Safe access control method based on computer
A security control and computer technology, applied in computing, fire alarms, instruments, etc., can solve problems such as disturbing work order, and achieve the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0013] A computer access control security control method uses an inductive IC card, and all personnel need to enter with an authorized inductive card. The cardholder puts the card close to the card reader, and within the effective distance of the card reader, the card reader will read the data (password) in the card and transmit it to the controller at the same time, and the controller will automatically identify the identity instantly and activate the electronic door Lock. At this time, the controller and the main control computer will record the cardholder's card number, name, time of entry and exit, access control point and other information in real time, and can print reports at any time as needed. If the cardholder has no access authority, the electric lock will not act. In case of forced entry or door opening overtime, the system will automatically send an alarm signal to the main control computer for processing by security personnel. In this way, the purpose of prohib...
Embodiment 2
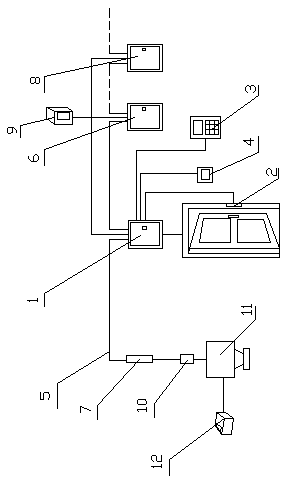
[0015] A computer access control security control method, the access control controller one (1) is respectively connected with the electric door lock 2, the door sensor, the card reader 3, and the exit pressing board 4 through lines, and the access control controller one is connected through the RS485 communication line or The TCP communication line 5 is connected with the access control controller two 6 or the communication converter 7 respectively, and the access control controller two is connected with the access control controller N8 through the RS485 communication line or the TCP communication line, and the access control controller one is connected with the access control controller N8 through the RS485 communication line or the TCP communication line. , the access controller 2 and the access controller N are connected to the UPS power supply 9 .
Embodiment 3
[0017] According to the computer access control security control system and method described in embodiment 1, the communication converter is connected to the network interface 10, the network interface is connected to the access control management machine 11, and the access control management machine is connected to the printer 12 connect.
[0018] The said access controller can control one, two or four said electric door locks.
[0019] Each person will hold a proximity card the size of a credit card. According to the authorization obtained, the designated door lock can be opened within the validity period to enter the public passage or door that implements access control. The data collected on the card reader will form attendance Management, for each defense zone, realize the alarm function by installing various detectors, sensors and various alarm devices. The central management computer records all system events, and configures relevant management software to perform reco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com