Security risk state analysis method and system for sensing layer of electric power internet of things
A power Internet of Things and security risk technology, applied in the field of Internet of Things, can solve problems such as reducing the security level of the perception layer, destroying smart terminals, and not being able to consider information security too much, so as to achieve enhanced intelligence and accuracy, and comprehensive and accurate analysis results , Intelligent and fast results in the analysis process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
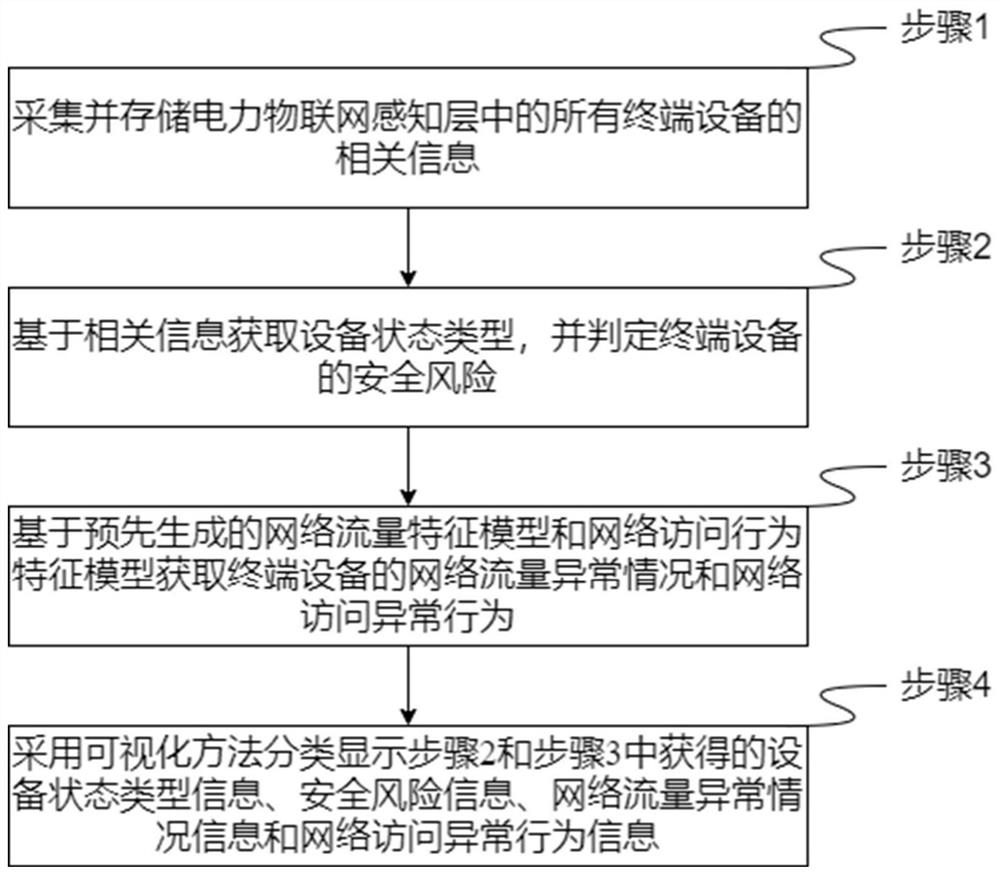
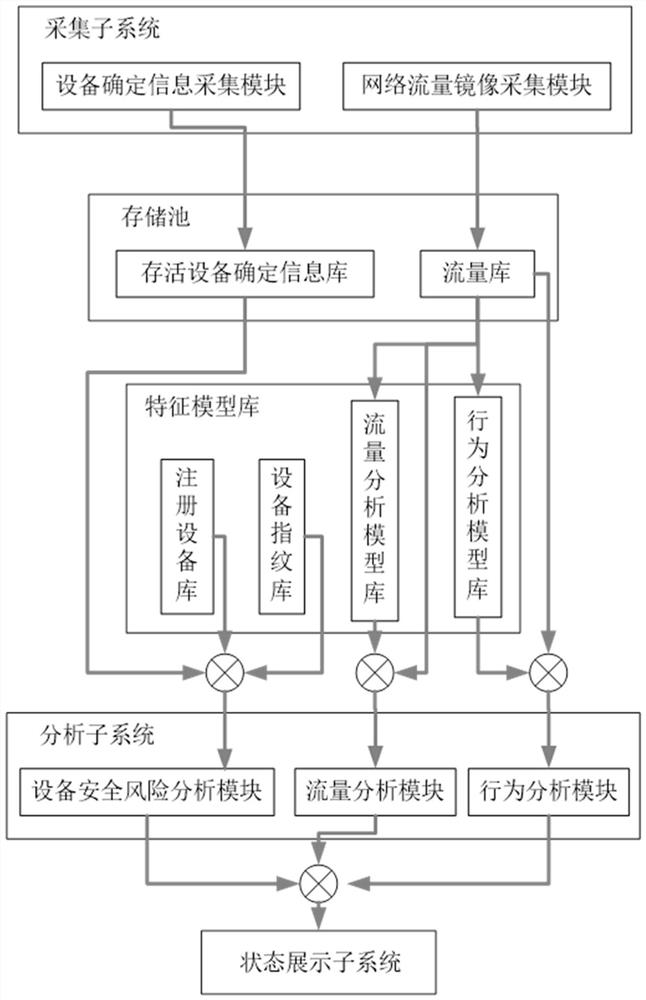
[0030] The application will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solutions of the present invention more clearly, but not to limit the protection scope of the present application.
[0031] There are various terminal devices included in the sensing layer of the electric power Internet of Things adopted in the present invention. For example, terminal equipment includes charging POS machine (Point Of Sale, point of sale terminal), ATM machine (Automatic Teller Machine, automatic teller machine), power transmission status monitoring terminal, power substation status monitoring terminal, power consumption information collection terminal, video terminal, Smart meters, IoT security access control terminals, RTU (Remote Terminal Unit, remote terminal unit) and FTU (FeederTerminal Unit, feeder terminal unit), etc. These devices usually realize the connection and data transmission with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com