Website access method and device and filter form downloading and updating method and system
A website access and filtering table technology, applied in the computer field, can solve the problems of poor scalability and high price, and achieve the effect of low expansion cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
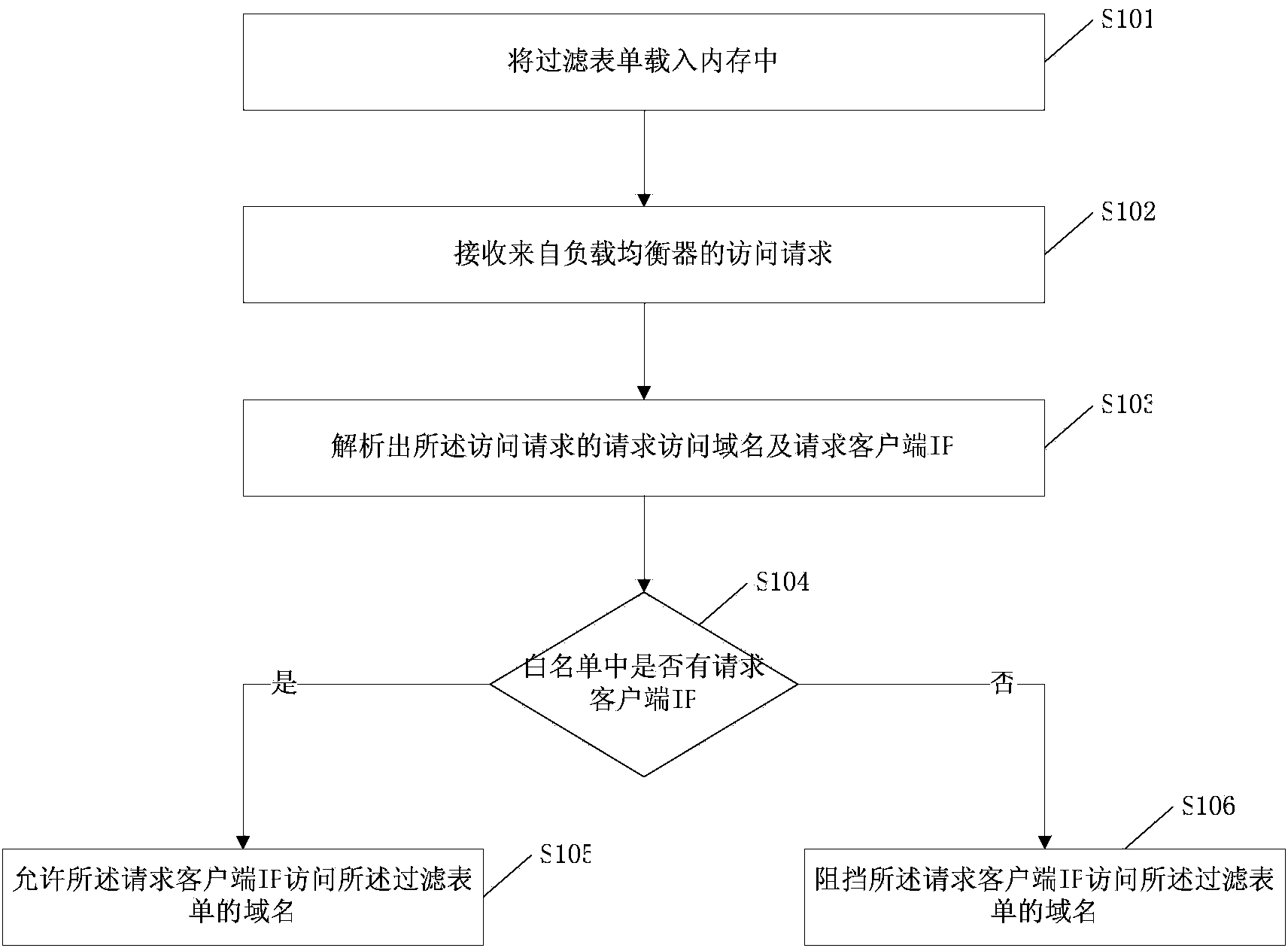
[0051] Such as figure 1 As shown, a website access method, which is applied to the routing component, includes the following steps:
[0052] Step S101 , loading a filter form into memory, the filter form records the correspondence between domain names and whitelists, and the whitelist includes at least one IP address. The content of the filter form is shown in the table below:
[0053]
[0054] Step S102, receiving an access request from the load balancer, that is, an http protocol request.
[0055] Step S103, parsing out the requesting domain name and requesting client IP of the access request.
[0056] Step S104, judging according to the filtering form whether there is the requesting client IP in the whitelist corresponding to the domain name of the filtering form matching the domain name of the access request, if so, performing step S105, otherwise, performing step S105. S016.
