Method for construction of network trust topology based on reliable loop
A construction method and credible technology, applied in the field of computer networks, can solve problems such as limited resource network collapse, increased packet loss rate, and reduced network performance, achieving high scalability and portability, increasing network throughput, The effect of suppressing the packet loss rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
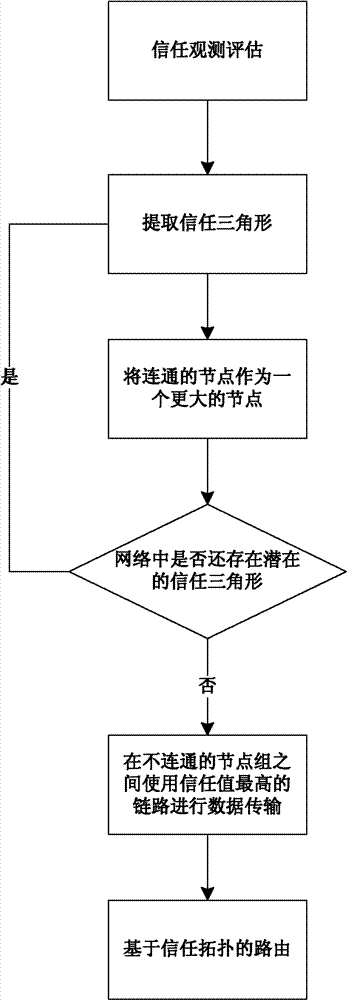
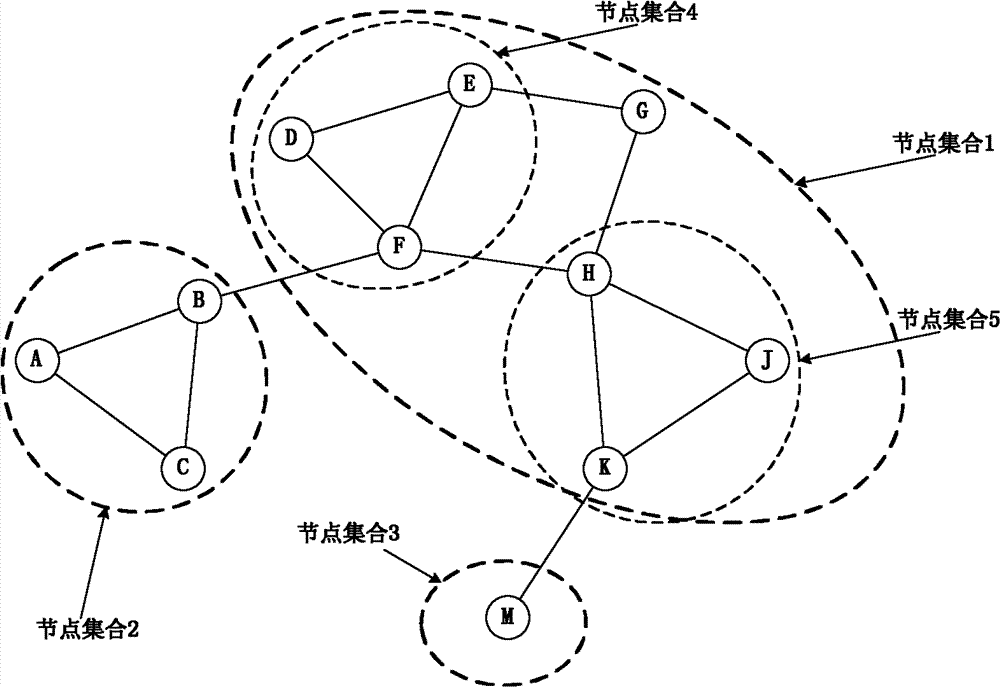
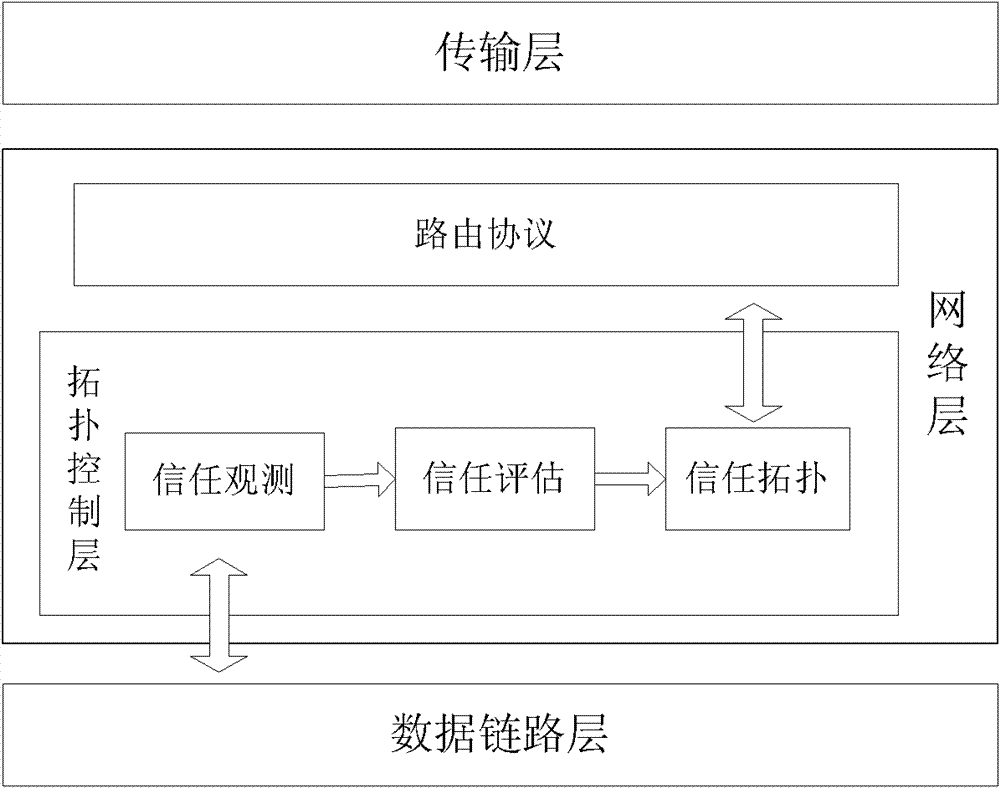
[0014] First, the trustworthiness is introduced: trustworthiness is a quantitative representation of trust. According to the node object, the trust value can be divided into direct trust value and indirect trust value. The direct trust value is the trust value between neighbor nodes, which is obtained through direct observation and calculation of neighbor nodes; the indirect trust value is the trust value between non-neighbor nodes, which needs to be calculated through a certain trust model. The network trust topology in the present invention generates The algorithm only needs to use the direct trust value and the link trust value. The direct trust value t of a node in the link is estimated by its upstream node's trust in completing a specific behavior of the node, and the calculation method is as follows:
[0015] t = μ ( a , b ) = a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com