System and method for identifying authority using relative inquire
A technology of association query and association relationship, applied in the field of network management, it can solve problems such as clear description of difficult-to-contain relationships, complicated relationships, and difficult to adjust inclusive relationships, so as to reduce workload and improve efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the purpose, technical solutions and advantages of the present invention clearer, below in conjunction with embodiment and accompanying drawing, the present invention is described in further detail:
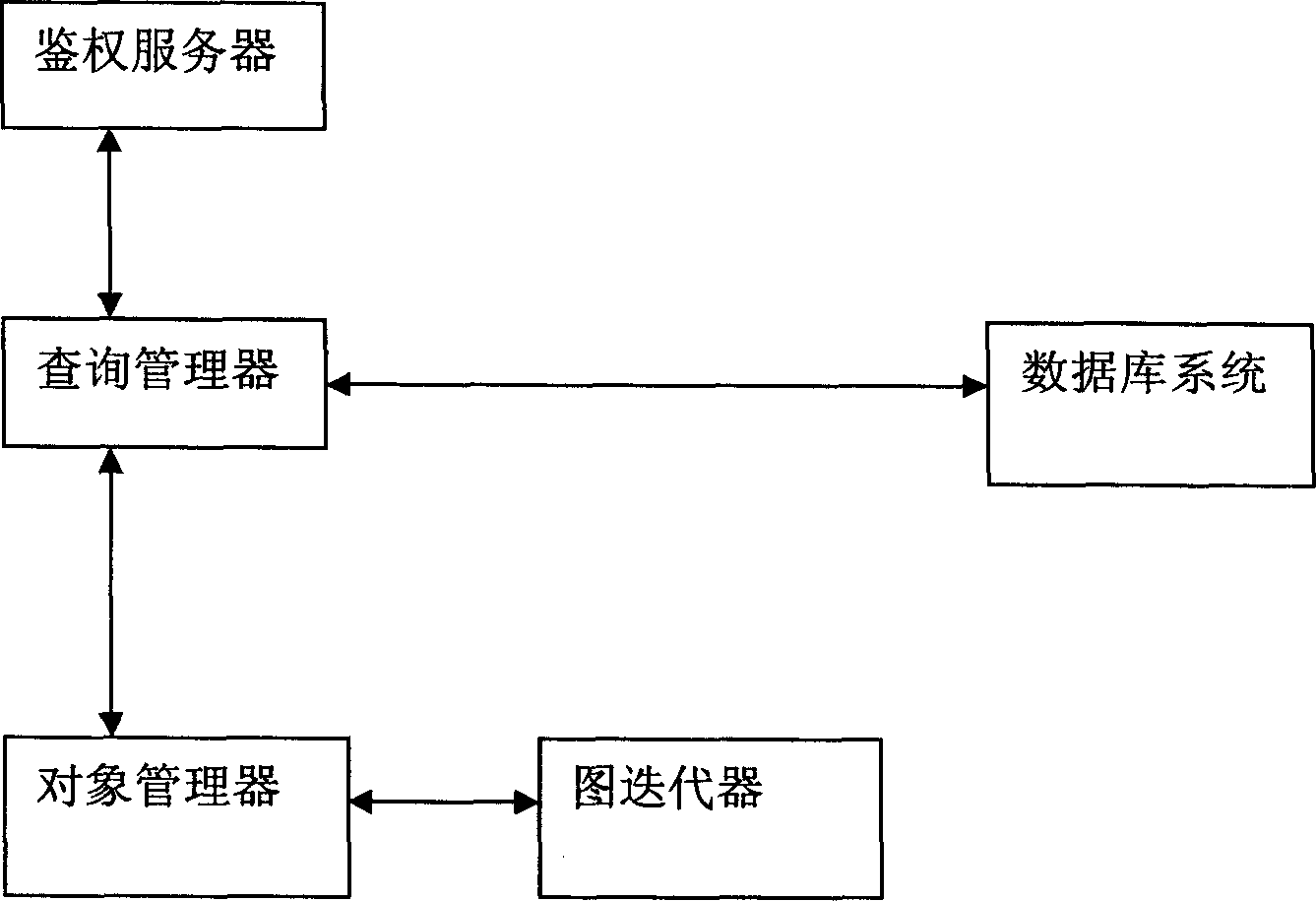
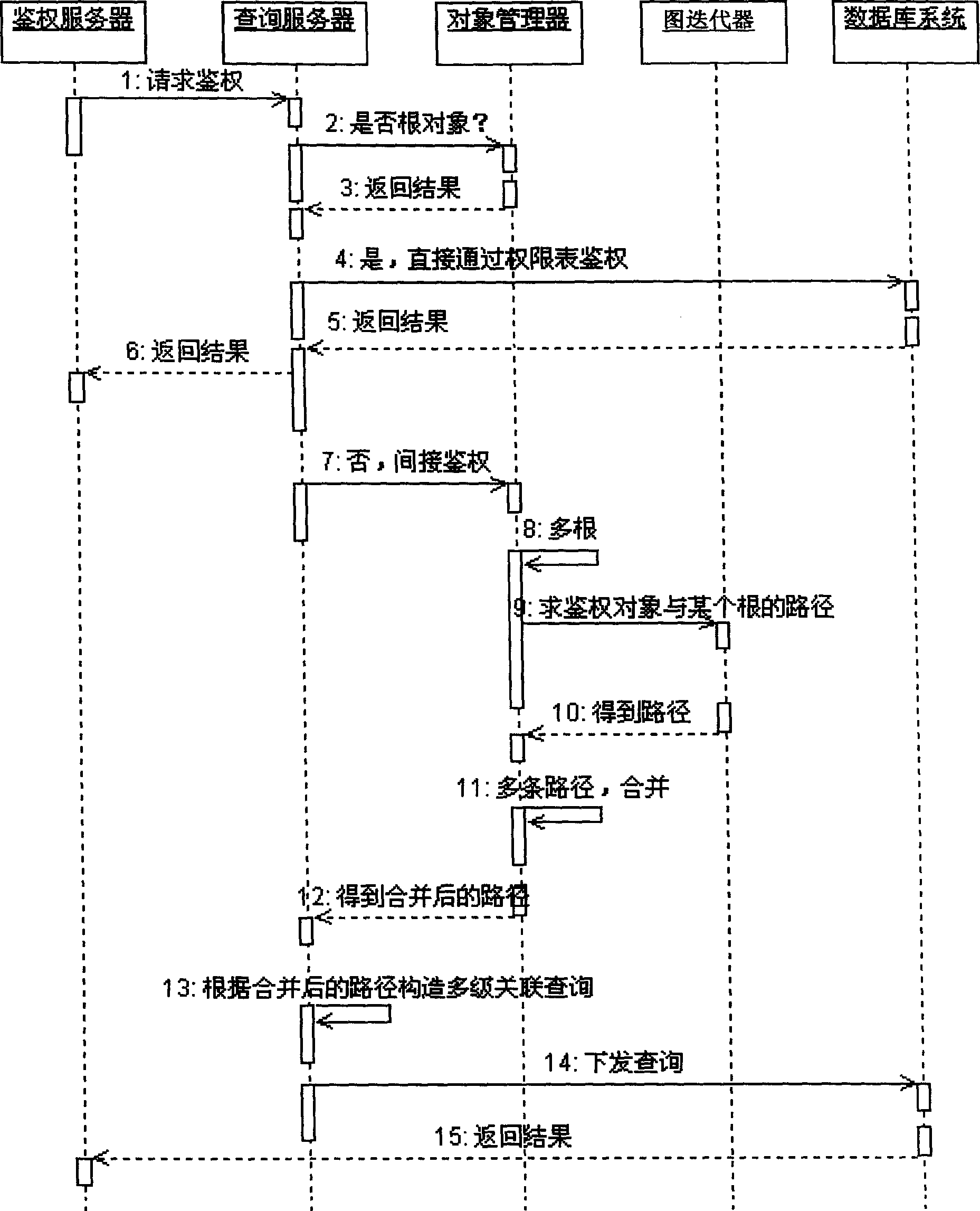
[0028] figure 1 It is a structural schematic diagram of a system for authenticating by using an associated query in the present invention; the system includes an authentication server, a query manager, a database system, an object manager and a graph iterator.
