Electronic data security system and method based on mobile terminal
A technology of electronic data and mobile terminals, applied in digital data protection, electronic digital data processing, digital data authentication, etc., can solve the problems of lack of judicial authentication, lack of password security protection means, lack of necessary technology, etc., to ensure the legitimacy of identity , Guarantee legitimacy and authority, and ensure the effect of key security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
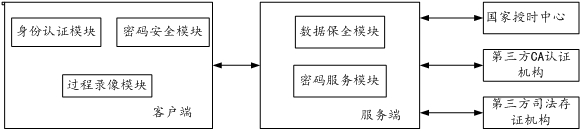
[0043] In one or more implementations, a mobile terminal-based electronic data security system is disclosed, referring to figure 1 , including server and client;
[0044] Wherein the client is set on the mobile terminal, and the client includes:
[0045](1) The identity authentication module is configured to call the biometric device of the mobile terminal for identity authentication, access control and real-name authentication, perform data interaction and key collaborative operation with the server, and obtain a digital certificate as a digital identity certificate;
[0046] Specifically, the identity authentication module includes:
[0047] ①The biometric identification unit is configured to implement identity authentication and access control on the client key information and personal information by invoking the biometric identification device (such as fingerprint identification, voiceprint identification or face recognition) of the mobile terminal;
[0048] ② The real-n...
Embodiment 2
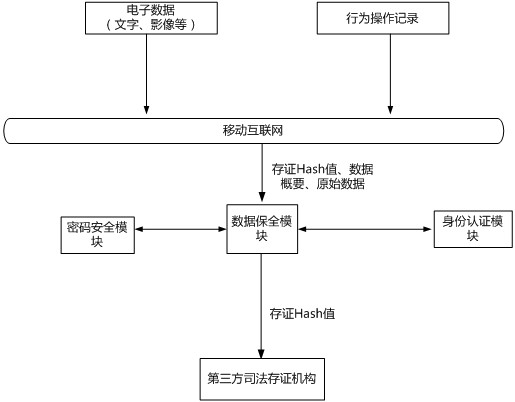
[0098] In one or more implementations, a mobile terminal-based electronic data preservation method is disclosed, including the following process:
[0099] (1) Receive the identity authentication request and perform real-name identity authentication on the client user;
[0100] (2) After the identity authentication is successful, generate a local key, and send a digital certificate application request and the local key to the server, so that the server submits a digital certificate authentication request to the third-party CA certification authority; at the same time, the receiving server The returned digital certificate is encrypted and stored;
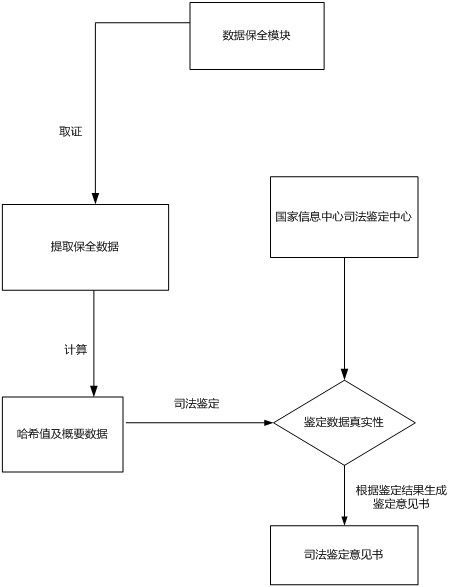
[0101] (3) Obtain the signature value through the collaborative operation of key shares, generate time stamps and electronic signatures for the preserved electronic data, and locally encrypt and store the original text of the preserved electronic data, the hash value of the original text, digital signature information and identity aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com