Bidirectional identification method and system
A technology for two-way authentication and system generation, which is applied in the field of two-way authentication without certificates based on bilinear pairings and systems, and can solve problems such as failure to protect user identities, difficulties in public key authentication management, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
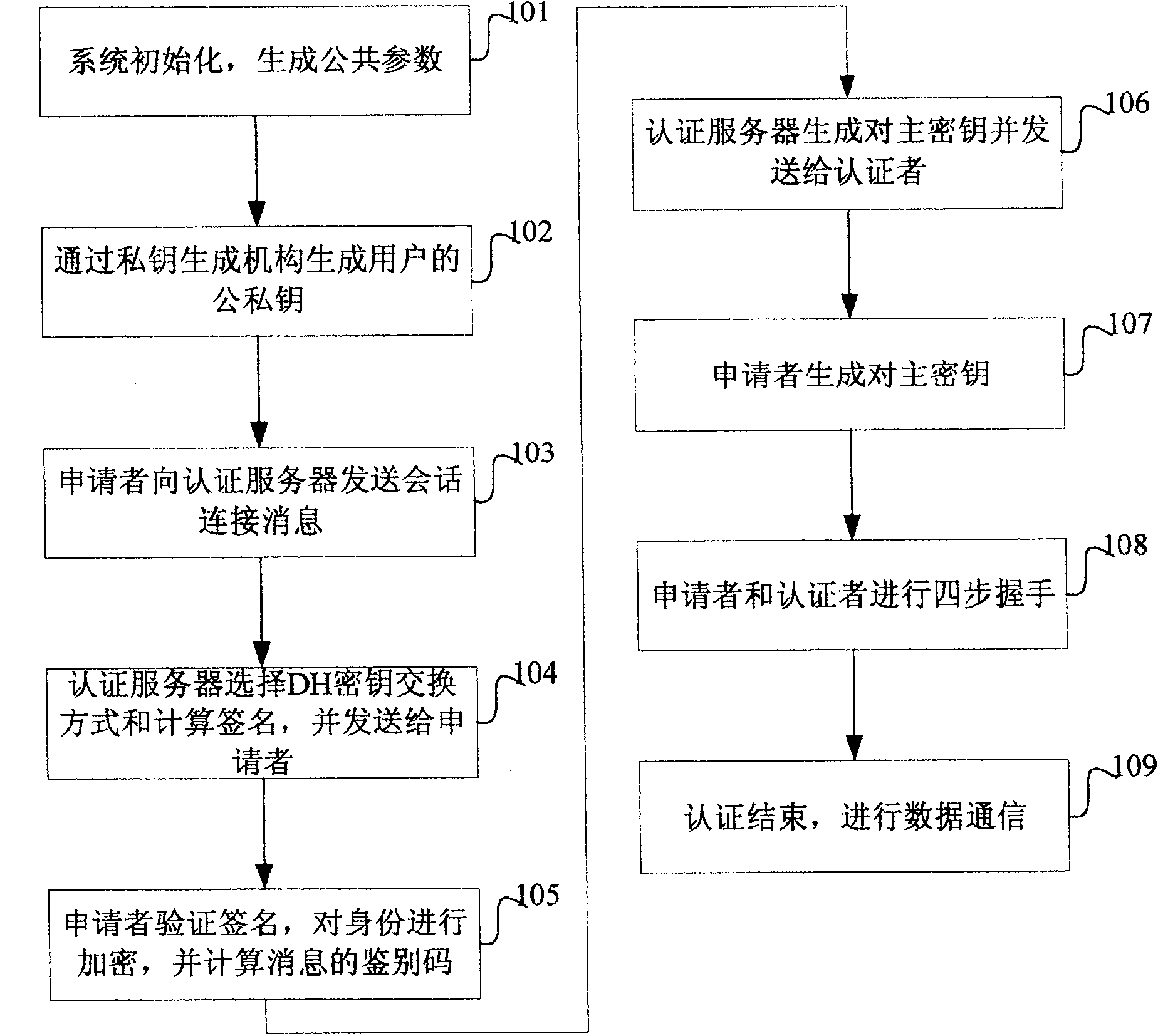
[0108] In order to describe the solution in more detail, below we give a specific example that can be used in 802.11i. This example can be used as a new EAP authentication method. The specific description is as follows:
[0109] 1. The applicant sends a "Supplicant Hello (request session)" message to initiate a session connection. The message contains the protocol version number and the random number N S , session ID, and cipher suite. Cipher suites are some cipher options supported by the applicant. Among them, the key exchange method consists of DH and public key encryption exchange. In the proposed technical solution, it is recommended to use DH exchange as the preferred key exchange method, because of the security of this scheme. better.
