T-BOX information security detection and protection method based on vehicle anomaly data monitoring
A technology of abnormal data and information security, applied in the field of automobile information security, can solve the problems of economic loss, lack of information security protection ability, user privacy exposure, etc., to achieve the effect of online upgrade
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the drawings and specific embodiments.
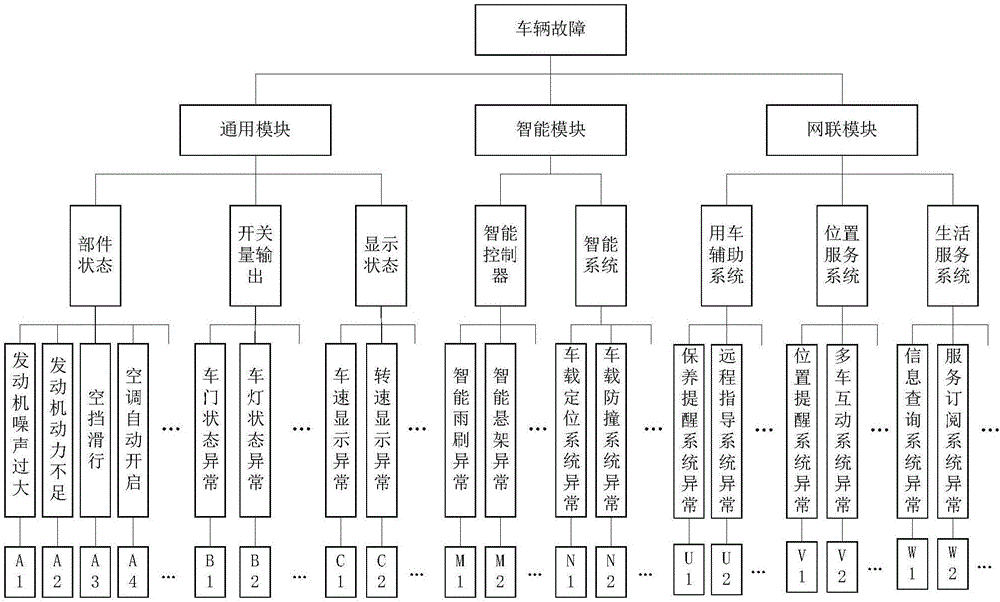
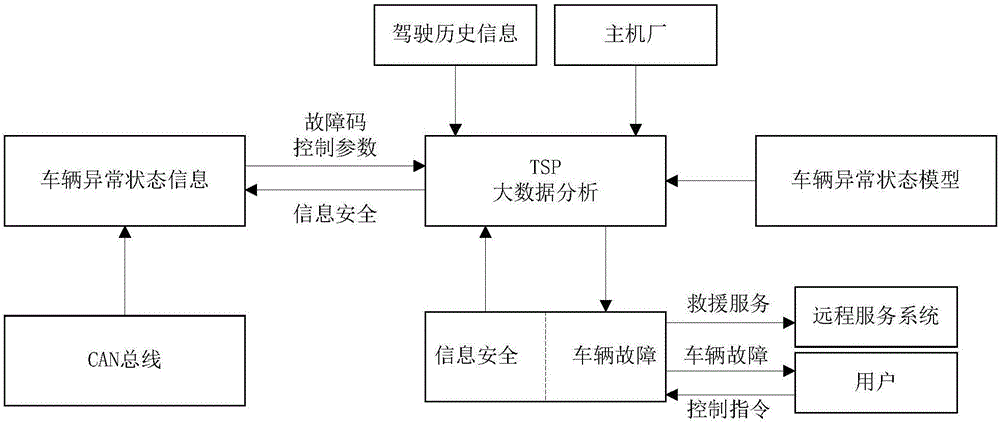
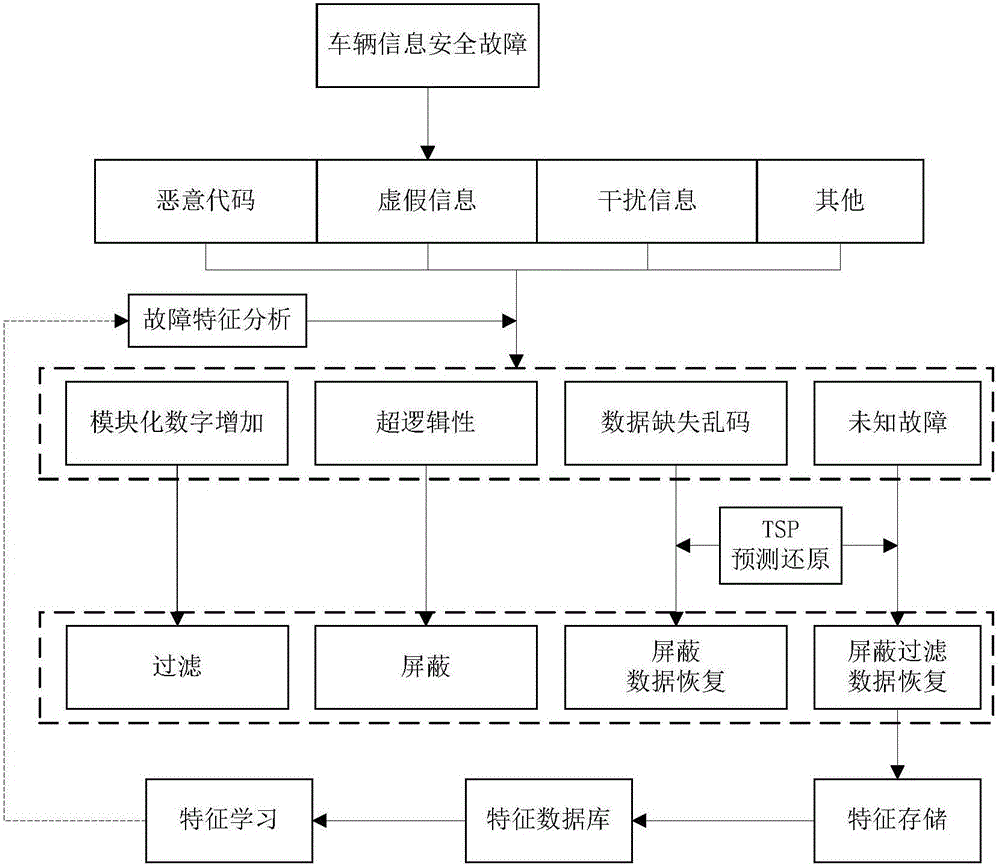
[0026] The present invention proposes a T-BOX information security detection and protection method based on vehicle abnormal data monitoring, for which a general vehicle fault tree model is established, such as figure 1 As shown, the model includes information about possible failures of traditional vehicles, smart vehicles and connected vehicles, and extracts fault features for data storage. Then, based on the abnormal vehicle data monitored by T-BOX, data fusion and big data analysis are performed in TSP, such as figure 2 As shown, according to the analysis results and the fault tree model, the real-time detection of the fault information of the vehicle is determined, and it is determined that it is caused by the function of the vehicle. It is necessary to send a reminder or warning to the user and the vehicle. For the cause of the vehicle information safety, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com