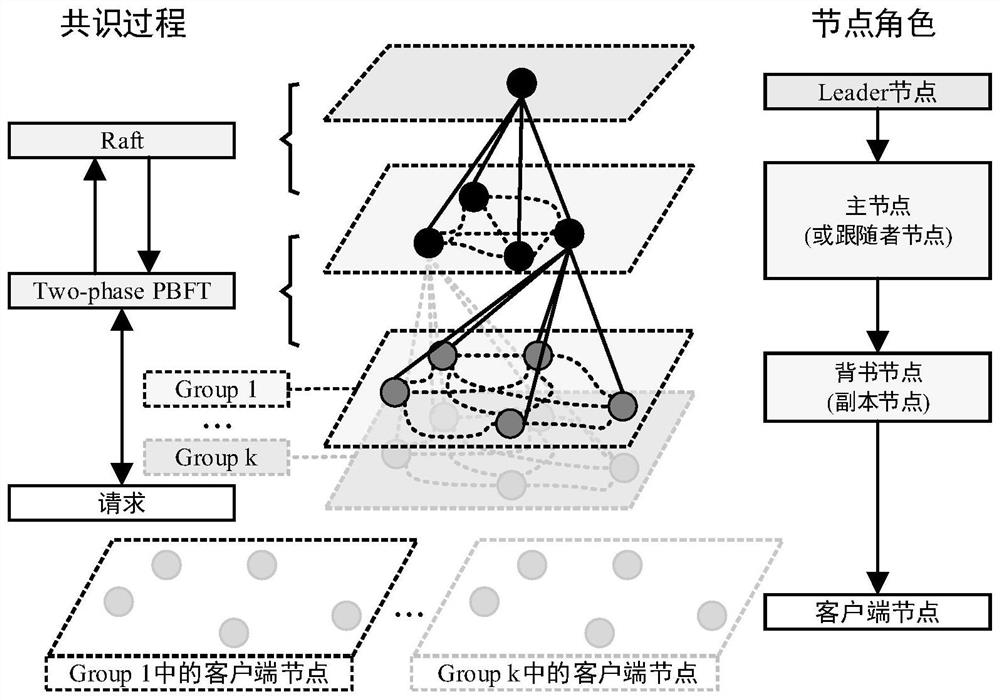
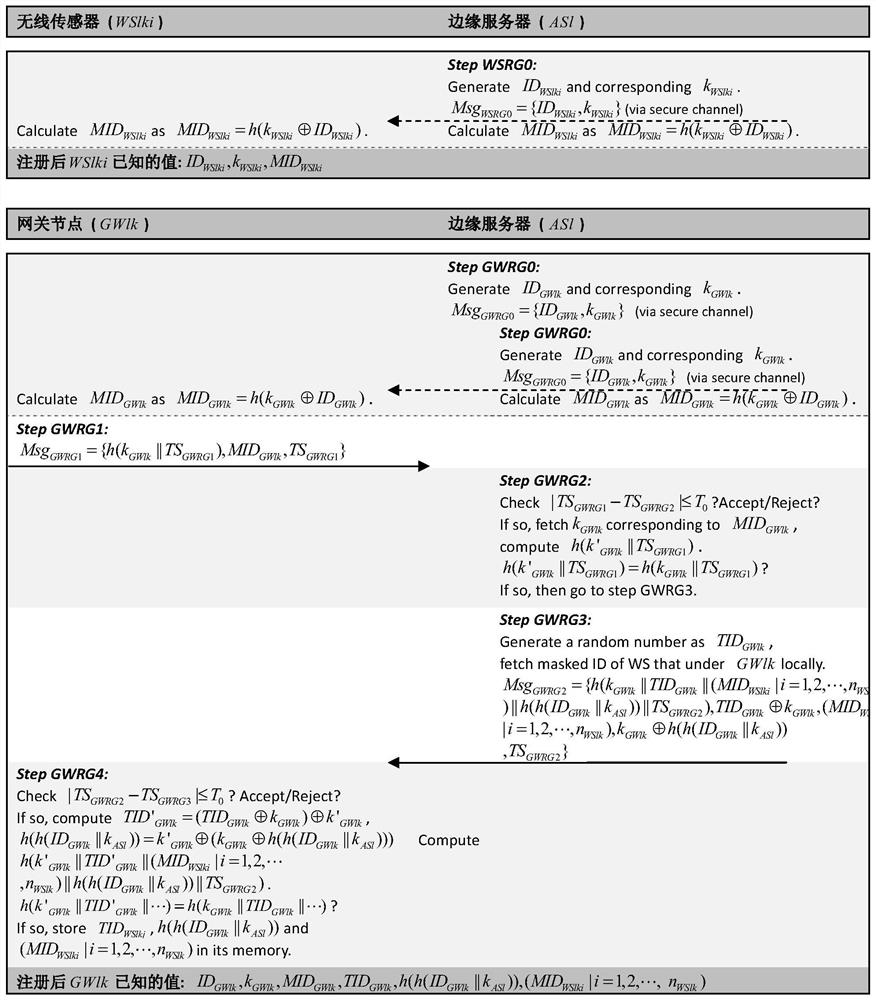
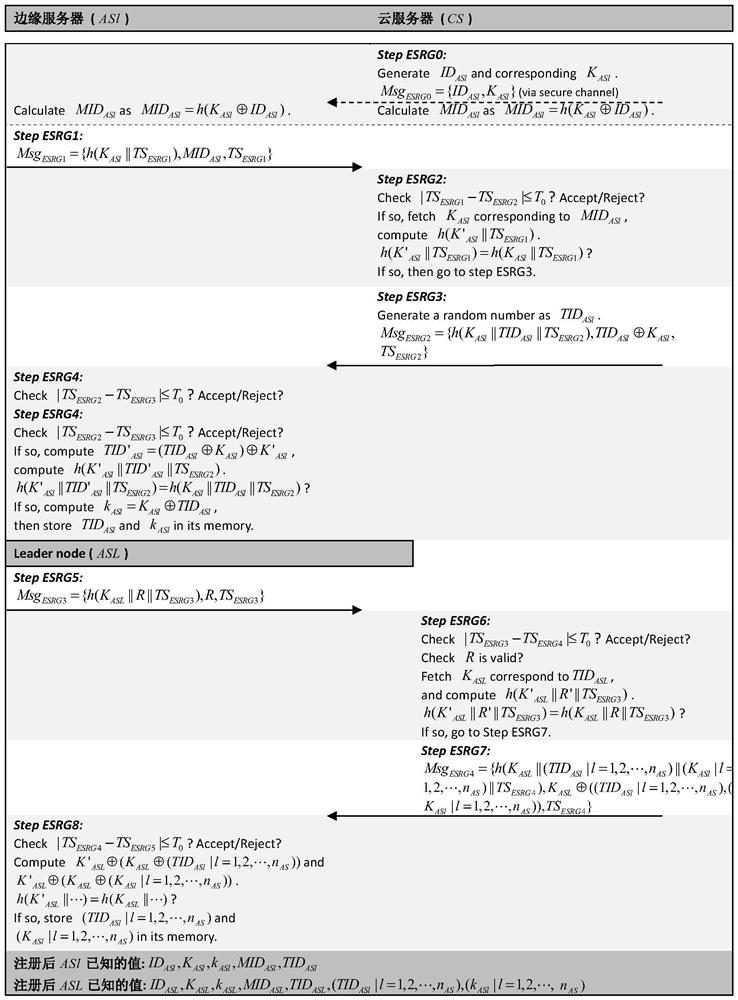
Authentication key protocol of block chain applied to edge of wireless sensor network
A wireless sensor, authentication key technology, applied in network topology, wireless communication, transmission system, etc., can solve problems such as threats that are not suitable for network edge quality information management applications, lightweight solution attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0086] It should be noted that, in the following examples, these documents will be cited:
[0087] [1] Li D, Peng W, Deng W, et al. A blockchain-based authentication and security mechanism for IoT [C]. 2018, 27th International Conference on Computer Communication and Networks (ICCCN), 2018: 1-6.
[0088] [2] Qiongqiong D, Dinghua X, Hongzhou S. Scheme Design of Intelligent Object Authentication Technology Based on Blockchain [J]. Information Network Security, 2018, 18(9):95-101.
[0089] [3] Zhang L, Li H, Sun L, et al. Poster: towards fully distributed user authentication with blockchain [C]. 2017, IEEE Symposium on Privacy-Aware Computing (PAC), 2017: 202-203.
[0090] [4] Li F, Han Y, Jin C. Practical access control for sensor networks in the context of the Internet of Things [J]. Computer Communications, 2016, 89: 154-164.
[0091] [5] Tewari A, Gupta B. Cryptanalysis of a novel ultra-lightweight mutual authentication protocol for IoT devices using RFID tags [J]. The Jour...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com