Hardware Trojan horse detection method and a device of a key node based on power consumption average analysis
A hardware Trojan detection and key node technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of high engineering cost, low detection accuracy, and narrow application range, and achieve low engineering cost, high detection accuracy, and wide application range. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0029] In the following, the AES (Advanced Encryption Standard) encryption chip will be used as an example to further describe in detail the method and device for detecting hardware Trojan horses at key nodes based on average power consumption analysis of the present invention.
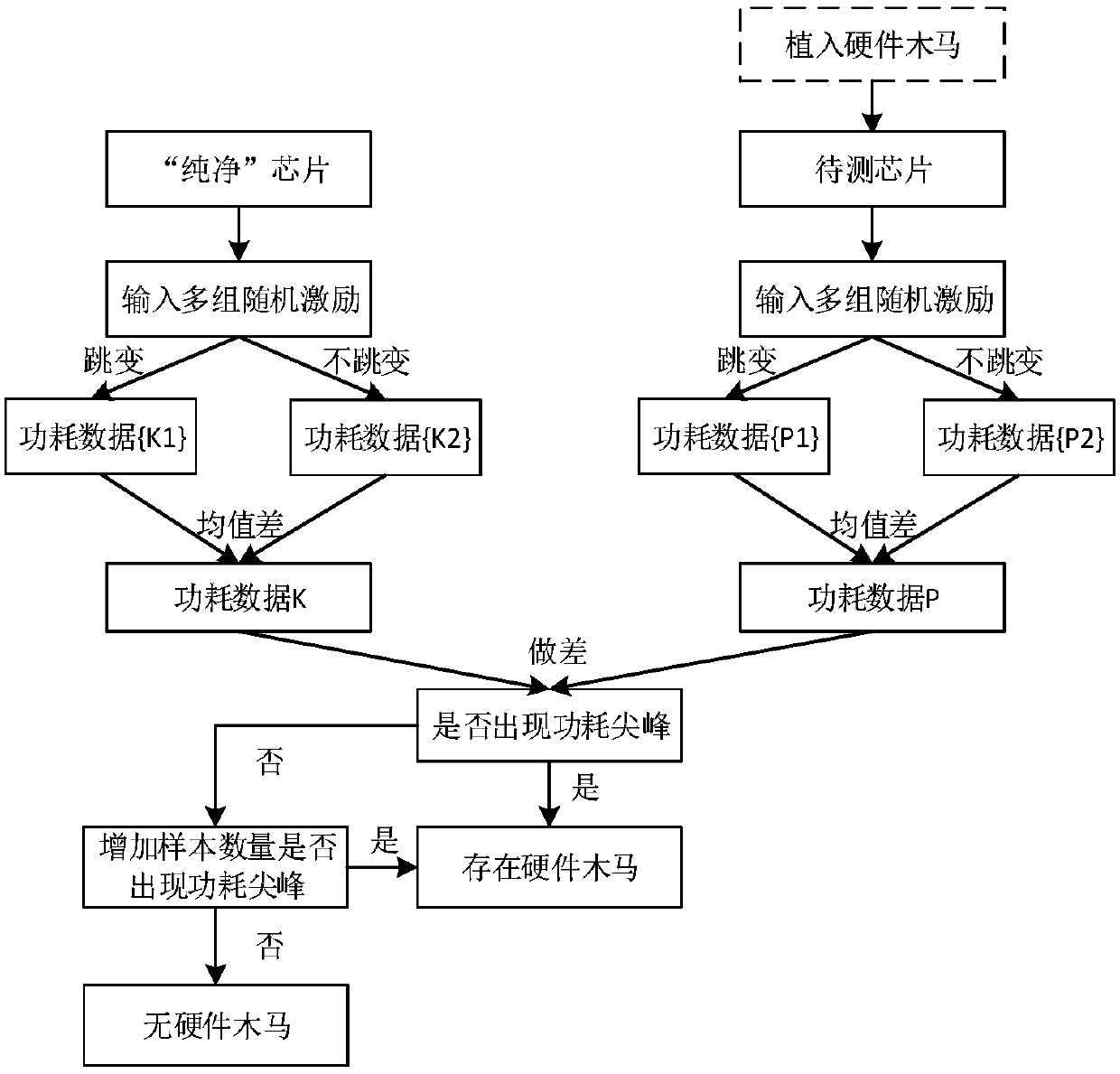
[0030] Such as figure 1 As shown, the implementation steps of the key node hardware Trojan horse detection method based on power consumption average analysis in this embodiment include:
[0031] 1) For the chip to be tested, select a pure reference chip ("pure" chip) that is confirmed to be free of hardware Trojans;
[0032] 2) Key nodes selected for the chip to be tested;
[0033] 3) Apply incentives to the pure reference chip and sample the power consumption data of the pure reference chip to obtain the power consumption data K of the corresponding key node when the logic value jumps 1 , The power consumption data K when the logic value does not jump 2 , the power consumption data K 1 , power co...
