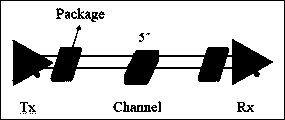Signal integrity simulation method for mixed encryption model
A technology of signal integrity and simulation methods, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve problems such as inability to complete link simulation and distortion of simulation results, and achieve outstanding substantive features, reliable principles, and The effect of broad application prospects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] A method for simulating signal integrity of an encrypted mixed model provided in this embodiment includes:
[0037] Using transient simulation to extract the step response of the SPICE model;
[0038] Generate an external random code signal;
[0039] Import the extracted step response data as the input source of ADS channel simulation;
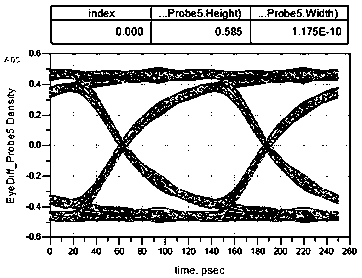
[0040] The ADS channel emulator calculates the eye diagram of the RX end according to the algorithm and the external random code signal, and completes the eye diagram measurement.
[0041] In this embodiment, the verification link needs to be carried out before the transient simulation, and the verification link is that the TX end is connected to the RX end through a wiring model; the TX end chip is an encrypted SPICE model, and the step response generated by the TX end chip is completely Contains the characteristics of the TX-side chip; the RX-side chip is an IBIS AMI model; the TX-side SPICE model is an RC circuit.
[0042] In this...
Embodiment 2
[0050] This embodiment provides a signal integrity simulation method of an encrypted mixed model. In this embodiment, the SPICE model at the TX end is an encrypted model, and the steps of the simulation method include:
[0051] 1) Transient simulation based on HSPICE, the encrypted SPICE model and link construction are used for transient step response simulation, and the step response output file with the suffix .lis is obtained; edit the format of the file so that it can be called by ADS The suffix is .tim file;
[0052] 2) Carry out active simulation, import the step response data (.tim) into ADS for active simulation, call the step response data in ADS, and complete the active simulation with an external random code signal source; reserve the input interface of the model , it is convenient to input a step signal outside the model; import it into the channel simulation as the signal source of the RX terminal, add a random code signal, and set related parameters;
[0053] ...
Embodiment 3
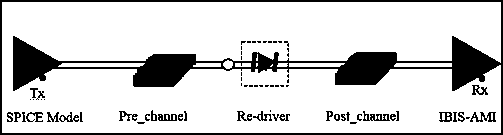
[0055] The simulation link in this embodiment is as follows figure 1As shown, the TX end chip is an encrypted SPICE model, the relay system chip and the RX end chip are IBIS AMI models, and the Pre_channel and Post_channel in the link are both 5inch long PCB trace models; the TX end is Broadcom's PEX9797 chip , the Re-driver is TI's DS80PCI800 chip, and the RX end is the CPU model provided by Intel.
[0056] Since the SPICE model and the IBIS AMI model cannot exist in the simulation link at the same time, first figure 2 The verification link shown is for simulation verification, in which the TX and RX end chips are SPICE models and IBIS AMI models respectively, and the TX end SPICE model is an RC circuit, and the link only includes 5-inch length PCB traces.
[0057] In this embodiment, the SPICE model at the TX end is assumed to be an unencrypted model, and the simulation steps are as follows:
[0058] 1) SPICE model import. Import the SPICE model based on the Spice Wizard...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com