A distributed vehicle electronic system information security protection method
A vehicle-mounted electronics and system information technology, applied in the field of vehicle-mounted system information security, can solve difficult vehicle-mounted system applications and deployments, inability to apply vehicle-mounted systems, and inability to simultaneously adapt to low-resource overhead, high-security and high-real-time requirements of vehicle-mounted networks, etc. problems, to achieve the effect of comprehensive security protection capabilities and confidentiality protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
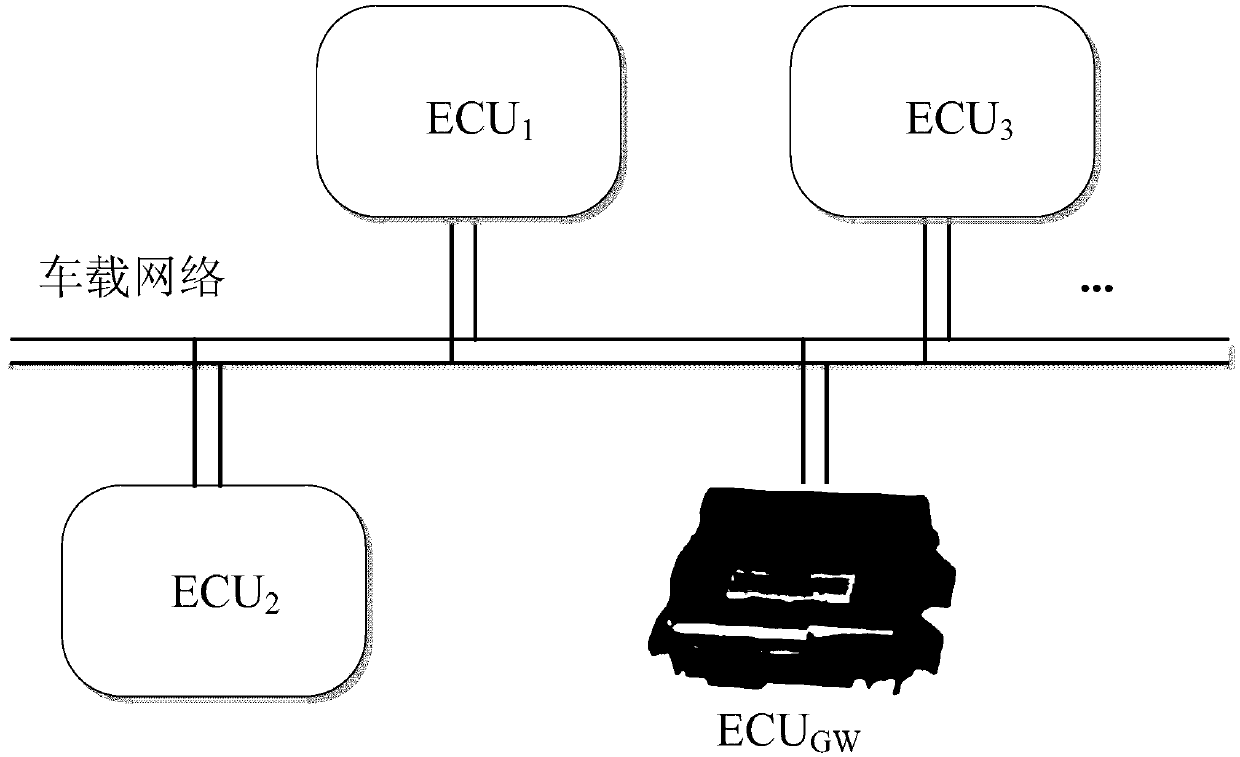
[0037] Include the following steps:
[0038] The first stage: system initialization, in this stage, the electronic control unit inside the system loads the long-term key through the secure channel;
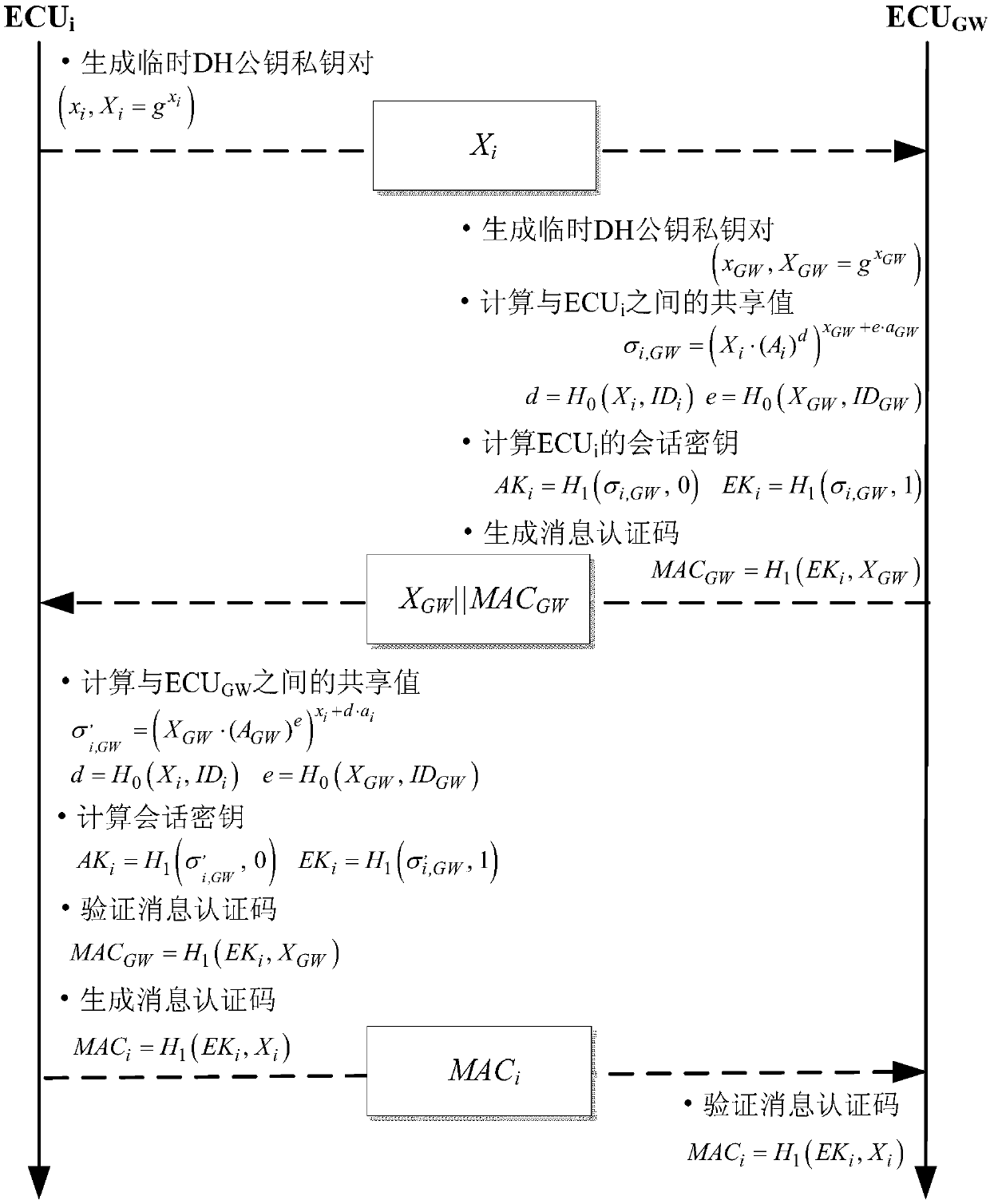
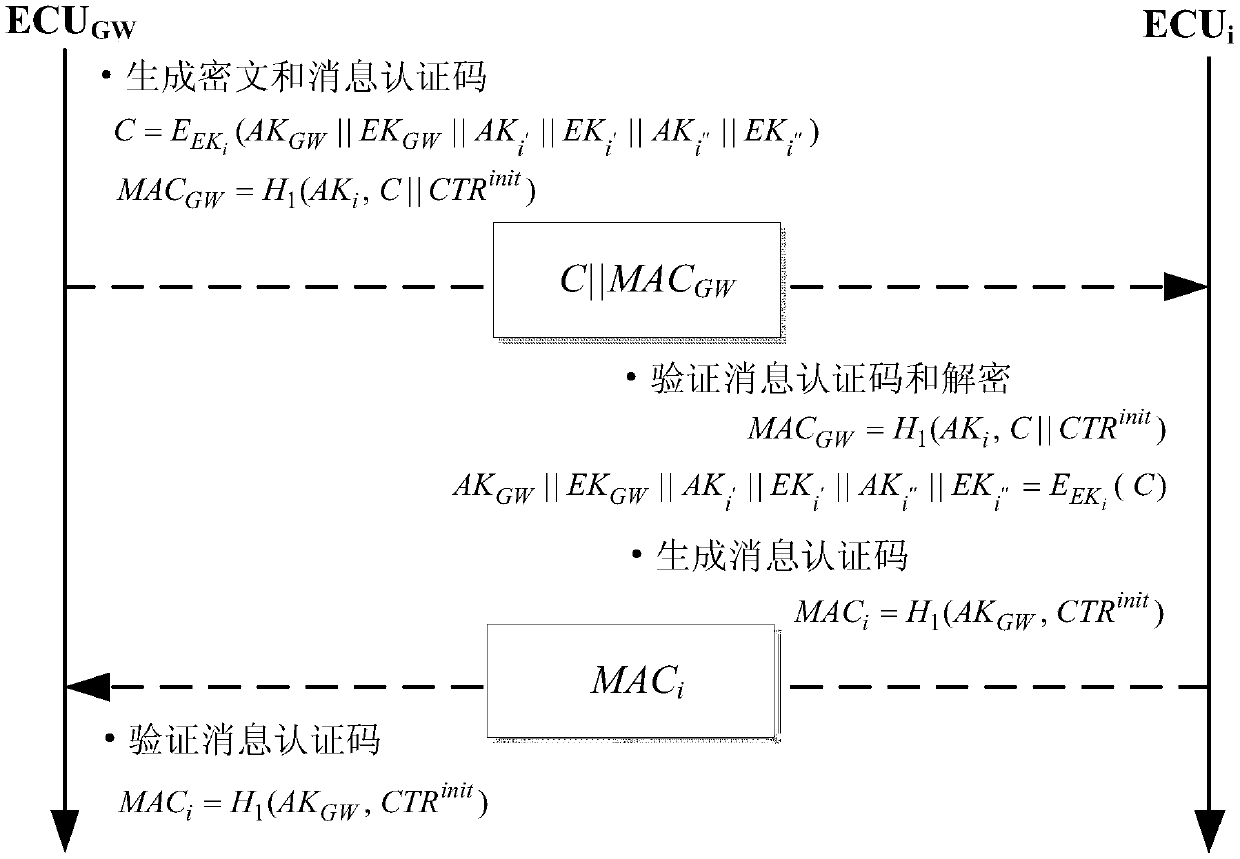
[0039] The second stage: session key generation and distribution. In this stage, the gateway electronic control unit deduces and distributes the session key with each other electronic control unit in a fixed order;
[0040] The third stage: data frame encryption and authentication. In this stage, the electronic control unit performs encryption, decryption and authentication of data frames.
[0041] The method of system initialization in the first stage of the present invention is as follows, gateway electronic control unit ECU GW The preset long-term Diffie-Hellman (DH) public-private key pair (A GW ,a GW ) and all other electronic control units ECU i DH public key A i loaded into a secure storage area while the ECU i The preset long-term DH public-private key pair (A i ,a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com