[0110] 2. The authentication server responds with an "Authentication Server Hello (request received)" message, makes a choice from the cipher suites supported by the applicant and informs the applicant. After the Hello message, the ser...
Embodiment 2
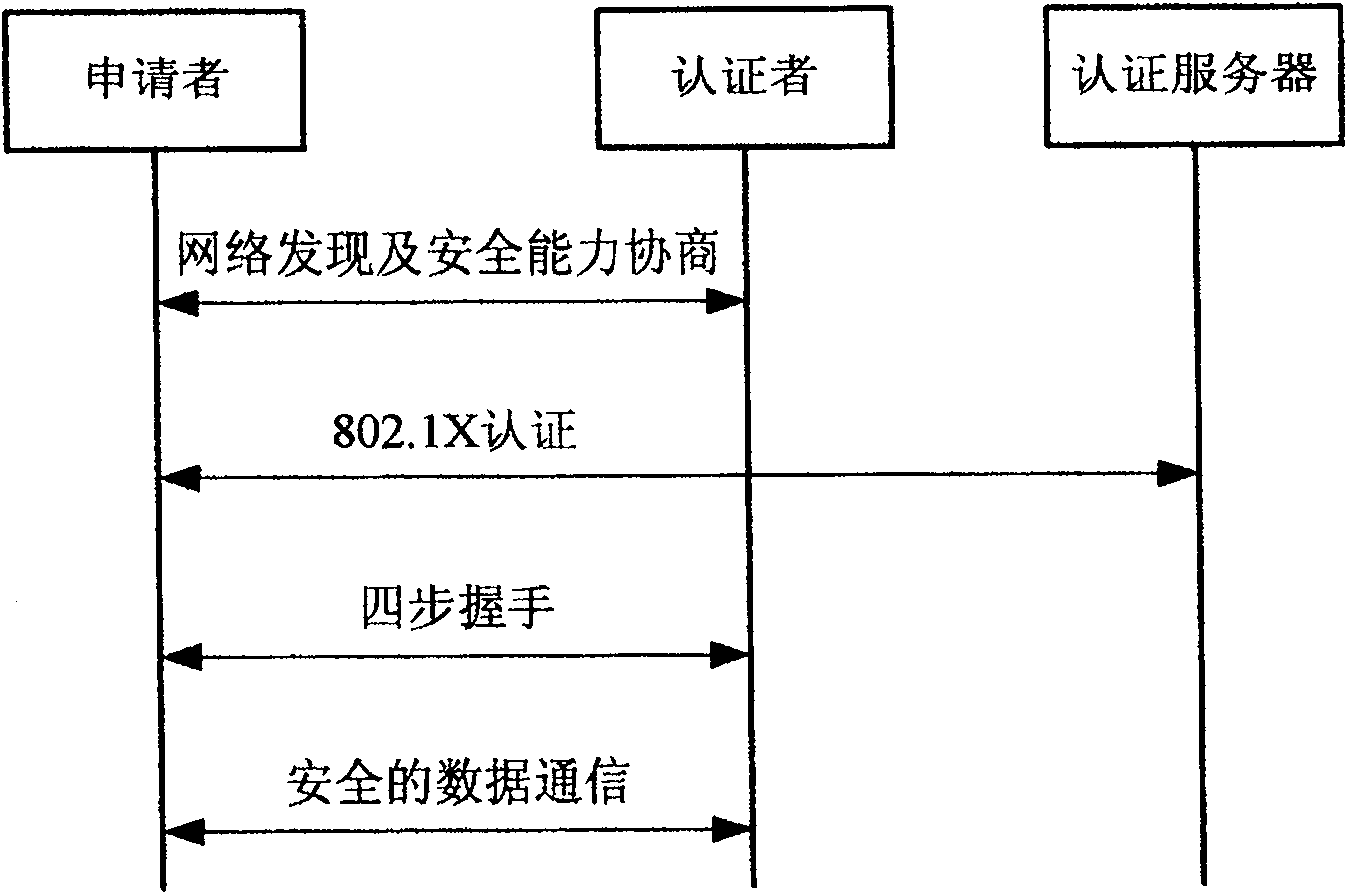
[0116] see Figure 4 , based on the technical solution provided by the present invention and the specific examples in 802.11i, a mobile device preparing to access the current WLAN or WMN will perform the following RSNA establishment process:
[0117] Phase 1: Network Discovery Phase
[0118] At this stage, the applicant has two ways to discover the network access device (Authenticator, authenticator) and its security capabilities. One is passive scanning: the authenticator periodically broadcasts beacon frames (Beacon frames); the other is active scanning: the applicant sends a probe (Probe Request) to each channel, and the other party uses a probe response frame (Probe Response) to perform answer.
