An anonymous communication method of wmn based on network coding
A network coding and anonymous communication technology, applied in the field of WMN anonymous communication based on network coding, can solve the problems of high computational cost, low network throughput, and unfavorable large-scale promotion, so as to resist traffic analysis, improve the efficiency of the scheme, and reduce the encryption. The effect of key management overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
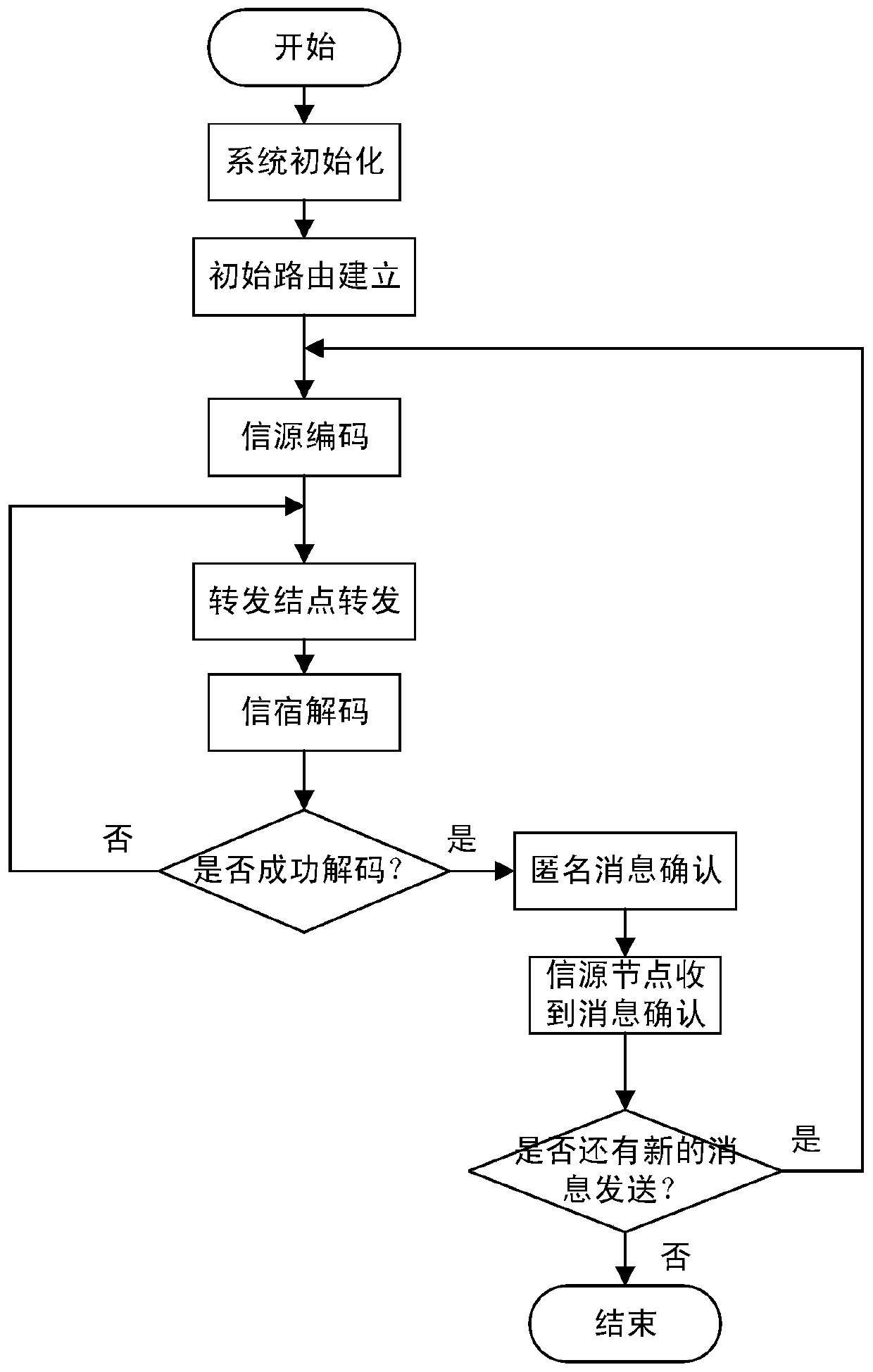
[0063] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
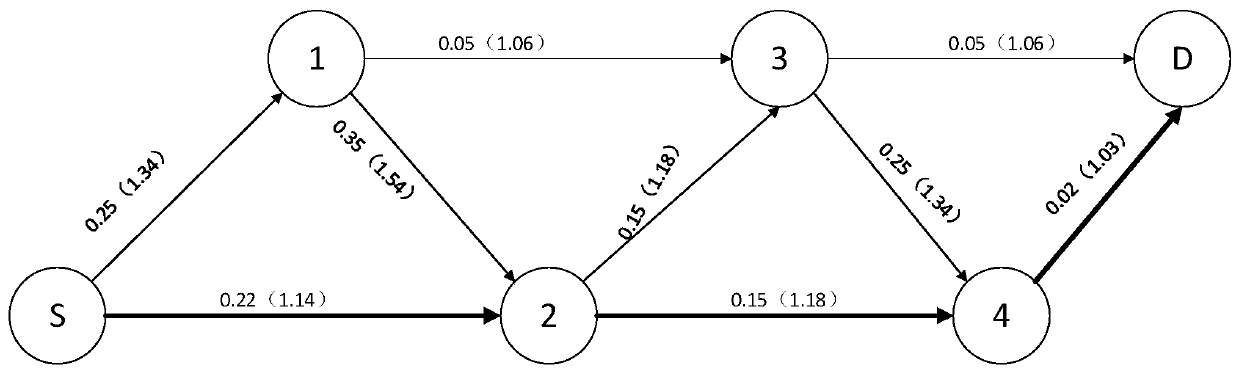
[0064] This embodiment combines the opportunistic routing protocol with network coding, and protects GEV and message content through permutation