Safety protection system and method based on challenge response and storage medium
A technology of security protection and response code, applied in the field of security protection system based on challenge response, can solve problems such as loss, threat to network security, and routers being easily hacked, and achieve high network stability and security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
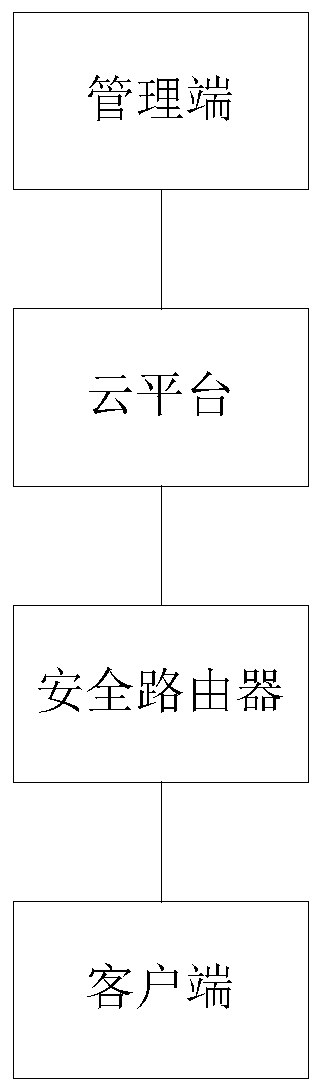
[0055] Embodiment 1: as figure 1 As shown, a security protection system based on a challenge response includes a client, a router, and a cloud platform connected in sequence, and the client is used to send an application KEY, an application challenge response code, and initiate a challenge response to the router, and display the response result. The router is used to select and / or set routes, process network requests and / or responses, and process data; the cloud platform is connected to routers, used to receive network requests and / or send response results, and The data is processed.
[0056] Among them, first of all, the cloud platform has the advantages of large scale, virtualization, high reliability and good scalability, and has good flexibility, adaptability and scalability. Secondly, the cloud platform is based on the high-efficiency computing mode of cloud computing. , can provide a good application foundation for network communication.
[0057] Wherein, the client ca...
Embodiment 2
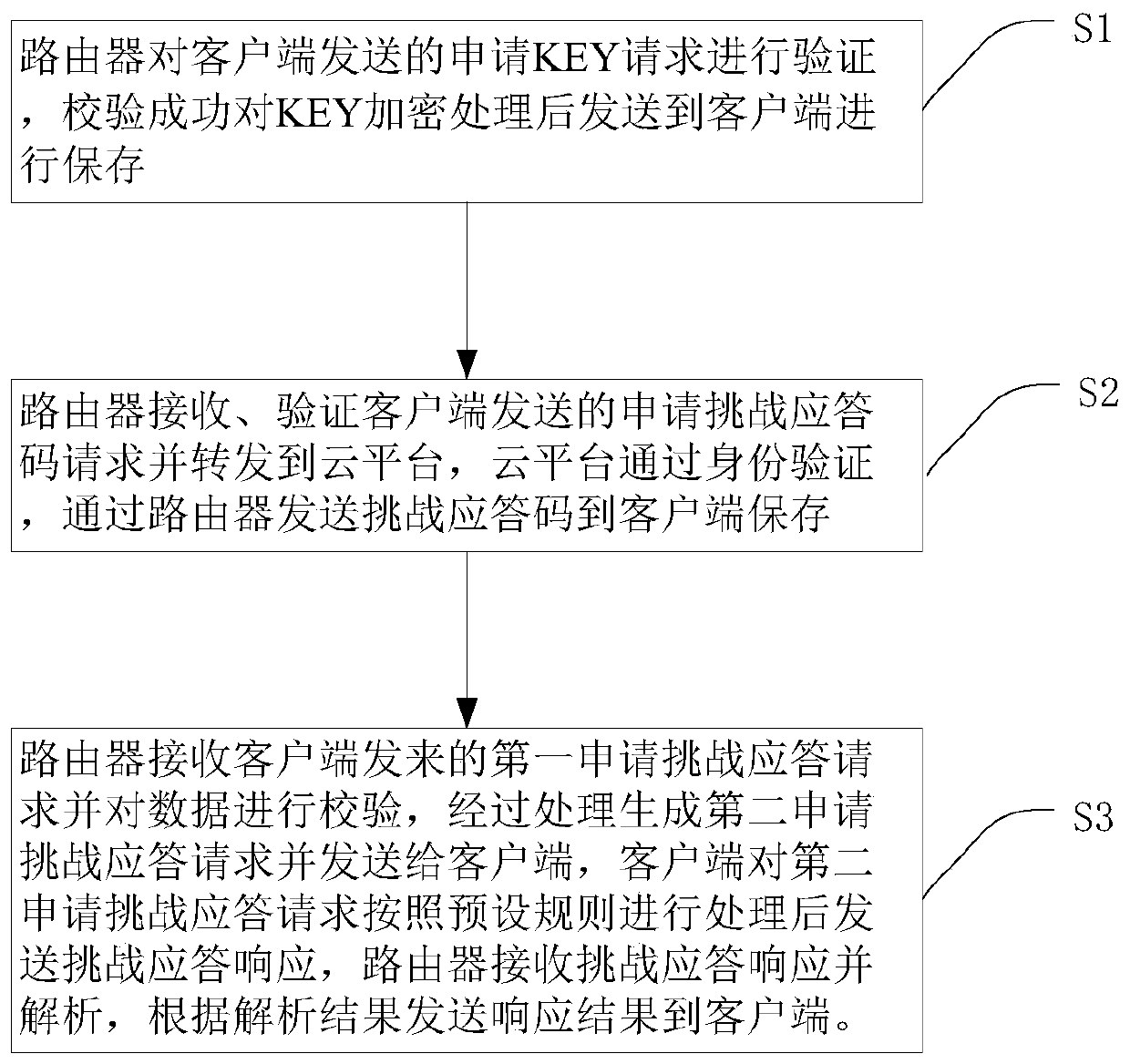
