Attack detection method and device for privacy protection-oriented cyber-physical system
A cyber-physical system and attack detection technology, applied in the field of network information security, can solve problems such as large attack space, and achieve the effect of good detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
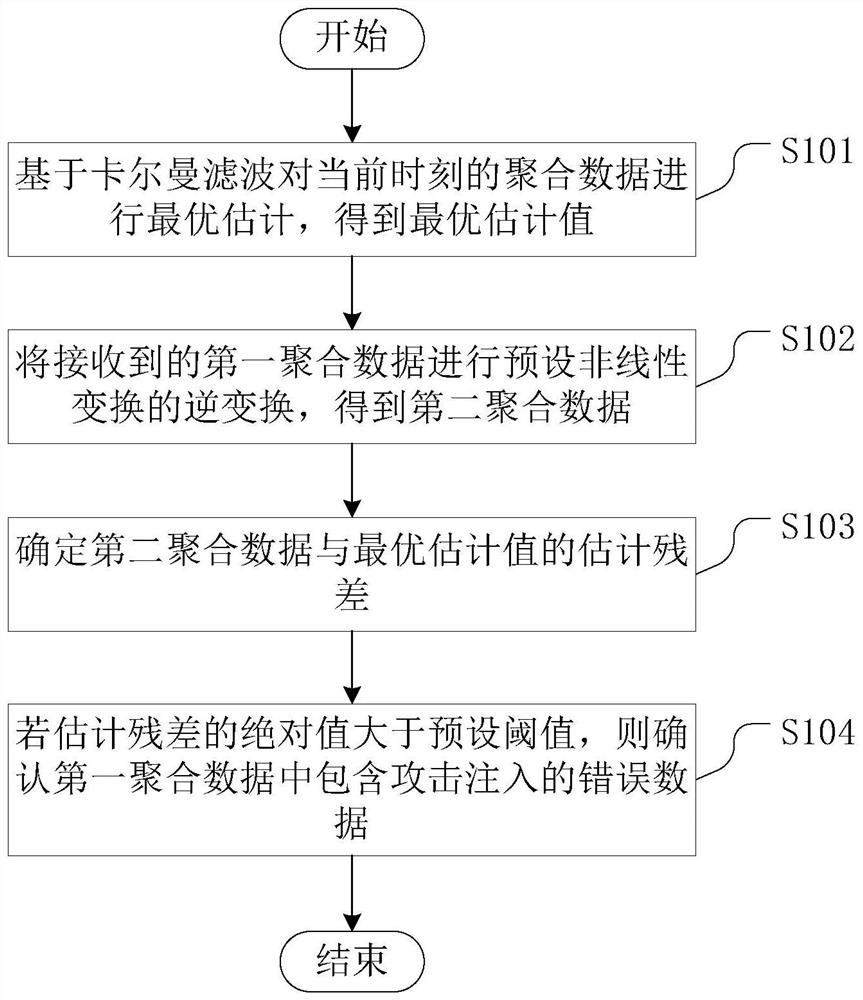
[0082] figure 2 A block diagram of an attack detection method for a privacy-protected cyber-physical system provided by an embodiment of the present application.
[0083] As mentioned in the above-mentioned embodiment, the data sender aggregates the data with noise Perform a preset nonlinear transformation, specifically, the noise-added aggregation data can be Multiply by non-linear transformation multipliers generated based on convention rules On this basis, preferably, the non-linear transformation multiplier can specifically adopt a value generated by a pseudo-random number generator; the seed of the pseudo-random number generator is generated from agreed data.
[0084] Generate non-linear transformation multipliers by employing a pseudo-random number generator On the basis of the distributed differential privacy mechanism, the Moving Target Defense (MTD) method is integrated, which increases the randomness and unpredictability of the aggregated data to be transmitte...