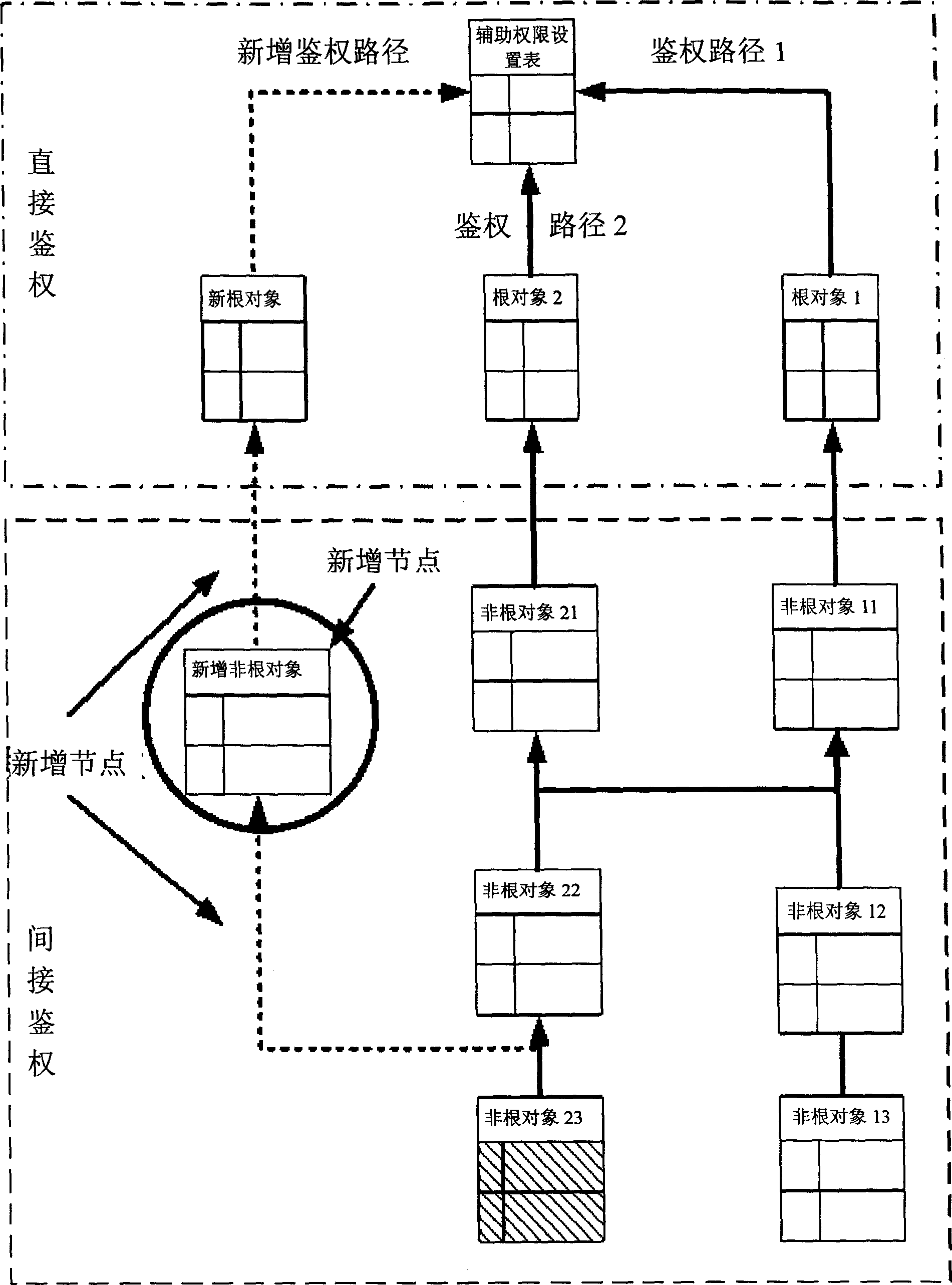
[0029] Among them, the authentication server is a background service program that centrally processes the authentication business logic, which can accept authentication request information from the client (authentication requester), and can perform operations such as login access control, superimposed operation authority control, etc. , and at the same time, it can also perform load balancing in the case of a large number of requests from multiple clients. Wherein, the authentication request infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com