Offline signature authentic identification method and system based on multi-feature metric learning
A metric learning, multi-feature technology, applied in the field of digital image processing and handwriting identification, can solve the problems of poor accuracy of offline signature verification system, and achieve the effects of stable verification results, improved accuracy and small errors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
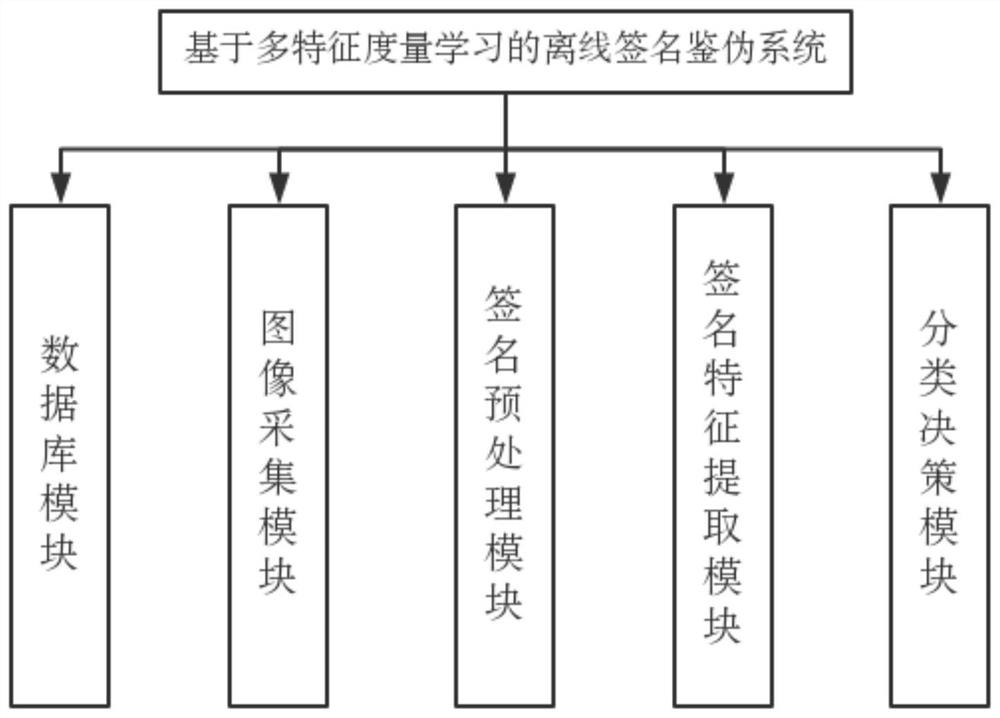
[0044] An embodiment, an offline signature verification system based on multi-feature metric learning, the system adopts a modular design method, the whole system is mainly composed of a database module, an image acquisition module, a signature preprocessing module, a signature feature extraction module and classification decision-making The module consists of five modules (such as figure 1 shown), the specific scheme is as follows:
[0045] Database module: Pre-store digital information such as the user's handwritten signature image, personal information (such as name, gender, ID number), etc., and use these information to verify the authenticity of the signature image to be authenticated in the subsequent authentication process;
[0046]Image acquisition module: use equipment to collect users' personal information and signature images, such as a 5-megapixel self-focus camera, and control the data of the sample handwriting through the software operating system to enter the s...
Embodiment 2
[0050] Embodiment 2: An off-line signature verification method based on multi-feature metric learning.
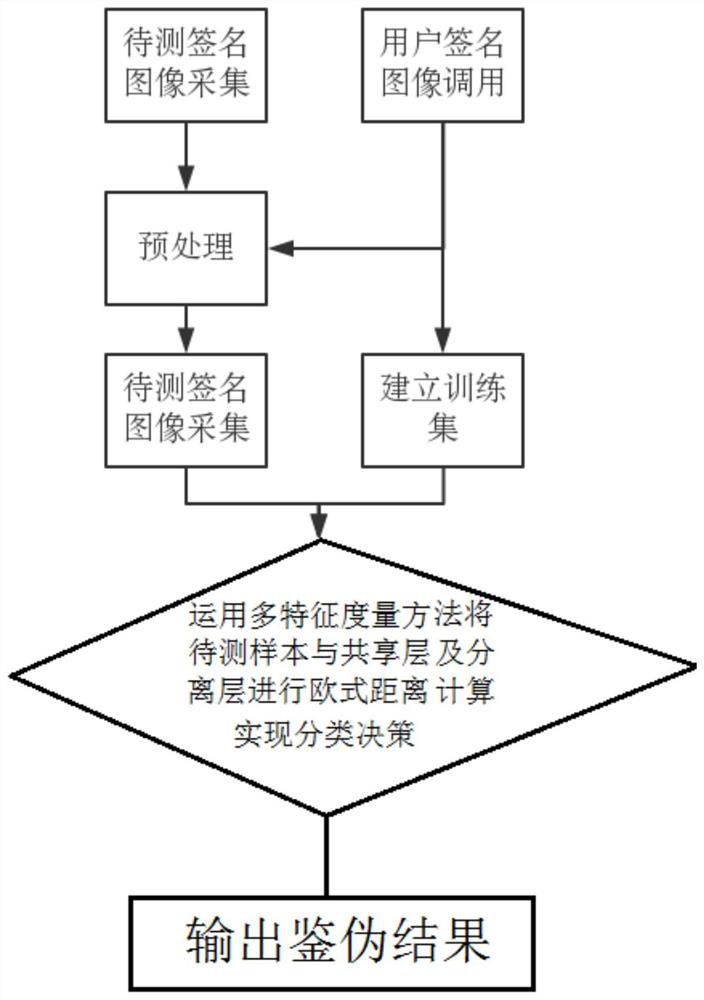
[0051] The flow chart of the counterfeiting method in the embodiment of the present invention is as follows: figure 2 Shown:
[0052] The database used in the specific embodiment includes a sample signature database and collected images of handwritten signatures as samples to be tested. In this embodiment, when the system performs signature verification, first, the signature to be tested is collected and imaged by a high-speed camera. At the same time, according to the user's personal information, 3 reserved real signature images are called from the information database module, and signature images other than the user in the database are called, and each person-time has 3 real images and 3 forged images.
[0053] Step 1: Perform preprocessing on the sample image to be detected and the called signature image respectively. The preprocessing includes processing steps such a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com