[0059] Embodiment 2: as figure 2 As shown, a security protection method based on challenge response is provided, including steps:
[0060] Step S1: the router verifies the application KEY request sent by the client, and the verification succeeds in encrypting the KEY and sending it to the client for storage;
[0061] Step S2: the router receives and verifies the application challenge response code request sent by the client and forwards it to the cloud platform, and the cloud platform passes the identity verification and sends the challenge response code to the client through the router for storage;
[0062] Step S3: The router receives the first application challenge response request sent by the client and verifies the data, generates a second application challenge response request after processing and sends it to the client, and the client responds to the second application challenge response request according to the preset After the rule is processed, it sends a challenge r...
Embodiment 3
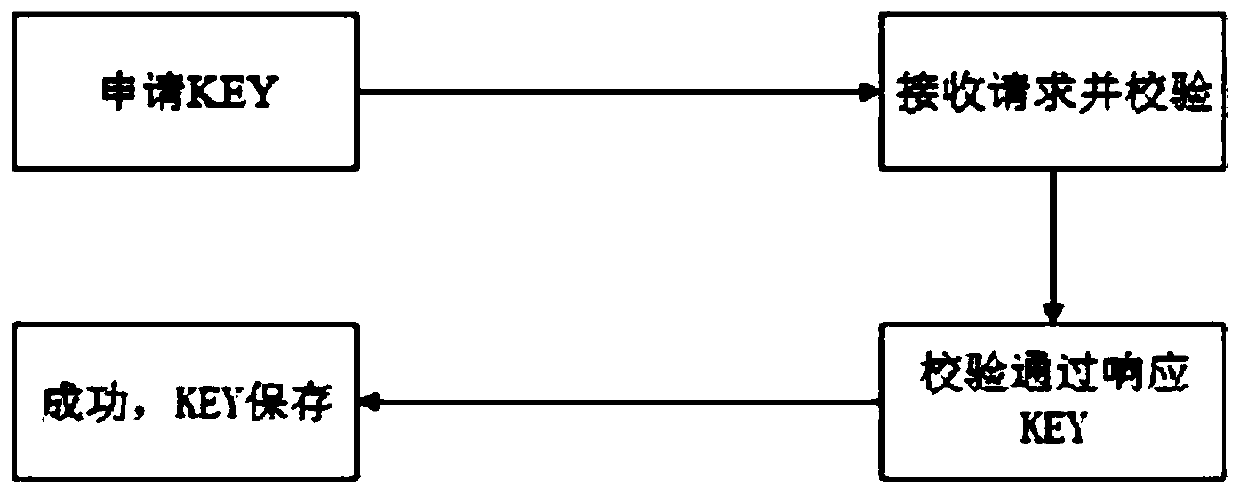
[0065] Embodiment 3: This embodiment is a further optimization done on the basis of the above-mentioned embodiments, as image 3 As shown, the client sends a KEY application request, and the router receives the KEY application request. If the verification passes, the KEY is generated according to the seed input by the client, and the plaintext data is encrypted according to the KEY to form ciphertext data, which is sent to the client for storage.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com