Embodiment 2
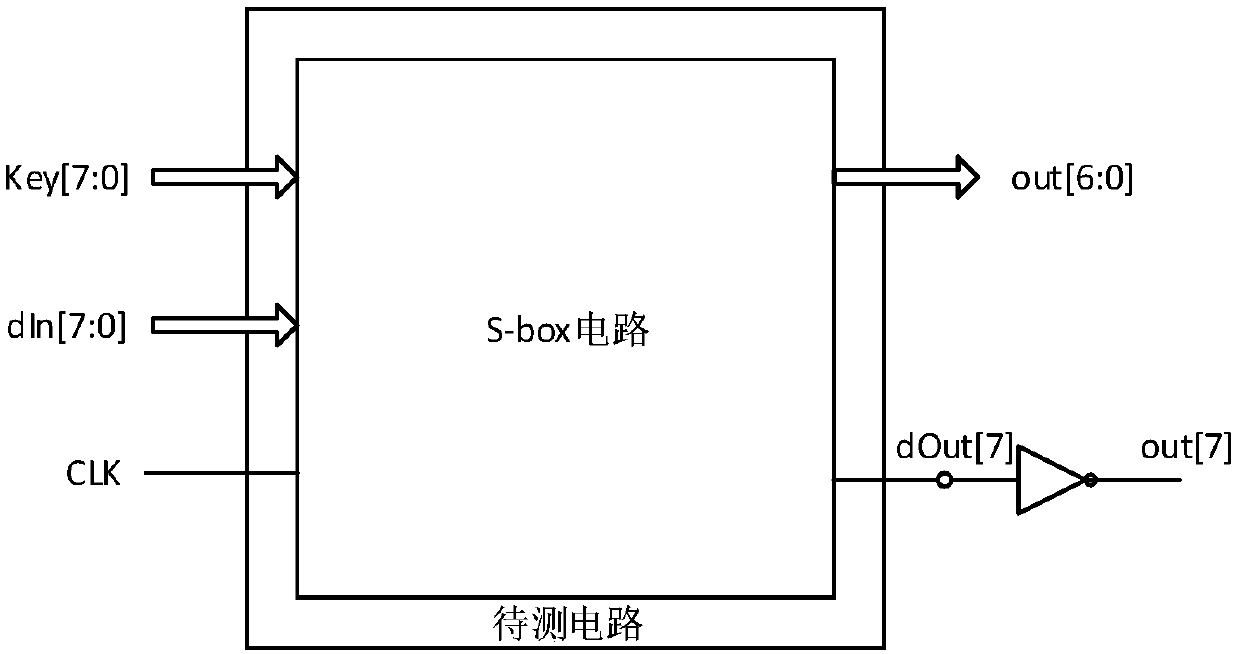
[0059] This embodiment is basically the same as Embodiment 1, and the main difference is: this embodiment performs batch detection for batches of chips to be tested. In order to simulate other batches of 9 chips to be tested, the AES encryption chip is introduced into the process deviation using the Monte Carlo random method, and the 9 chips to be tested from other batches are simulated. Such as image 3 As shown, the s-box module in the AES encryption circuit of the specific implementation step 2) selects the highest bit (out[7]) of one of the 8-bit output ports as a key node, and the remaining 7 bits (out[6:0]) as a reference node. Utilize the Virtuoso tool to attach a hardware Trojan horse (1 inverter) to the key node of the encrypted circuit layout.
[0060] Such as Figure 4 As shown, when obtaining the power consumption data K in this embodiment: use the Caliber tool to perform capacitance (C) and resistance (R) parasitic parameter extraction (RC extraction) on the "p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com