Android application security monitoring method based on plug-in loading and storage medium
An application security and plug-in technology, applied in the field of information security, can solve the problems of difficult to find detection capabilities, poor cooperation in system iterative development, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
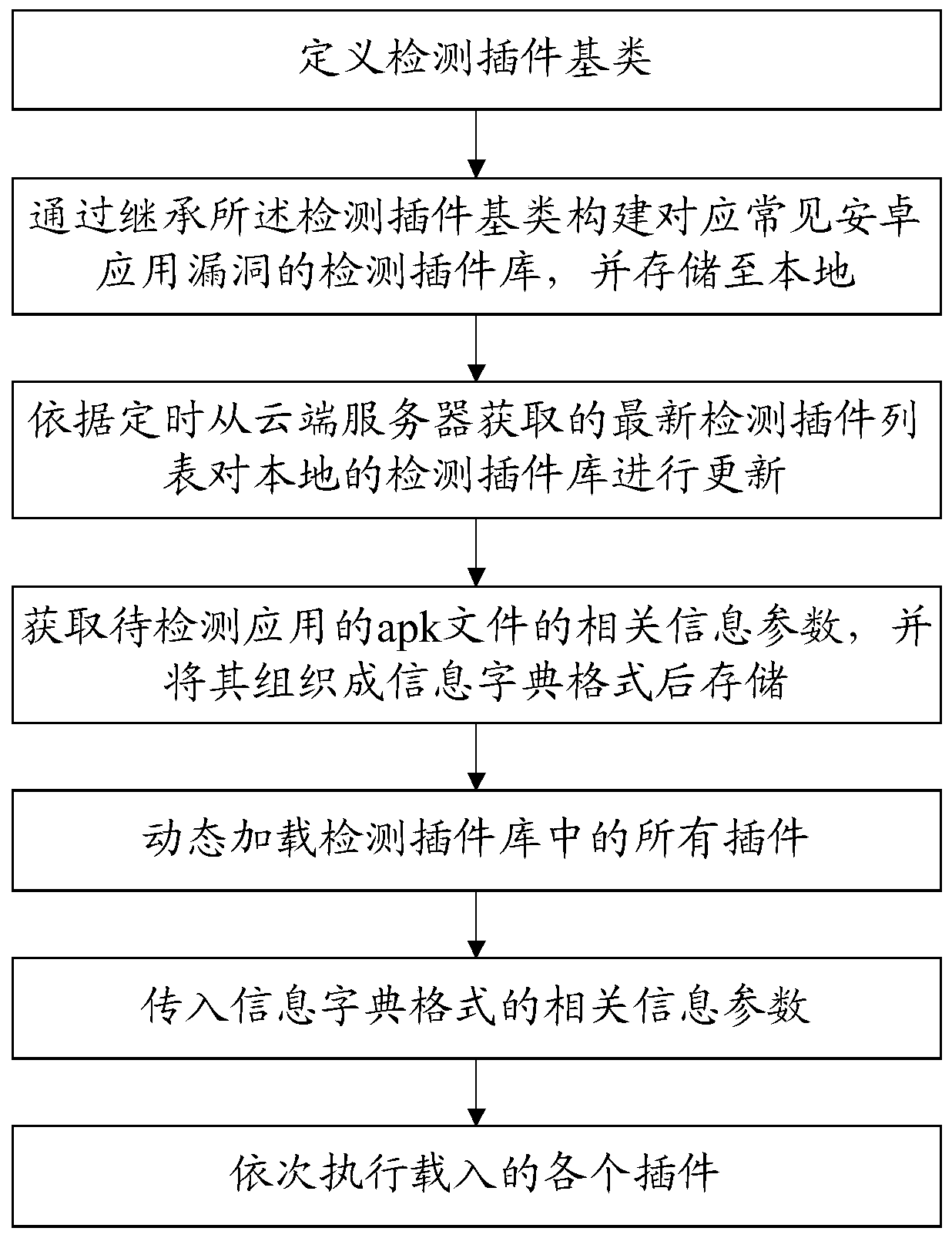
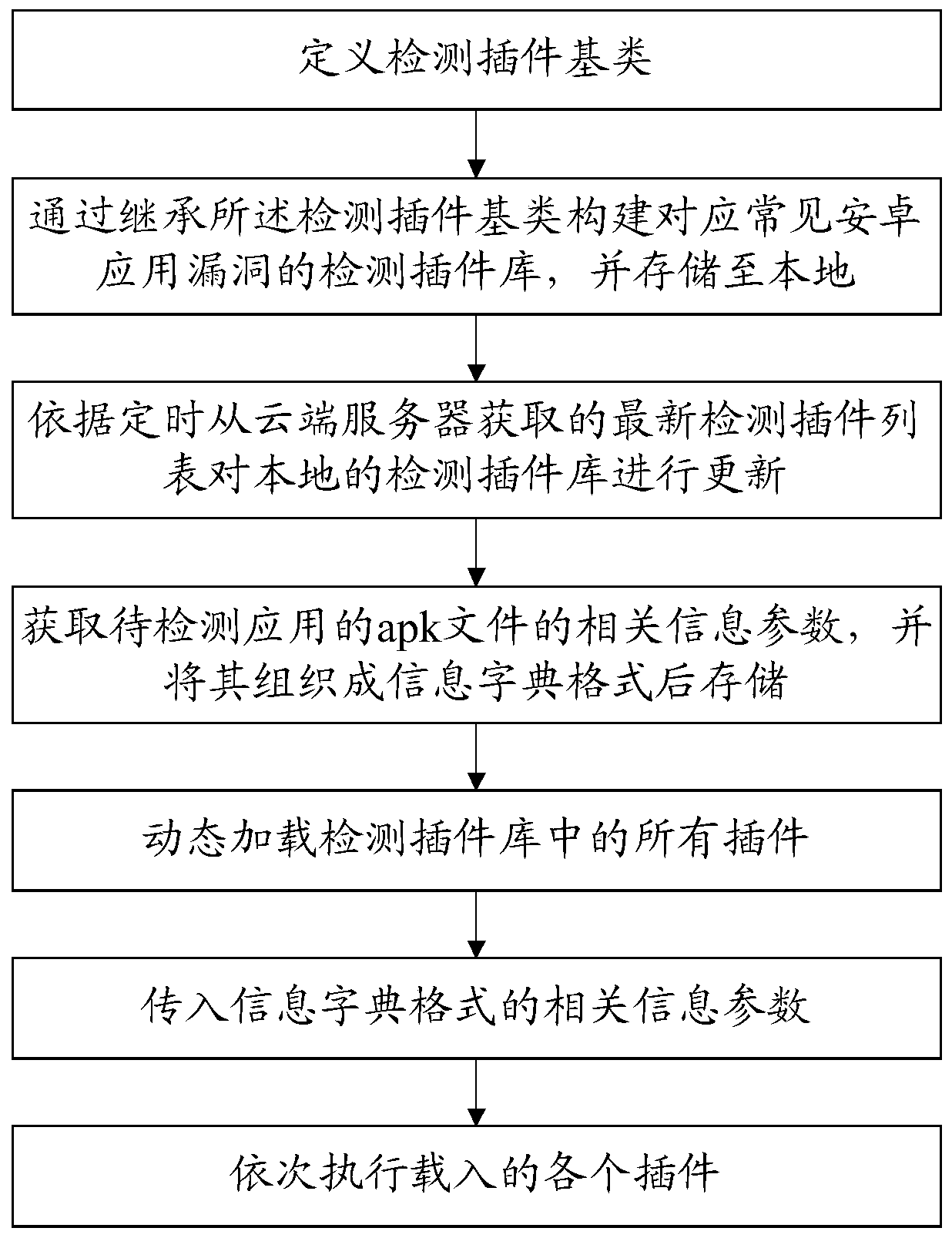
[0082] Please refer to figure 1 , this embodiment provides a plug-in-based Android application security monitoring method, which is suitable for comprehensive and effective security vulnerability detection of Android APP, and the detection method has low coupling, high availability and scalability.
[0083] The method of the present embodiment comprises the following steps:
[0084] (1) Detection plug-in preparation process
[0085] S1: Define the detection plug-in base class;
[0086] Define and agree on a vulnerability detection plug-in base class, which defines member variable attributes including plug-in name, associated vulnerability number, plug-in version, detection result, plug-in priority, number of discoveries, and detection status. Using the characteristics of class inheritance in object-oriented programming (inheritance is one of the most important concepts in object-oriented programming, inheritance allows the use of existing classes in the hierarchical structur...
Embodiment 2
[0126] This embodiment corresponds to Embodiment 1, and provides a computer-readable storage medium on which a computer program is stored. When the program is executed by a processor, the Android application security monitoring based on plug-in loading described in Embodiment 1 can be realized. The steps included in the method. The specific steps will not be repeated here, please refer to the description of Embodiment 1 for details.
[0127] Wherein, the storage medium may be a magnetic disk, an optical disk, a read-only memory (Read-Only Memory, ROM) or a random access memory (Random Access Memory, RAM) and the like.
