Intelligent identity information identification method based on rfid technology
A technology of identity information and RFID tags, applied in the direction of collaborative devices, instruments, biological neural network models, etc., can solve the problems of password leakage authentication system, limited length, security risks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
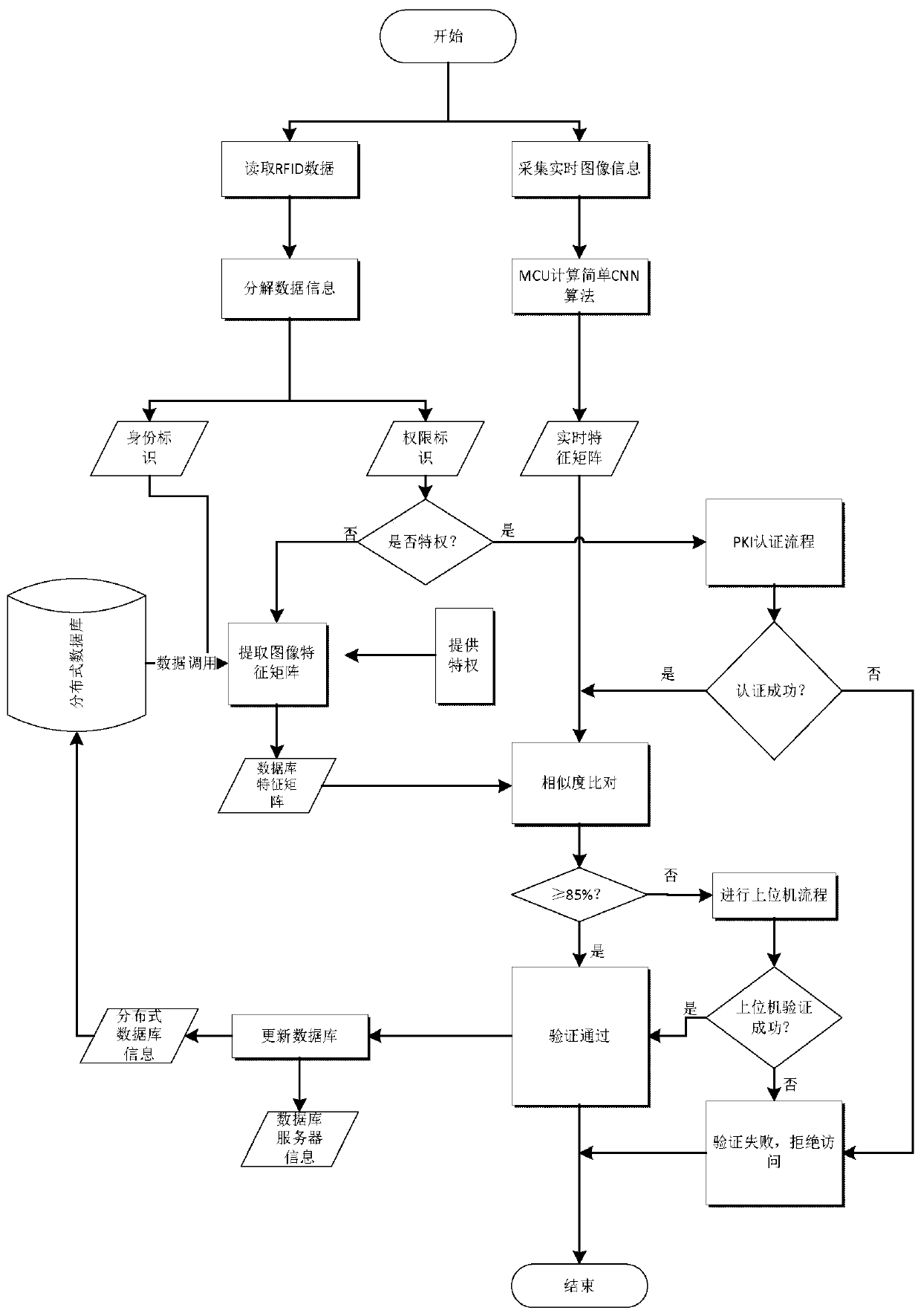
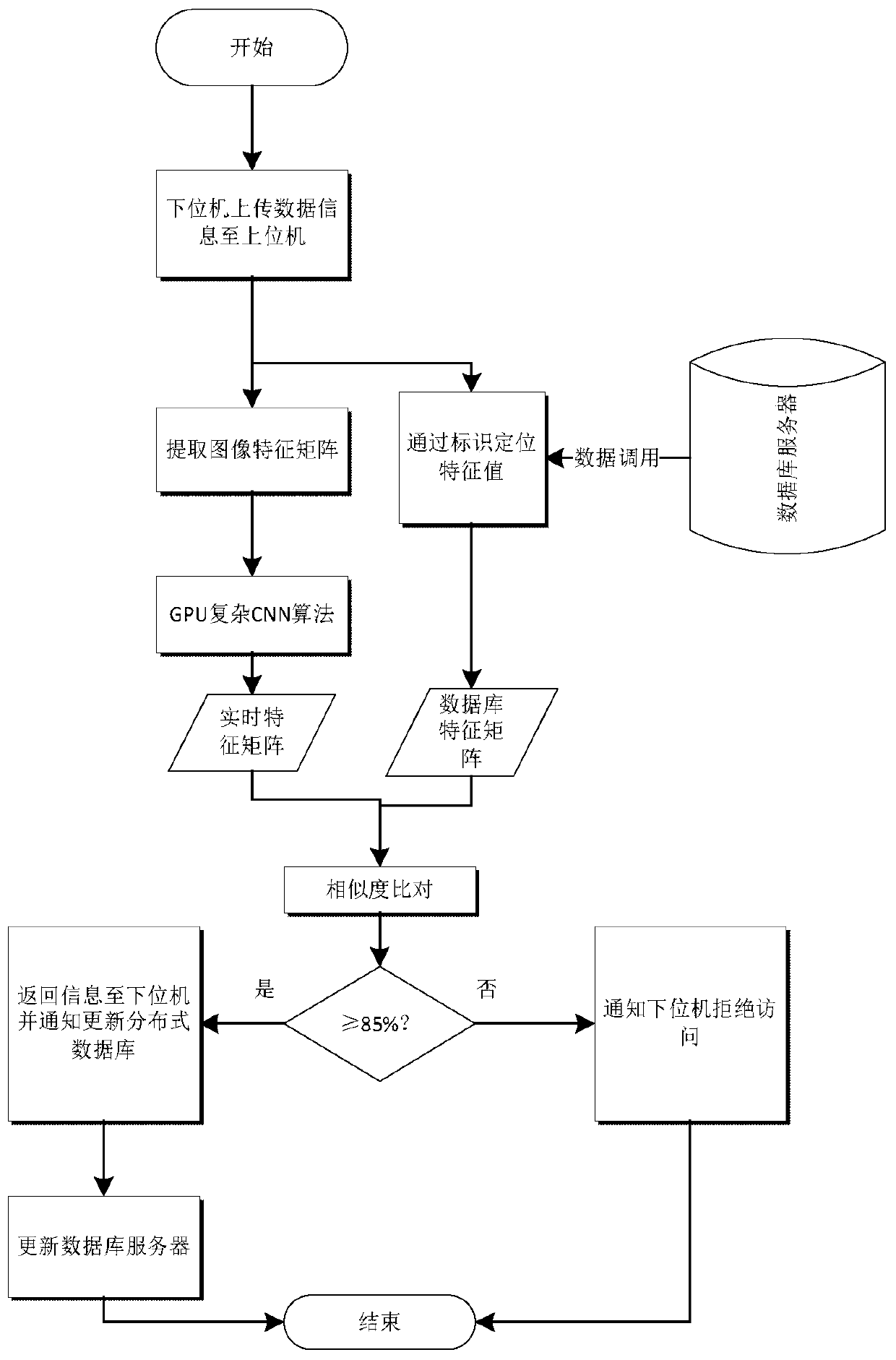
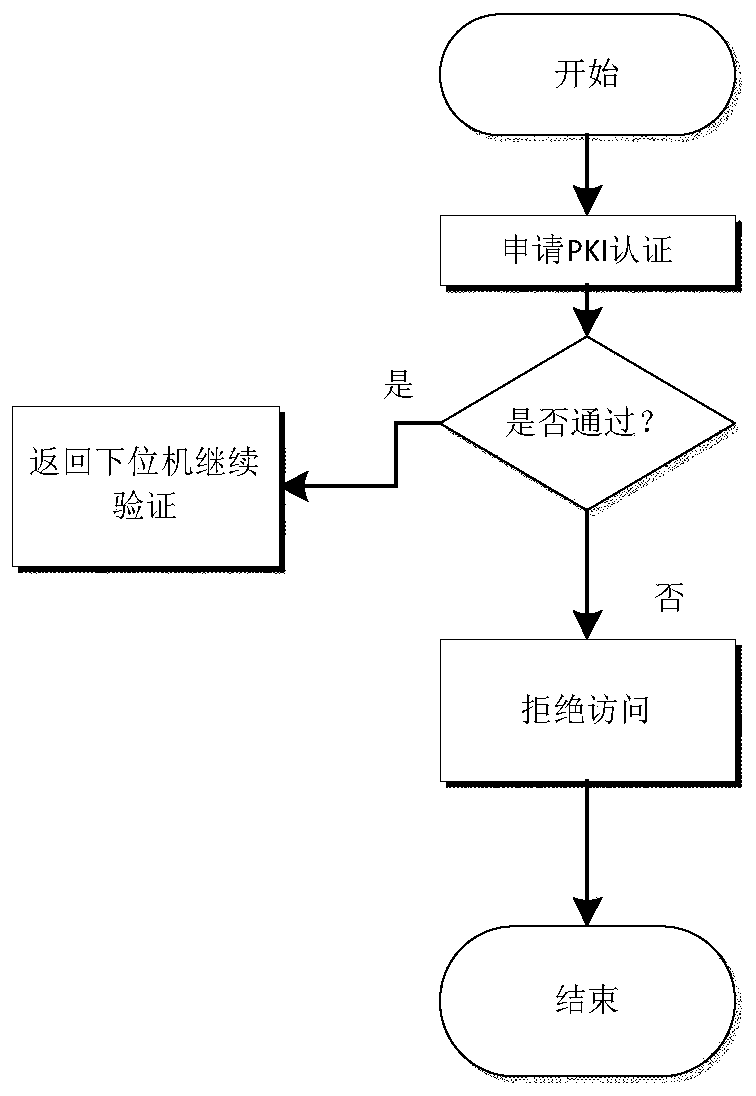
[0049] see Figure 1 to Figure 4 , a kind of intelligent identification information identification method based on RFID technology, comprises the steps:
[0050] A. Establish several subsystems, each subsystem includes RFID reader, hyper terminal, MCU module, distributed database chip and image acquisition module; and the subsystem is connected to the host system through a switch in the form of a bus; the host system includes the host and servers; servers include database servers and computing servers.
[0051] The host system is used to complete the data communication and the interactive operation of the control logic with the sub-systems of the lower layer through the switch, and perform the second convolution feature extraction level filter calculation on the user's physiological image information to obtain the complex feature vector matrix of the second image.
[0052] see Figure 5 , each subsystem includes RFID reader, hyper terminal, MCU module, image acquisition modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com