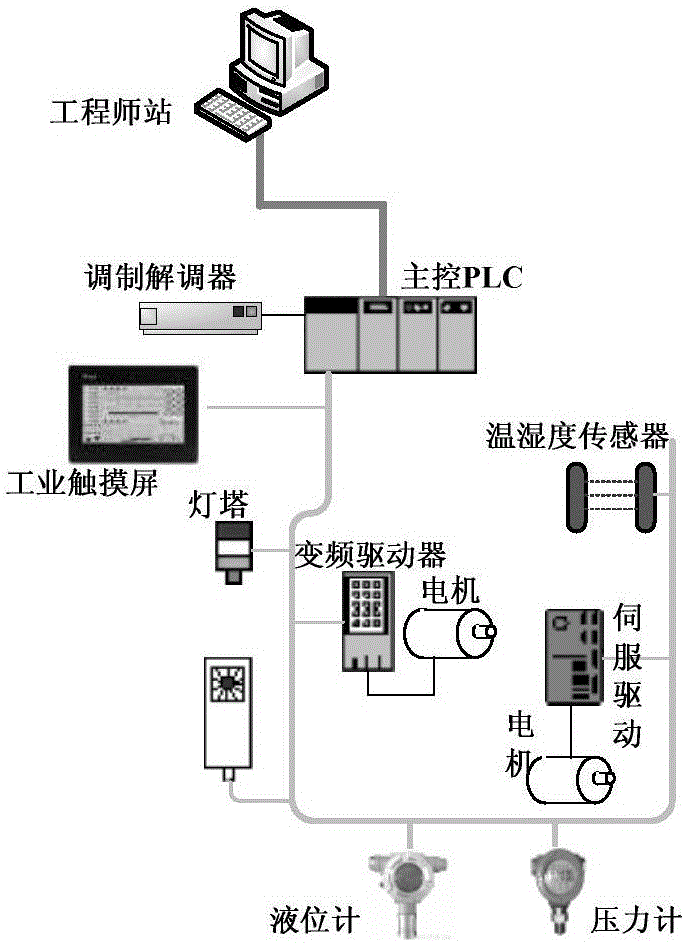
[0054] The ICS anomaly detection method based on the dual-contour model mainly involves the following three modules: data packet deep analysis system, anomaly detection subsystem, and security management platform.
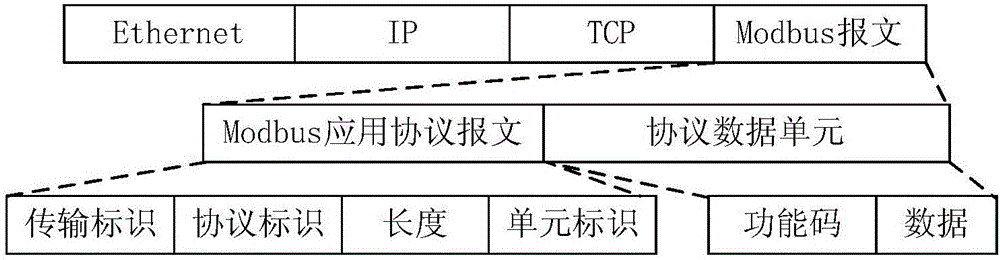
[0055] The data packet deep analysis system is to deeply analyze the message layer by layer. Regarding the Modbus application protocol message header, it includes the transmission identification, protocol identification, length and unit identification, as well as the periodic characteristics of the marking function code, and summarizes the characteristics of each protocol. Command and status characteristics, and record the communication behavior frequency according to the master-slave communication cycle.
[0056] The anomaly detection subsystem conducts real-time data analysis based on the information from the data packet deep analysis system, and constructs the characteristics of the transaction identifier frequency, read slave station function code frequency, wri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com