Embodiment 3
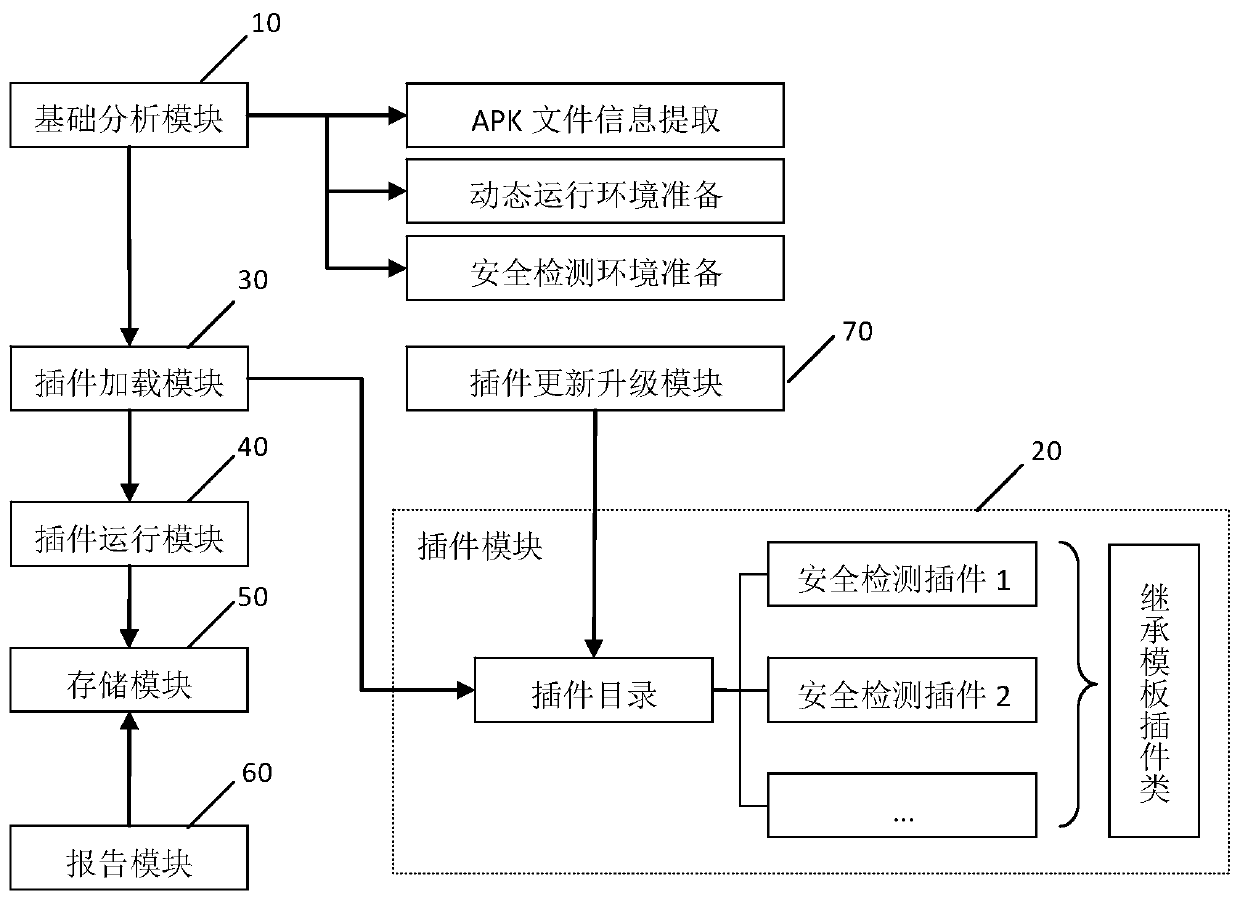
[0129] This embodiment corresponds to Embodiment 1, and provides an Android application security monitoring system based on plug-in loading, and implements the method described in Embodiment 1 through specific functional modules.
[0130] Specifically, the system of this embodiment includes a basic analysis module 10, a plug-in module 20, a plug-in loading module 30, a plug-in running module 40, a storage module 50, a reporting module 60 and an insertion update and upgrade module 70. For the connection relationship of each module, please refer to figure 2 .
[0131] Wherein, the basic analysis module 10 is used to pre-prepare the apk_info_dict parameter before running the plug-in. For the specific execution process, refer to the content of S4 in the first embodiment.
[0132] Wherein, the plug-in module 10 is composed of a template plug-in, a plug-in directory, and all security detection plug-ins under the plug-in directory. Among them, the template plug-in is the base class...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com