Data access control method and device
A data access control and data access technology, applied in the field of data security, can solve the problems of unauthorized receipt malicious access, malicious tampering of network information, malicious access to data, etc., to avoid malicious access, improve user experience, and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
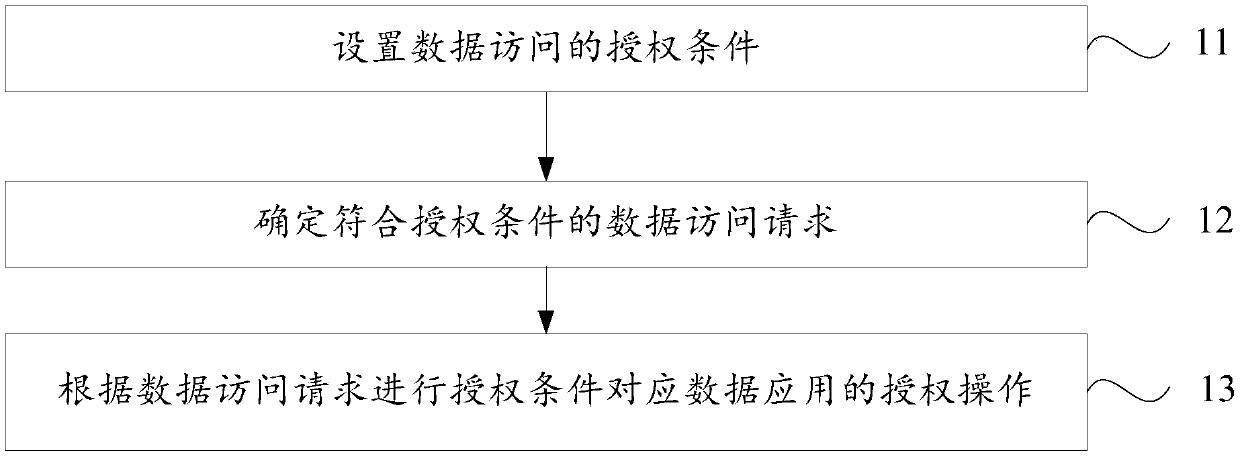
[0041] figure 1 It is a flowchart of the data access control method provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the embodiment of the present invention provides a data access control method, the method includes the following steps:
[0042] 11. Set the authorization conditions for data access, where the authorization conditions include one or more authorization conditions that can meet the different access requirements of users accessing data, and the data accessed by users is stored in the blockchain network.
[0043] Specifically, the authorization conditions for setting data access include the following items:
[0044] Determine the legal account information verification rules for authorized users; and / or determine the authorization rules for different authorization levels according to different authorized users; and / or determine the authorization rules for different authorization fees for different authorized users; and / or determine the ...
Embodiment 2
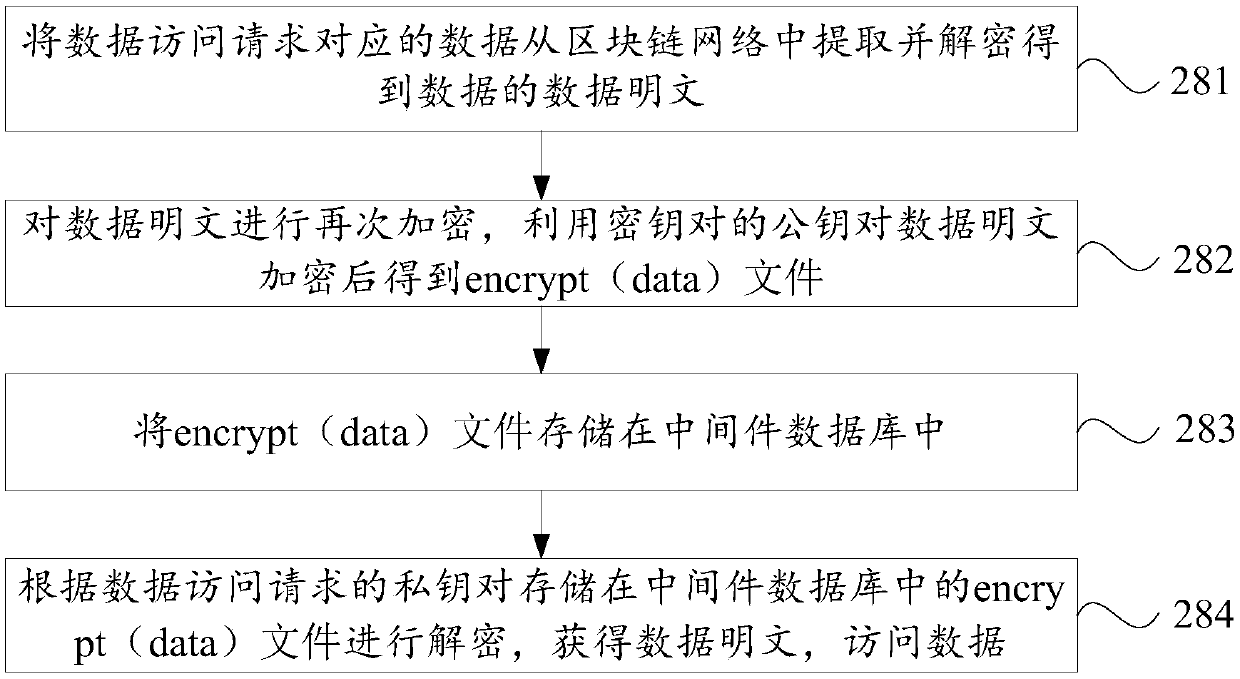
[0068] figure 2 It is a flow chart of the data access control method provided by Embodiment 2 of the present invention.
[0069] Such as figure 2 As shown, the data access control method provided by the embodiment of the present invention includes the following steps:
[0070] 21. Determine the legal account information verification rules for authorized users.
[0071] According to the key verification and / or account address of asymmetric encryption, the legal verification of the authorized user is carried out.
[0072] Specifically, the asymmetric encryption technology adopted uses the private key to calculate the public key. The public-private key login authorization method can outsource a layer of account password system, or directly use the public-private key, and then log in through the public-private key method or add the account address. Legal verification of authorized users prior to operations such as access, application, authorization, encryption, and decryption...
Embodiment 3
[0100] Such as Figure 4 As shown, the data access authority control device provided by the embodiment of the present invention includes a setting module 31 , a determination module 32 and an authorization operation module 33 .
[0101] Specifically, the setting module 31 is configured to set authorization conditions for data access. Further, the setting module 31 includes: a first determination module 311, used to determine the legal account information verification rules for authorized users; a second determination module 312, used to determine authorization rules for different authorization levels according to different authorized users; The determination module 313 is used to determine the authorization rules for different authorization fees according to different authorized users; the fourth determination module 314 is used to determine the authorization rules for different authorization times according to different authorized users; the fifth determination module 315 is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com