Safe distributed database interaction method suitable for mobile positioning system
A technology of mobile positioning and interaction method, applied in the field of computer network communication and distributed database, which can solve the problems of low efficiency, inability to realize one-time pad, no identity authentication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The present invention will be further described in detail below in conjunction with the drawings and specific embodiments:
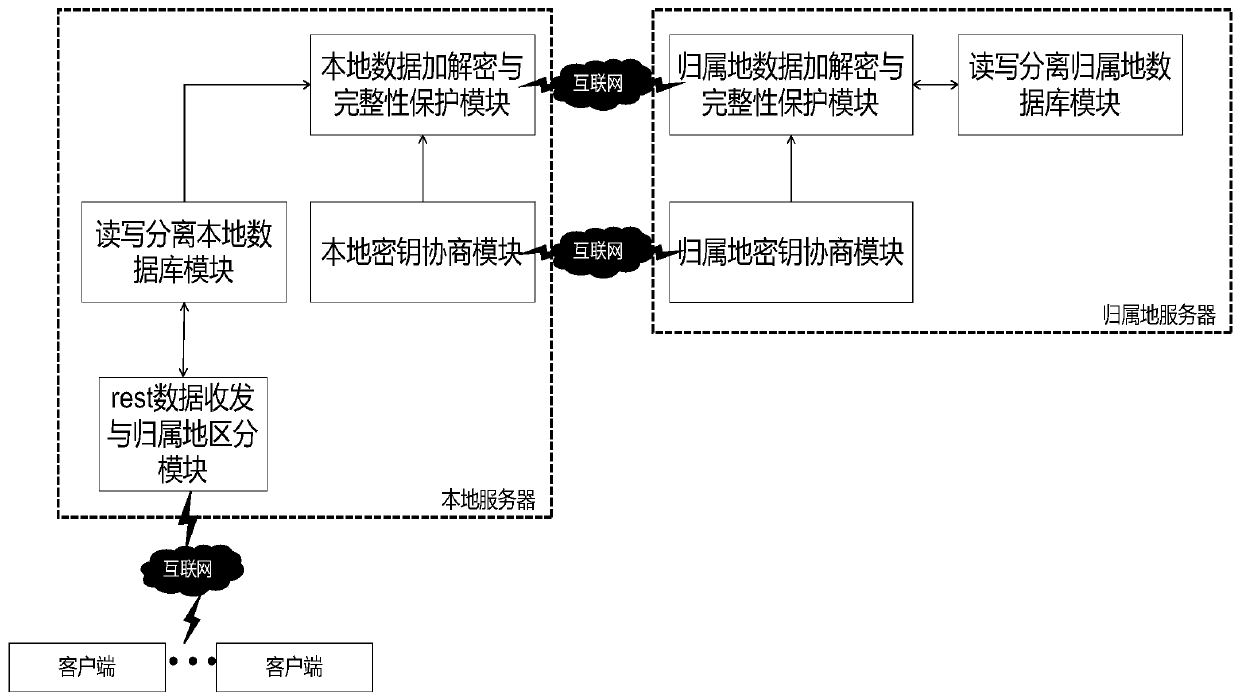
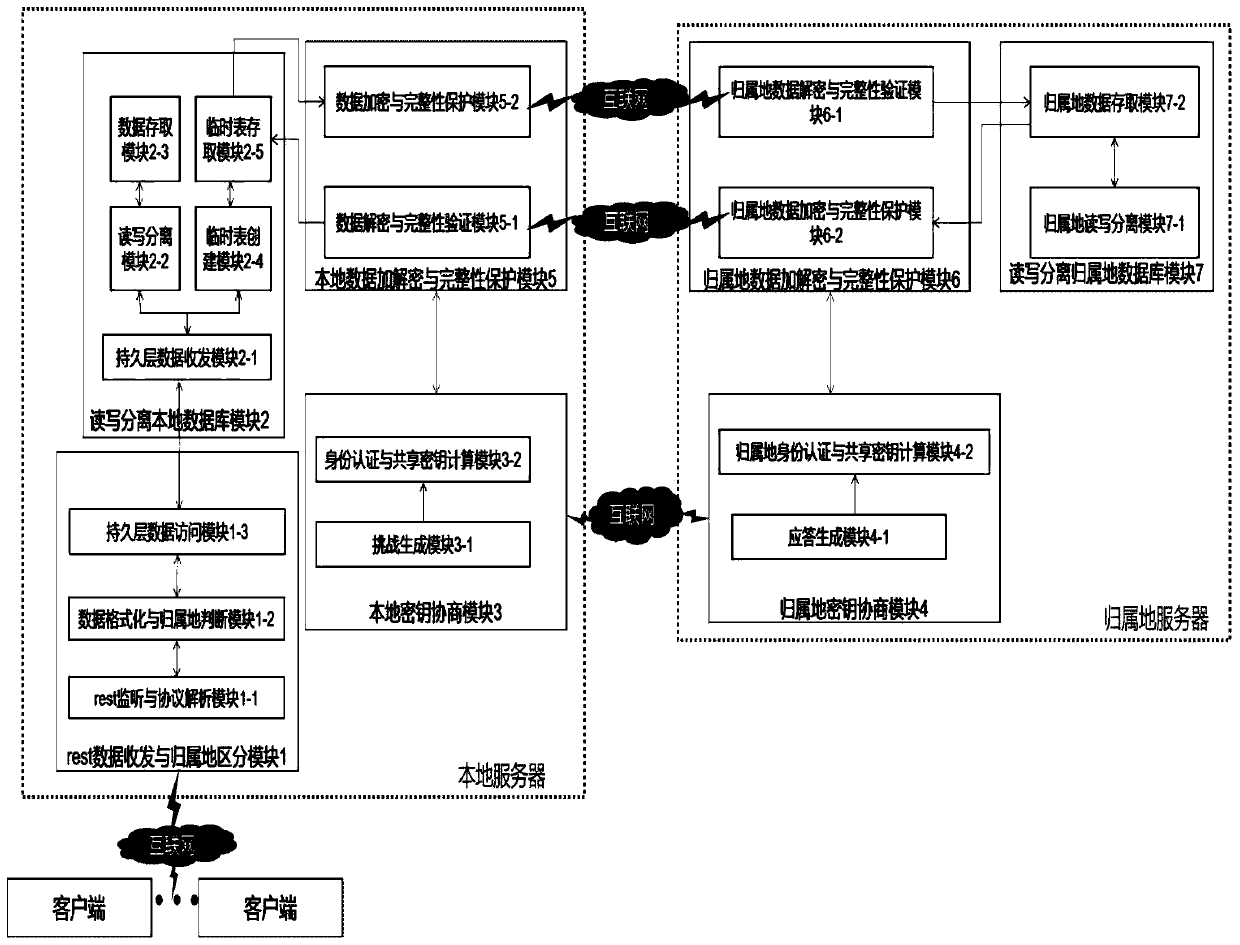
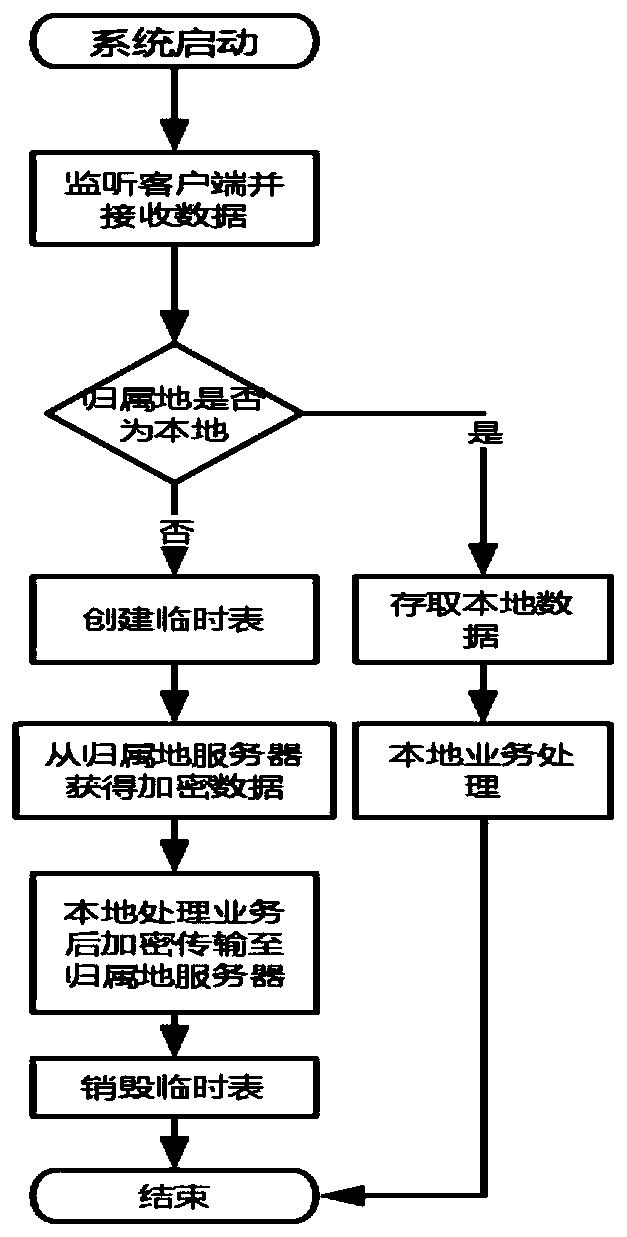
[0063] The present invention provides a secure distributed database interaction method suitable for mobile positioning systems. The present invention improves the SM4 encryption algorithm by designing, adopts a pre-shared key to independently design a key agreement protocol, designs a statistically based read-write separation algorithm and has The data integrity protection model provides a safe distributed database interaction method suitable for mobile positioning systems. This method can be applied to the distributed database of the mobile positioning system. The distributed database is separated from reading and writing, and the interaction between the databases is separated. Encrypt data, provide a one-time encryption standard for encryption, and localize non-local users with a temporary table designed for business, which ensures the efficient rea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com