encryption. Since the permutation function and linear combination operation are interchangeable, the recoding of the forwarding node can be transparent on the encrypted data packet Execute efficiently, effectively improve the efficiency of the scheme, realize the key sharing between the communication parties in the initial routing establishment and anonymous message confirmation phase, and reduce the key management overhead.
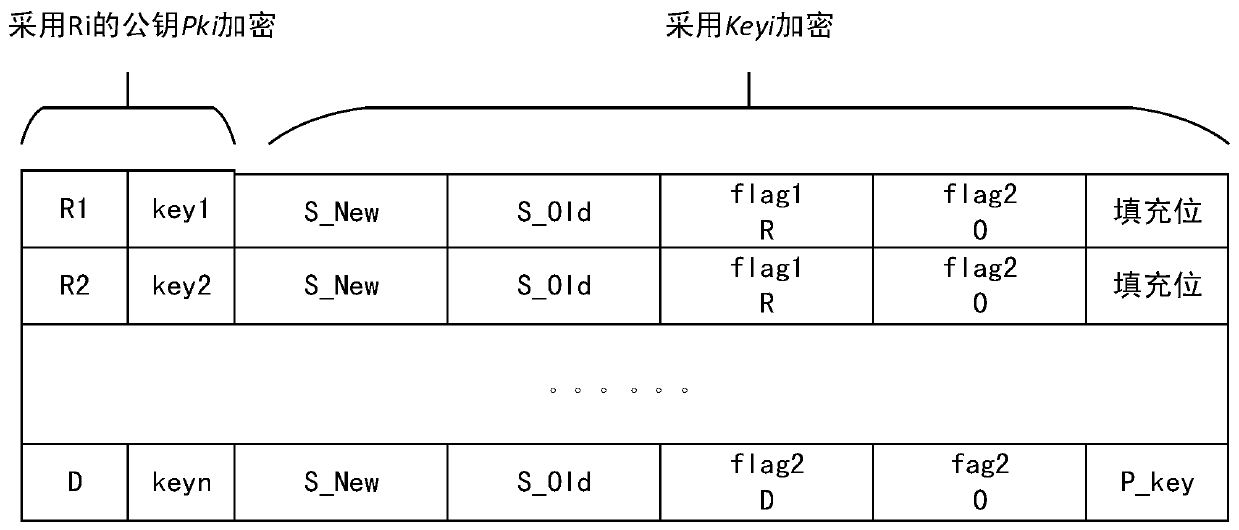
[0065] For the convenience of subsequent description, the identification and description shown in Table 1 are given.
[0066] Table 1 Identification and description
[0067]
[0068]
[0069] A WMN anonymous communication method based on network coding, whi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com