[0057] Step S105, allowing the requesting client IP to access the domain name of the filt...
Embodiment 2
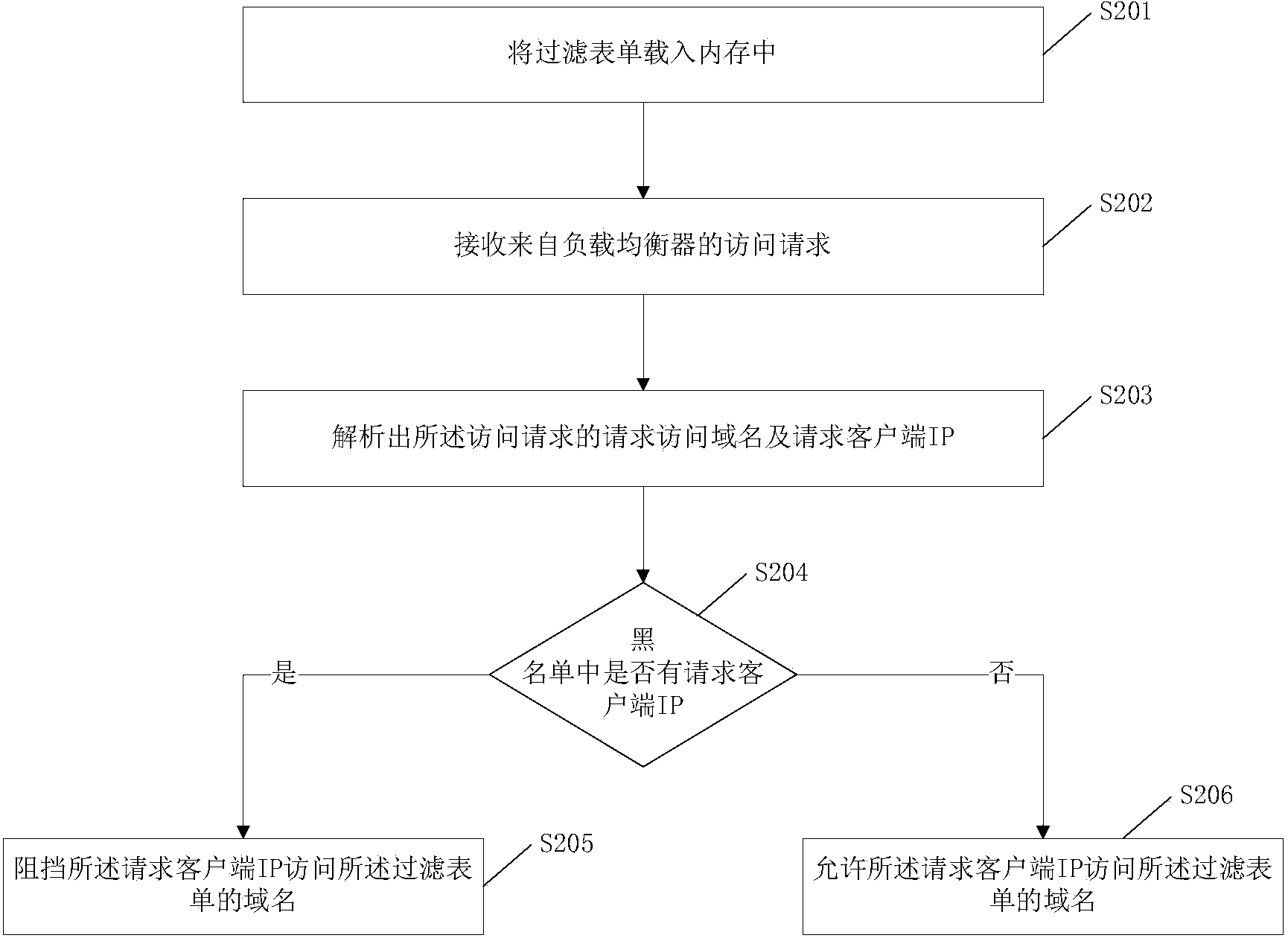
[0065] Such as figure 2 As shown, a website access method, which is applied to the routing component, includes the following steps:
[0066] Step S201 , loading a filter form into memory, the filter form records the correspondence between domain names and blacklists, and the blacklist includes at least one IP address.
[0067] Step S202, receiving an access request from the load balancer;
[0068] Step S203, parsing out the requesting domain name and requesting client IP of the access request;
[0069] Step S204. According to the filtering form, it is judged whether there is the requesting client IP in the blacklist corresponding to the domain name of the filtering form matching the requesting domain name of the access request. If so, perform step S205; otherwise, perform step S206 .
[0070] Step S205, blocking the requesting client IP from accessing the domain name of the filtering form.
[0071] Step S206, allowing the requesting client IP to access the domain name of ...
