Web attack detection method based on NLP
An attack detection and web service technology, applied in the field of wide area network, can solve problems such as false positive verification, difficulty increase, network storm, etc., to achieve the effect of ensuring integrity, reducing traffic output, and reducing data pollution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only some, not all, embodiments of the present invention.
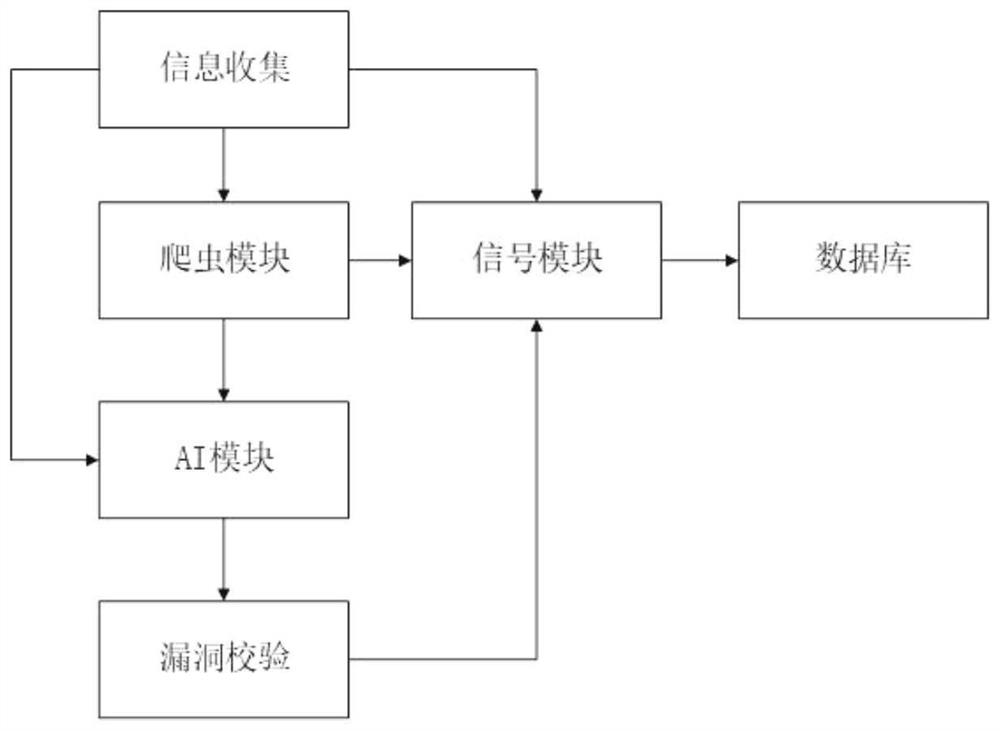
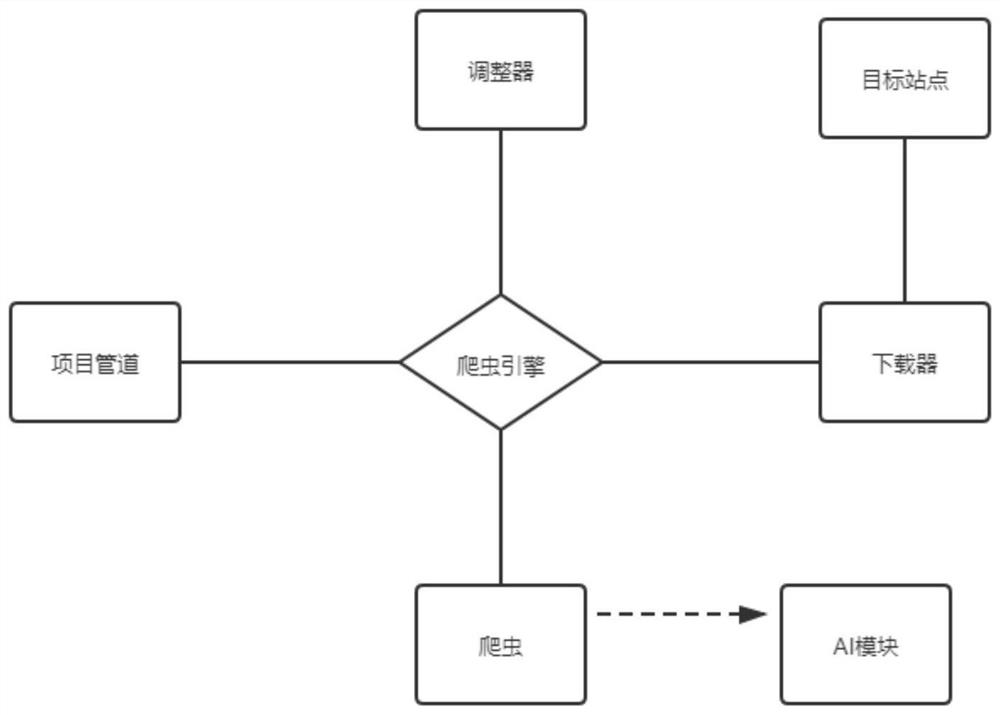
[0026] refer to figure 1 - Figure 4 , a kind of technical scheme that the present invention proposes: a kind of Web attack detection method based on NLP, comprises the steps:
[0027] S1. The user enters the target information on the client, and sends the user's input to the server through an HTTP request. After the server verifies the data, it stores the scanning information in the database, and sends it to the scanning engine through the message queue to complete the scanning;
[0028] S2. Use NMAP to collect basic information on the target system, including all open ports, port services, operating systems and versions, MAC addresses, and open web service ports, ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap