Vehicle-mounted CAN intrusion detection method based on sliding window and CENN
A sliding window, intrusion detection technology, applied in neural learning methods, biological neural network models, protection of internal/peripheral computer components, etc., can solve problems such as high false alarm rate and lack of feature preprocessing methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
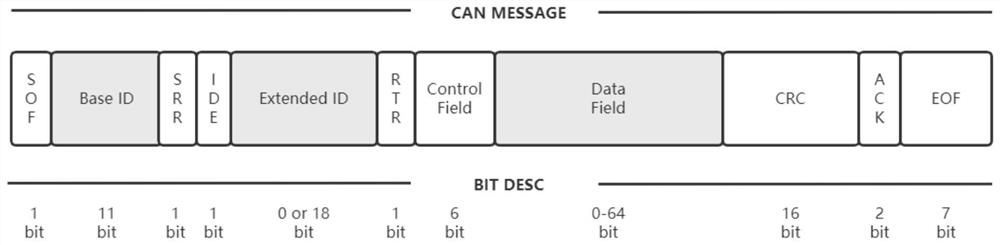
[0038] This embodiment provides an implementation of setting a square window according to the obtained feature size and obtaining the features of the original data according to the sliding window. Perform data conversion and convert the data into binary data, where CAN ID occupies 29 bits, and less than 29 bits will be filled with 0. For 64-bit CAN Data, it is converted in the same way as CAN ID, that is, CAN Data occupies 64 bits, and less than 64 bits will be filled with 0.
[0039] The obtained binary information is expanded, that is, the sum of CAN ID and CAN Data converted binary dimensions is used as the expanded feature size.
[0040] Divide all data records into square windows, where each window is a 93x93 two-dimensional matrix, and set the processing window size to a 93x93 square matrix, where the kth window is expressed as:
[0041]
[0042] Among them, SW k Indicates the kth window, x {i,j} The binary representation of the raw data, its value is 0 or 1.
[0...
Embodiment 2
[0047] On the basis of Embodiment 1, this embodiment provides a method for predicting data based on a convolutional encoder neural network.
[0048] In this embodiment, the encoding part of the convolutional neural network includes an encoder and an Inception-Resnet structure, and the encoder includes two convolutional layers and two pooling layers for reducing the sliding window from 93×93×1 dimension to To 6×6×64 dimension; Inception-Resnet structure, including 3 parallel convolutional layers, used to reduce the data from 6×6×64 dimension to 3×3×64 dimension.
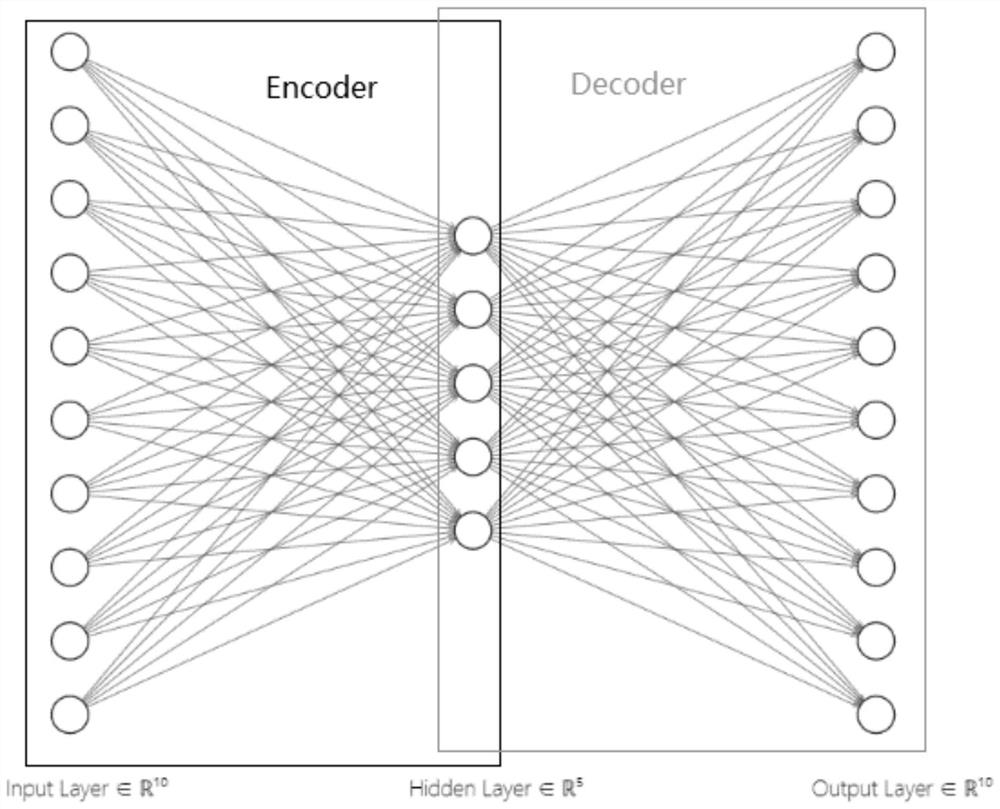
[0049] The convolutional encoder network (CEN) proposed by the present invention is composed of the basic structure of CNN and the partial structure of autoencoder (AutoEncoder). AutoEncoder has the ability to capture nonlinear dependencies and reduce feature size. Such as image 3 As shown, AutoEncoder is divided into encoder and decoder. The implementation of encoder and decoder is described as follows:
[0050] ...
Embodiment 3
[0054] In this embodiment, on the basis of Embodiment 2, the prediction result obtained by the convolutional neural network is further described.
[0055] Studies have shown that dropout (half of the hidden node values are set to 0) is a better choice for training deep neural networks, because it can avoid overfitting and improve the accuracy of the underlying neural network. Therefore, this embodiment first expands the network (corresponding to Figure 5 Average pooling in the previous operation), then use Dropout to prevent the model from overfitting, and output the result to the fully connected layer, and use SoftMax to obtain the training result.
[0056] exist Figure 5 Among them, the Encoder Structure part is the encoder, which reduces the dimensionality of the input 93×93×1 dimensional data to 47×47×32 through the convolutional layer (Covn1), and becomes 24 through a maximum pooling layer (Max-pooling). ×24×32 dimensions, then converted to 12×12×64 dimensions throu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com