Electricity stealing prevention monitoring method and system based on electricity utilization big data
A technology of electricity consumption data and monitoring system, which is applied in the field of electricity theft monitoring, can solve problems such as large errors, weak pertinence, and poor effects, and achieve the effects of reducing detection costs, maintaining social fairness, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
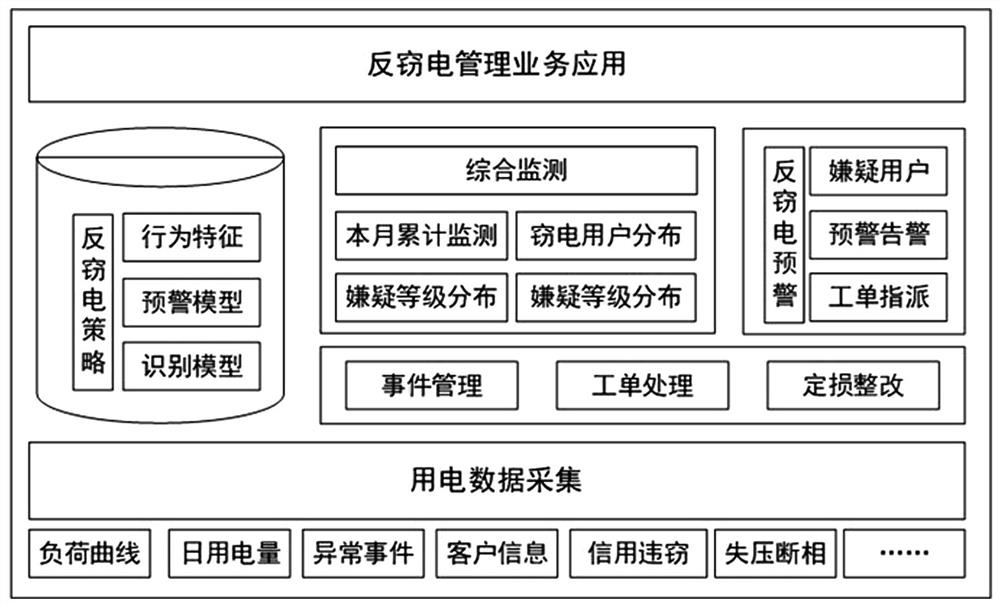
[0043] The present invention is an anti-stealing electricity monitoring system based on electricity consumption data, such as figure 1 as shown, figure 1 It is the overall framework and flow diagram of the present invention.
[0044] The anti-stealing electricity monitoring system based on electricity consumption data in the present invention builds an anti-electricity theft management business application system, including an electricity consumption data acquisition module, an anti-electricity theft strategy management module, a comprehensive monitoring module, an anti-electricity theft abnormal warning module, and an event management module And the service module of damage assessment and rectification.
[0045] The power consumption data acquisition module is connected to an external service database through a local area network, and collects relational index data composed of load curves, daily power consumption, abnormal events, customer information, credit theft, voltage ...
Embodiment 2
[0054] The embodiment of the present invention also provides an anti-stealing electricity monitoring method based on electricity consumption data, such as figure 1 as shown, figure 1 It is the overall framework and flow diagram of the present invention.
[0055] The inventive method comprises the following steps:
[0056] Step 1. Build an anti-theft management business application system.
[0057] The present invention builds an anti-stealing power management business application system, uses big data analysis technology and computer algorithms to monitor user power consumption data in real time, builds intelligent power consumption abnormality analysis and anti-stealing power applications, and analyzes power consumption information and tables in multiple dimensions. Data information such as meter status and line loss can detect electricity theft events in a timely and effective manner, and quickly locate users suspected of electricity theft. Through the construction of int...
Embodiment 3
[0075] Based on the same inventive concept, an embodiment of the present invention also provides a computer storage medium, on which a computer program is stored, and when the computer program is executed by a processor, the one based on The steps of the anti-stealing electricity monitoring method of electricity consumption data.
[0076] Those skilled in the art should understand that the embodiments of the present application may be provided as methods, systems, or computer program products. Accordingly, the present application may take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, the present application may take the form of a computer program product embodied on one or more computer-usable storage media (including but not limited to disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com