Lightweight hashed password digest generation method
A lightweight, hash technology, applied in the field of lightweight hash password digest generation, which can solve problems such as increasing running time and power consumption, and conforming to algorithm parameters.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention will be described in detail below through specific implementation examples.
[0052] The processing method of this implementation example is as follows:
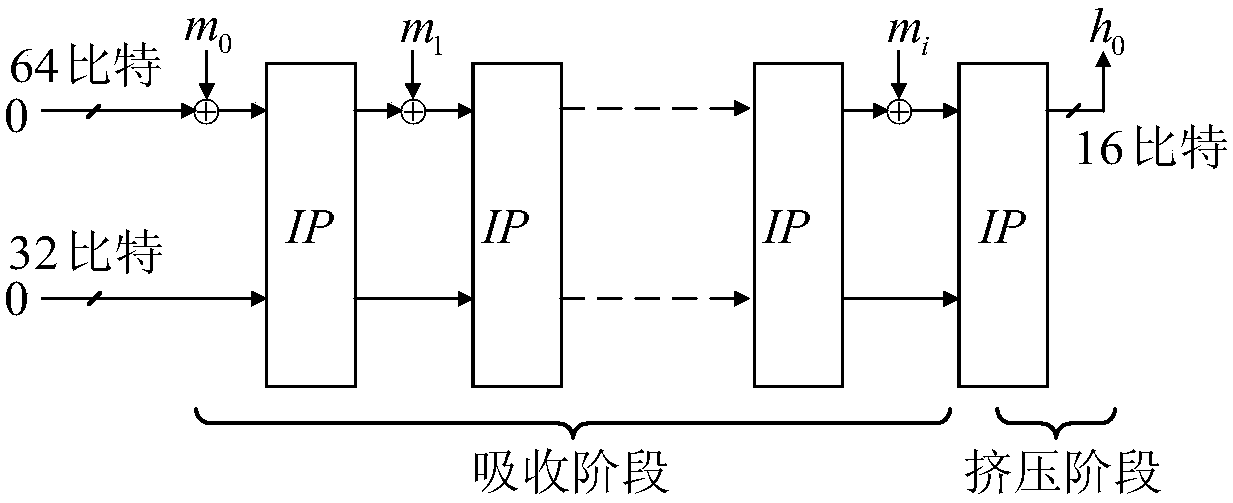
[0053] Step 1: Divide the input message M into 64-bit message blocks m 0 ,m 1 ,...,m i . Set the initial state S 0 A 96-bit string of all zeros.
[0054] Step 2: Block the message m j XOR to S j On the high-order 64 bits, the state after XOR is used as the input S of the internal permutation IP j ', where 0≤j≤i.
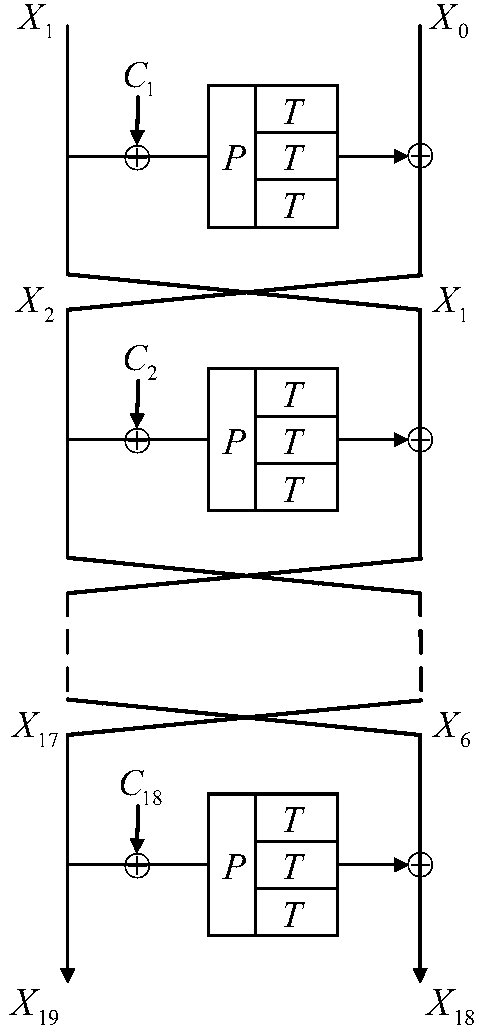
[0055] Step 3: Enter 96 bits into state S j 'Equally divided into two parts, which are respectively recorded as the left half branch L and the right half branch R, wherein both L and R are 48-bit strings.
[0056] Step 4: Combine the upper 16 bits of the left half branch L with the round constant C r (1≤r≤18) XOR, the output after XOR is used as the input of position replacement P.
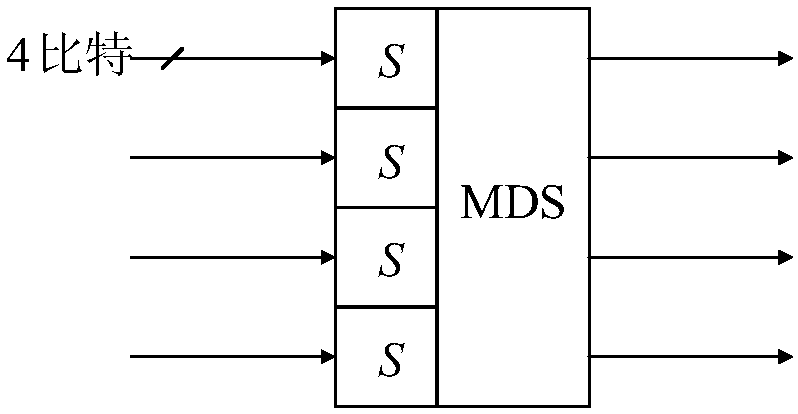
[0057] Step 5: Divide the 48-bit input of position replacement P into 12 groups according to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com