Embodiment 3
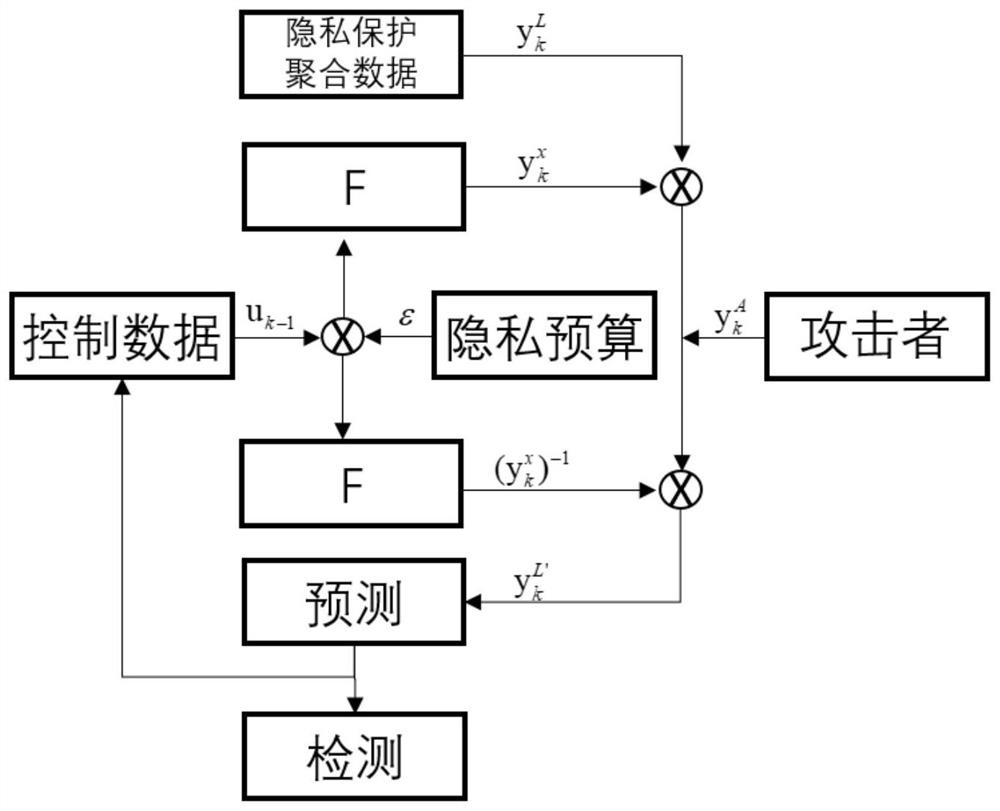
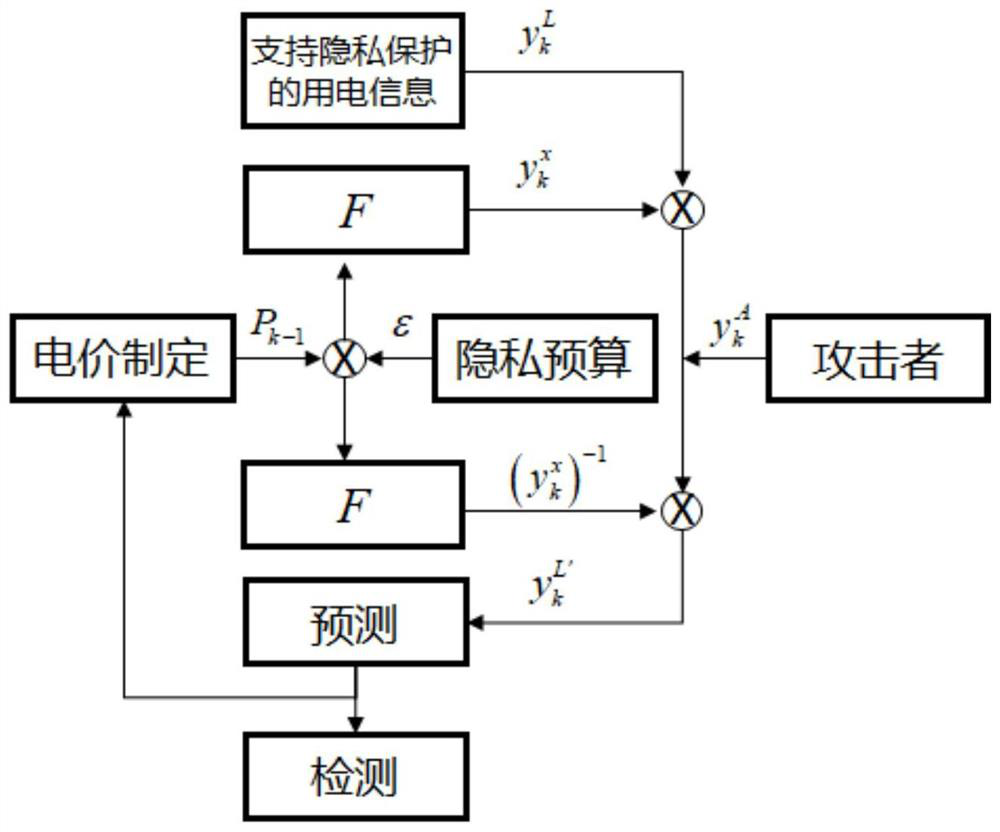
[0089] image 3 It is a block diagram of another attack detection method for a privacy-protected cyber-physical system provided by the embodiment of the present application.
[0090] The foregoing embodiments introduce methods for attack detection in cyber-physical systems. In practical applications, today's smart grid, as a kind of cyber-physical system, also faces two major problems of privacy protection and attack detection.
[0091] Today's smart grid combines network and information technology, and connects electricity consumers and electricity suppliers through new monitoring equipment such as smart meters. The power supply side can effectively control the marginal power supply cost through the real-time pricing mechanism of electricity price, and the power consumer can also formulate more refined power consumption strategies through it. Power providers can formulate more reasonable electricity price policies by digging deeper into more accurate and finer-grained elect...
Embodiment 4
[0109] Figure 4 It is a schematic structural diagram of an attack detection system for a privacy-protected cyber-physical system provided by an embodiment of the present application.
[0110] Such as Figure 4 As shown, the attack detection system for privacy-protected cyber-physical systems provided by the embodiment of the present application includes a system controller 401 and a control terminal 402;
[0111] The control terminal 402 is used to convert the real-time data collected by the monitoring terminal 403 into noise-added aggregated data based on the differential privacy mechanism, perform preset nonlinear transformation on the noise-added aggregated data to obtain the aggregated data to be transmitted, and pass the aggregated data to be transmitted through the network communication channel issue;
[0112] The system controller 401 is used to optimally estimate the aggregation data at the current moment based on the Kalman filter to obtain the optimal estimation v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com