[0119] Phase 2: 802.11 Open Systems Authentication and Association Phase
[0120] At this stage, 802.11 open system authentication (802.11Authentication Request, 802.11Authentication Response) is performed between the applicant and the authenticator, and the cipher options in t...
Embodiment 3
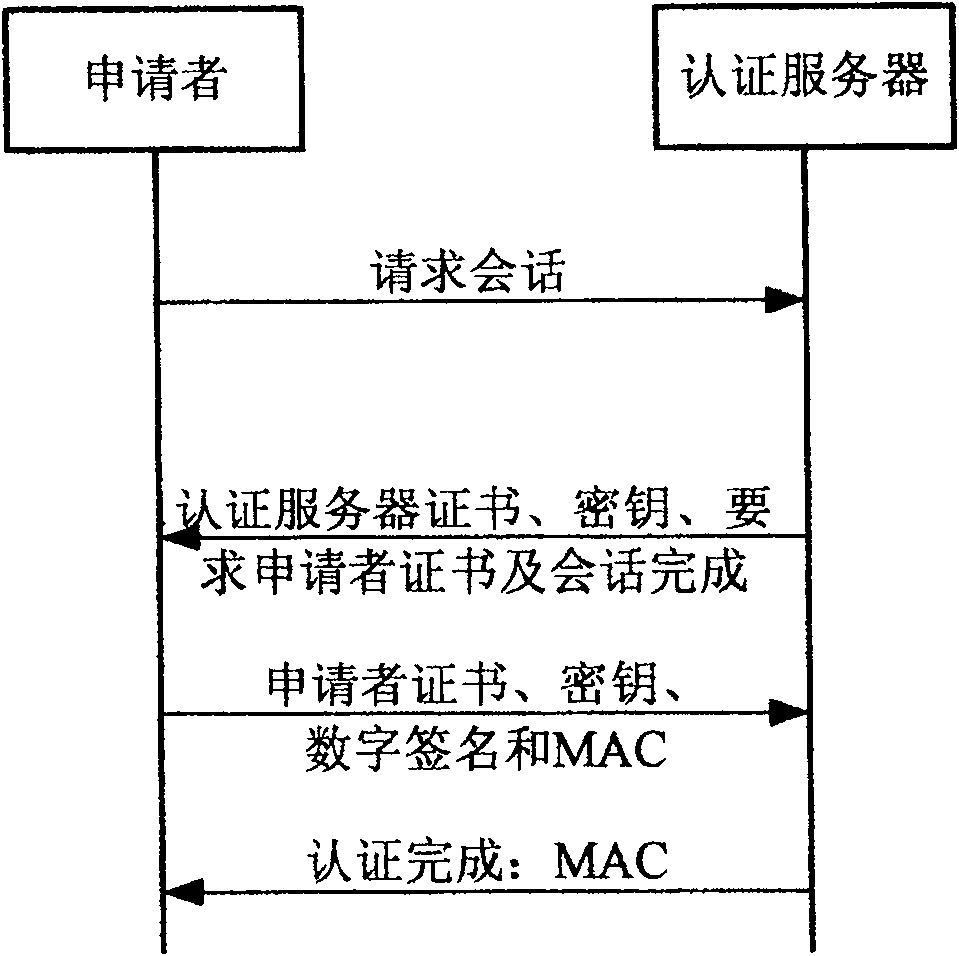
[0142] In order to describe the present invention in more detail, a specific example that can be used in 802.11i is also given, and this example can be used as a new EAP authentication method.
[0143] The specific description is as follows:
[0144] 1. The applicant sends a "session request" message to initiate a session connection, and the message includes the protocol version number, random number, session ID and cipher suite.
[0145] 2. The server replies with a "request received" message, chooses from the cipher suites supported by the applicant and informs the applicant. After the Hello message, the server sends its own identity ID AS . Finally the server sends "session complete" to indicate the end of the Hello message exchange.
[0146] 3 The applicant first selects the shared key MSK between the two parties, and uses it to encrypt his own identity to realize identity protection. At the same time, it is encrypted with the public key of AS ENC ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com