Secrecy method and system for displaying file to external user through network
A technology of external users and confidentiality methods, applied in transmission systems, electrical components, digital data protection, etc., can solve the problems of large investment, poor timeliness of acquisition, waste, etc., and achieve the effect of preventing leakage, enhancing confidentiality, and avoiding leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
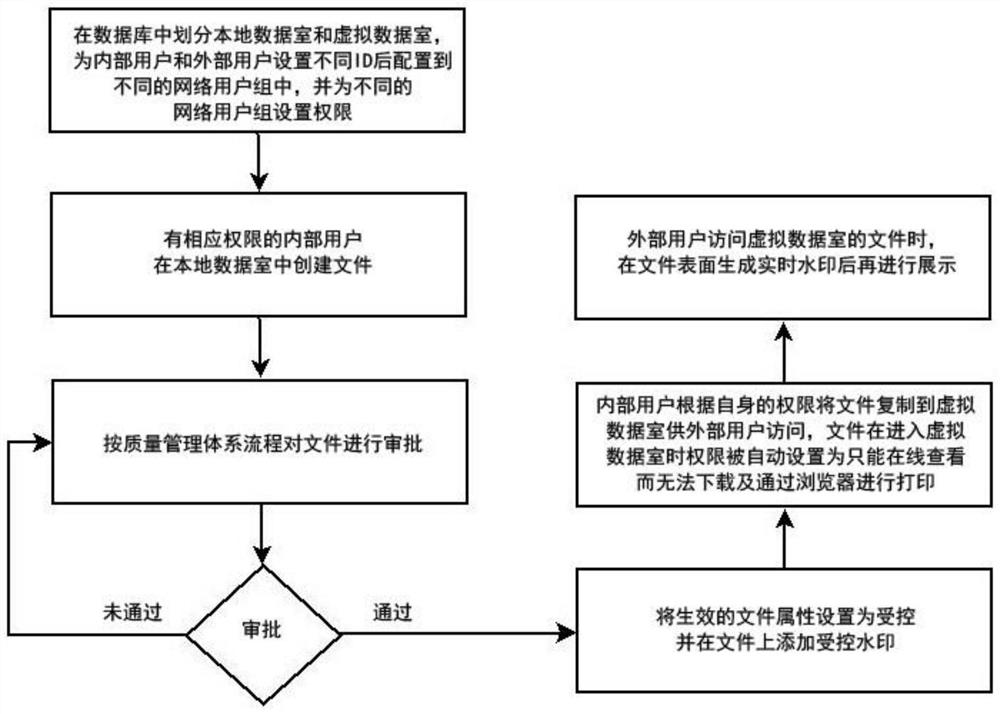
[0044]Embodiment 1: Divide the local data room and the virtual data room in the server-side database, and configure the internal users and external users to use one of their names, companies, account names, or a combination of any two or more of them as IDs and configure them in different In the network user group, and set permissions for different network user groups; so that internal users have different file approval, operation and access permissions and connection permissions of the local data room and virtual data room, and external users have different file access permissions and virtual data rooms. The connection authority of the data room; internal users with authority create files in the local data room; the user group with approval authority approves the file according to the quality management system process, and the file becomes effective if it passes the approval, and the file is modified until it passes the approval ;Set the effective file attribute to controlled,...
Embodiment 2
[0045] Embodiment 2: The user can combine the system of the present invention with various types of internal office management systems of oneself, and directly import the files (such as word files, wps files, pdf files, picture files) of oneself originally into the database, and approval can be set The document will take effect after any user in the network user group of internal users completes the approval process or a certain number of users complete the approval process in order. The user uses an electronic signature to complete the approval process. The electronic signature is a biometric signature and a password. Signature or its combination, biometric signature includes handwriting, appearance, pupil, other steps are the same as embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com