Embodiment 3
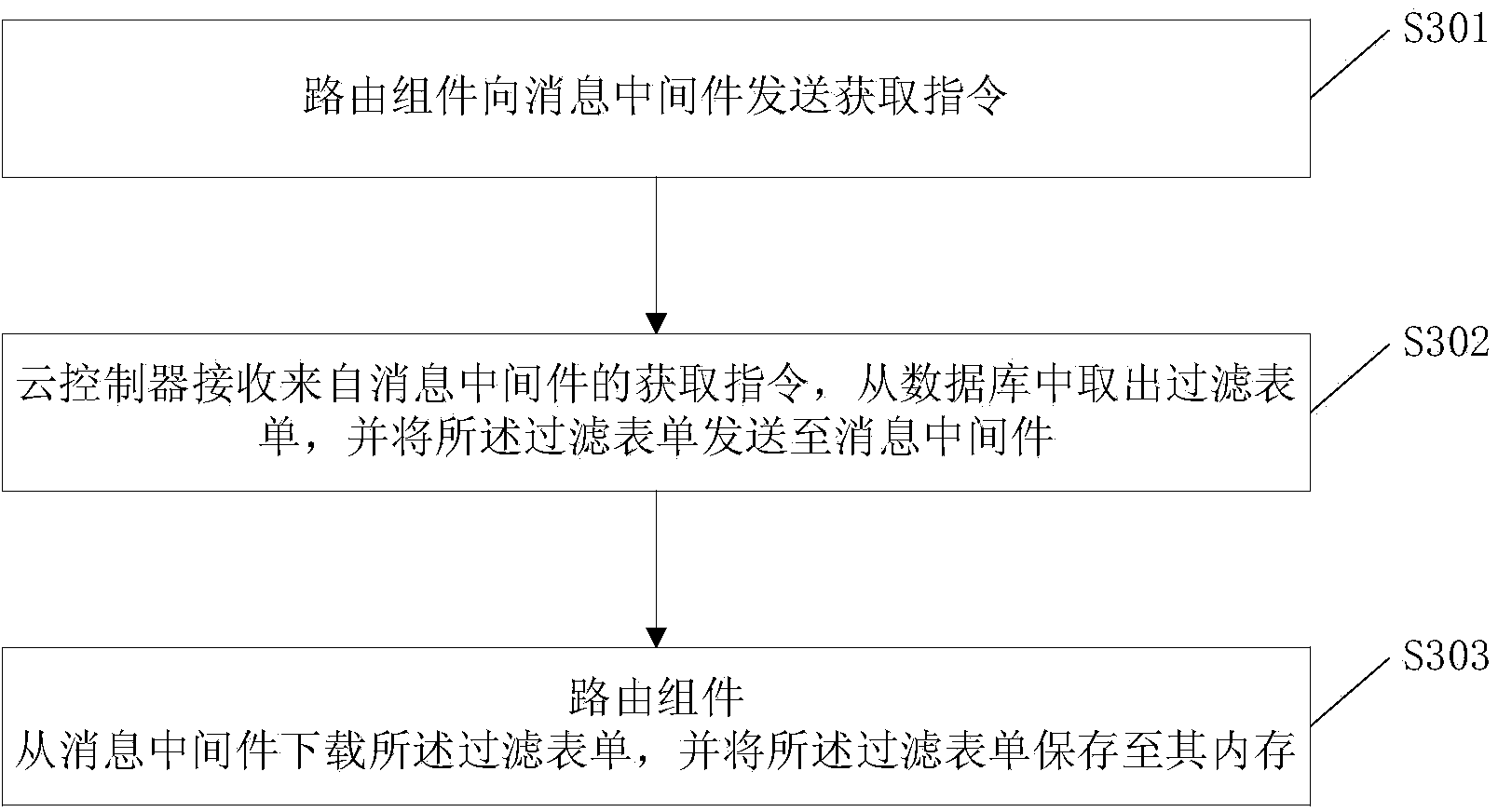
[0078] The method of downloading the filter form of Embodiment 1 or Embodiment 2 is as follows: image 3 As shown, it includes the following steps:
[0079] Step S301, the routing component sends an acquisition instruction to the message middleware.
[0080] Step S302, the cloud controller (CLC, Cloud Controller) receives the acquisition instruction from the message middleware (AM, Active Messenger), fetches the filter form from the database, and sends the filter form to the message middleware.
[0081] Step S303, the routing component downloads the filter form from the message middleware, and saves the filter form to its memory, the filter form records the corresponding relationship between domain names and whitelists or blacklists, and the whitelist or blacklist Include at least one IP address.
[0082] This embodiment also discloses an implementation such as image 3 The filtering form downloading system of the shown method, it comprises the following devices:
[0083] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com