Log-based Web performance test traffic description method
A web application and log technology, applied in software testing/debugging, error detection/correction, instrumentation, etc., can solve problems such as poor versatility of UML models, inability to describe complex business types of web application traffic, construction, and difficulty in data acquisition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
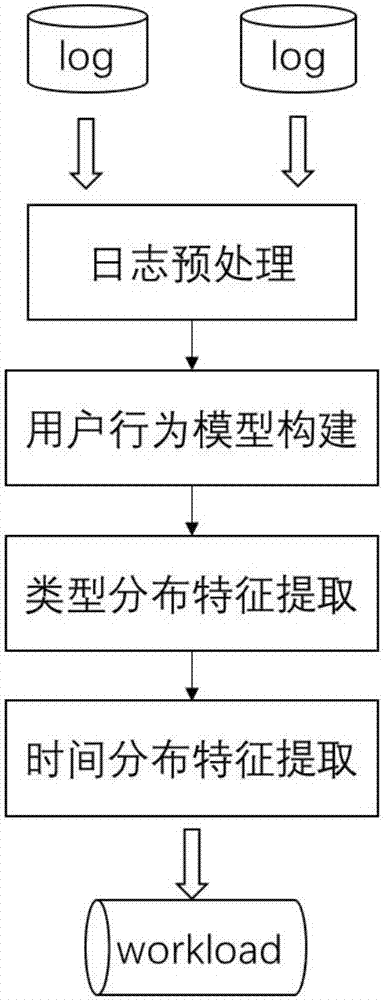
[0026] Specific implementation mode one: combine figure 1 "Implementation steps of a log-based web application performance test traffic description method" is used to illustrate that a log-based web application performance test traffic description method described in this embodiment includes the following steps: log data preprocessing steps, user behavior model Construction steps, user type distribution information extraction steps, and time distribution feature extraction steps.
specific Embodiment approach 2
[0027] Specific implementation mode two: this implementation mode is a further limitation to specific implementation mode one, and the described log data preprocessing steps are specifically:
[0028] The first step is to filter out dirty data that is useless for session extraction, including missing, error, and embedded objects contained in the page;
[0029] The second step is to structure the remaining records and match actions to generate structured records, including flags, types, and time.
specific Embodiment approach 3
[0030] Specific implementation mode three: this implementation mode is a further limitation to specific implementation mode two, and the described user behavior model construction steps are specifically:
[0031] The first step is to analyze the business logic of the web application, classify the pages, divide similar functional pages into an action according to the functional characteristics, and define the application action;
[0032] In the second step, the preprocessed formatted records are sequentially processed to identify records belonging to the same session;
[0033] The third step is to cluster the session, and extract k user behavior models from the session, the k user behavior models are k types of users, different types of users have different behavioral characteristics, and k is customized according to user needs.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com