Data protection method and system based on computer intelligent algorithm
A data protection and intelligent algorithm technology, applied in digital data protection, computer security devices, computing, etc., can solve problems such as threats to personal privacy or business secrets, illegal operations, cumbersome operation processes, etc., to achieve real-time protection of data security and avoid theft Take and tamper, the effect of simple operation process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
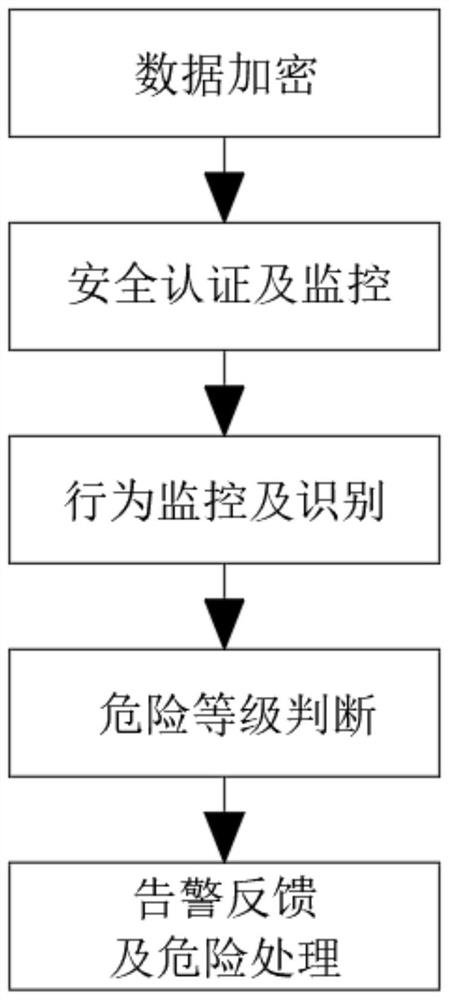
[0050] refer to figure 1 , the present embodiment discloses a data protection method based on a computer intelligent algorithm, and the specific steps of the data protection method are as follows:
[0051] First: data encryption, which encrypts the uploaded computer data through the data encryption method, obtains the encrypted computer data, and stores it in the computer for preservation;
[0052]Specifically, the data encryption method is implemented based on the joint use of symmetric encryption algorithms and asymmetric encryption algorithms. It performs symmetric encryption on the uploaded computer data through the DES algorithm and a private key to form symmetric encrypted data, and then passes the ECC algorithm and Combined with the public key for asymmetric encryption to obtain encrypted computer data.
[0053] Then: security authentication and monitoring, perform security login authentication on the user through the security authentication method, if the user authent...
Embodiment 2
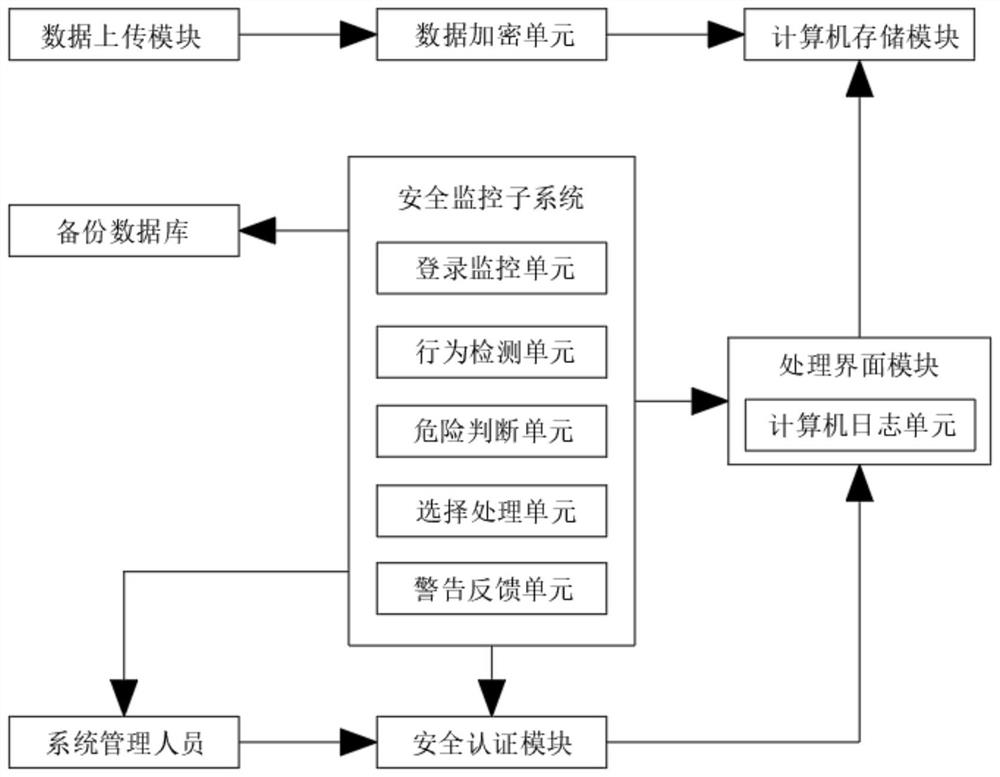
[0064] refer to figure 2 , the present embodiment discloses a data protection system based on computer intelligent algorithms, including a data upload module, a data encryption module, a computer storage module, a security authentication module, a processing interface module, a security monitoring subsystem and a backup database;
[0065] The data upload module is used for computer owners to upload computer data to be stored; the data encryption module is used for encrypting computer data to generate encrypted computer data; the computer storage module is used for storing encrypted computer data;
[0066] The security authentication module is used to perform security login authentication on the user through the security authentication method;
[0067] The processing interface module is specifically a computing operation interface, which includes a computer log unit for recording user and computer background behaviors in real time;
[0068] The safety monitoring subsystem inc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com